What is the NIST Cybersecurity Framework?
The NIST(National Institute of Standards and Technology) CSF (Cyber Security Framework) is a voluntary framework that provides a cybersecurity approach that organizations can use to identify, assess, and manage cyber risks. The framework is designed to give organizations principles and best practices to improve resilience and security posture regardless of their size, degree of cybersecurity risk, or sophistication. The Cybersecurity Framework covers several topics concerning the security posture of organizations.
These include:
- Cryptography
- Cybersecurity education and workforce development
- Cybersecurity measurement
- Identity & access management
- Privacy engineering
- Risk Management
- Securing emerging technologies
- Trustworthy networks
- Trustworthy platforms
While the cybersecurity framework is not a static document, it has a core structure designed to provide organizations with a proper system of addressing cybersecurity, including its effect on physical, cyber, and people.
NIST Cyber Security Framework Basics are divided into Four sections.
- The Framework Core
- Implementation Tiers
- Framework Profile
- Coordination of Framework Implementation
1. The Framework Core :
The Framework Core is an activity-based guide that organizations can use to achieve a set of outcomes in relation to cybersecurity risk. For example, an organization might need to develop and implement safeguards to protect data in all states. They will use functions within the core to calibrate these safeguards to achieve this goal.
The core is divided into elements such as Functions, categories, subcategories, and informative references.
Function:
These include Identify, Detect, Protect, Respond, Recover, and Govern. They organize cybersecurity activities at their highest level.
Categories:
These allow the breakdown of individual functions into groups of cybersecurity outcomes based on particular activities. For example, organizations looking to protect data in all states will set up protection processes such as “encryption of data-at-rest and in transit” to program the function for desirable outcomes.
Sub Categories:
These represent outcomes of technical or management activities from the category. For example, organizations that have already set up data encryption at rest and in transit could have a result such as “Data was protected in these two states because we implemented encryption policies.”
Informative Reference:
These are specific sections of standards, guidelines, and practices that provide organizations and security teams with methods of achieving outcomes associated with each subcategory. They help organizations understand each subcategory’s requirements and identify the appropriate controls to implement.

Note: Originally, the NIST Cybersecurity Framework had five main functions. However, its last major update includes a new function – Govern, which shows organizations how to make solid decisions regarding their cybersecurity strategy. The function puts cybersecurity alongside other areas, such as legal and finance, as a major source of risk to any organization.
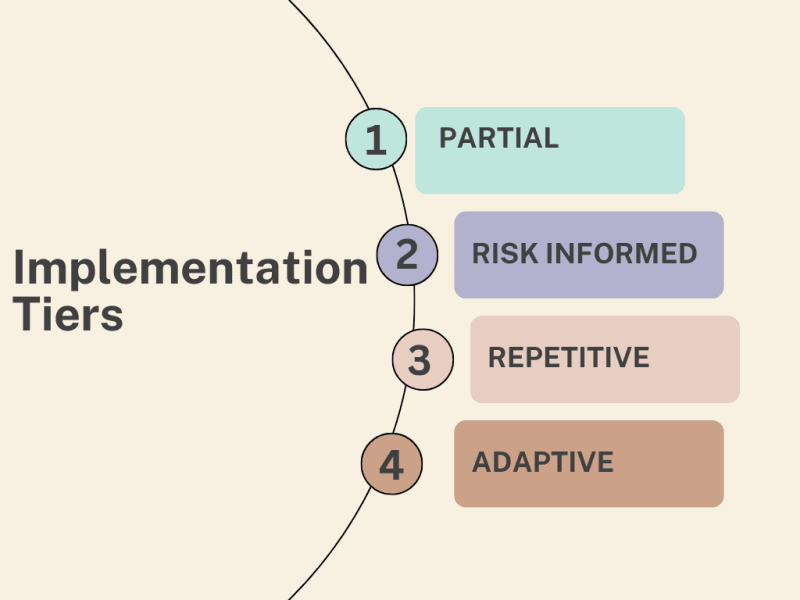
2. Implementation Tiers :
Framework Implementation Tiers (FIT) is a way of measuring how an organization is implementing the NIST Cybersecurity Framework. You can think of tiers as levels in a game. Each game level signifies some improvement and the ability to move up. The tiers range from Tier 1 (Partial) to Tier 4 (Adaptive), with Tier 1 being the lowest level of maturity and Tier 4 being the
highest.
- Tier 1 (Partial): If an organization is at Tier 1, they have just started implementing the NIST CSF. They may have identified some risks and implemented some controls but still need to integrate the CSF into their overall risk management processes fully.
- Tier 2 (Risk Informed): Once the organization has a better understanding of the NIST CSF and begins to integrate it into its overall risk management processes, it moves to Tier 2. At this point, they have identified and prioritized risks and implemented controls appropriate for the level of risk.
- Tier 3 (Repeatable): Organizations at Tier 3 have a repeatable process for implementing and managing cybersecurity controls. They have developed a risk management framework and have implemented controls that properly align with that framework.
- Tier 4 (Adaptive): Organizations at Tier 4 have an adaptive approach to cybersecurity. They constantly monitor and evaluate their risk posture and change their controls. They are also investing in research and development to stay ahead of emerging threats.
3. Framework Profile :
A framework profile allows security teams to determine whether their implementation of the CSF is in tandem with their business requirements. You could compare the framework profile to your medical checkup results. Consider the results that they provide after screening, your health profile.
Organizations can also use the framework profile as a benchmark to see how far off or close they are to achieving their desired security state. This happens by matching two states: the Current State and the Target State.
The current state pertains to how the organization is. On the other hand, the Target State represents where it desires to be. Profiles allow proper communication among all security stakeholders to enable them to allocate the required resources to achieve a higher security state on all levels.
4. Coordination of Framework implementation :
This describes the communication between all organizational stakeholders toward achieving a desirable security state for assets. Implementing this framework will involve players from the organization’s executive, business, and operations.
The executive, such as the CISO, CEO, or CFO, will relay mission priorities, available resources, and overall risk tolerance to the business/process level. The business/process level will then use the information and add it to the risk management process before sharing it with the operations team.
The operations or implementation team then creates a profile and passes the information to the business team. The business level then communicates the findings to the executive and any changes or implementations designed to improve the framework profile.
How to Use the Framework?
Organizations are different; each has its structures for identifying, assessing, and managing cybersecurity risk.
Therefore, some organizations will implement the framework in its entirety, while others will use it to fill in the gaps in their cybersecurity risk approach and develop a roadmap to improvement.
Regardless, be prepared to use the Cybersecurity framework in the following ways:
- Doing a basic review of cybersecurity practices
- Establishing or Improving a cybersecurity program
- Communicating cybersecurity requirements with stakeholders Making buying decisions
- Identifying opportunities for new or revised informative references
- Creating methodology to protect privacy and civil liberties




