As technology continues to advance at a rapid pace, so do the methods used by cyber criminals to breach an organization’s defenses. With Multi-Factor Authentication (MFA) and Privileged Access Management (PAM) solutions touted as the ultimate defense mechanisms, it is easy to believe that your data is safe from prying eyes. But what if I told you that these security measures may not be as impenetrable as you think? In this eye-opening article, we will explore the hidden flaws of MFA and PAM solutions, revealing how even the most well-intentioned protection strategies can fall short when faced with determined hackers seeking privileged access to your critical systems.
Think Your MFA (Multi Factor - Authentication) and PAM (Privileged Access Management) Solutions Protect You? Think Again.
What is "Identity Attack Surface"?
The identity attack surface includes any organizational resource accessed using usernames and passwords. Attackers typically use compromised credentials. Unlike other attack surfaces, attackers can easily gain access using legitimate usernames and passwords.
But I have MFA and PAM in place to prevent attacks:
According to the report, which summarizes findings from 600 identity security professionals surveyed around the world, the vast majority of organizations have MFA and PAM solutions in place yet remain exposed to attacks. Here’s why:
Less than 7% of organizations have MFA protection for the majority of their critical resources.
One of the questions the survey asked was: What proportion of the following resources and access methods are you currently able to protect with MFA?
- Desktop logins (e.g. Windows, Mac)
- VPN and other remote connection methods
- RDP
- Command-line remote access (e.g. PowerShell, PsExec)
- SSH
- Homegrown and legacy apps
- IT infrastructure (e.g. management consoles)
- VDI
- Virtualization platforms and hypervisors (e.g. VMware, Citrix)
- Shared network drives
- OT systems
These numbers imply a critical gap, since a resource without MFA is a resource that an adversary can seamlessly access using compromised credentials. Translating this to a real-life scenario, a threat actor using command-line tool that’s not protected with MFA – such as PsExec or Remote PowerShell – will encounter no obstacles when moving across a network in order to plant a ransomware payload on multiple machines.
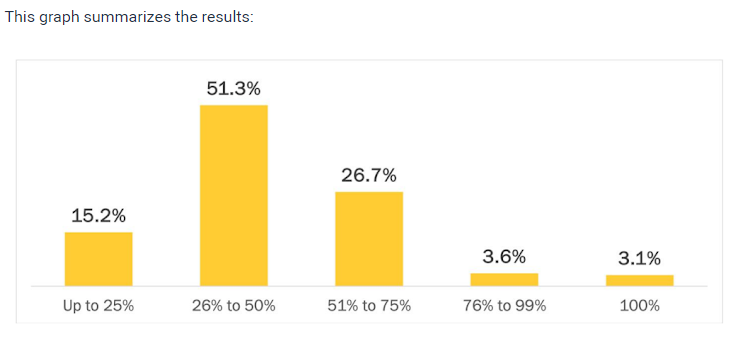
Only 10.2% of organizations have a fully onboarded PAM solution.
PAM solutions are notorious for long, complex deployments, but how bad is it really? The report reveals the answer: It’s bad. Here is an aggregation of respondents’ answers to the question “Where are you in your PAM implementation journey?”

As you can see, most organizations are stuck somewhere along their PAM journey, which means at least some of their privileged users are exposed to attacks. And keep in mind that admin users are an attackers’ fastest path to your crown jewels. Failing to protect all of them is a risk no organization can afford to ignore.
78% of organizations can't prevent malicious access with compromised service accounts
Service accounts are a well-known blind spot. Because these non-human accounts are often highly privileged yet can’t be protected by MFA – as well as the fact that they are typically undocumented and thus unmonitored – they are a prime target for adversaries.
Here are the answers to the question, “How confident are you in your ability to prevent attackers from using service accounts for malicious access in your environment?”

Note that the term “medium” here is a bit misleading, since the absence of real-time prevention essentially voids the security value of being able to detect an account’s compromise.
In conclusion, while MFA and PAM solutions are widely regarded as effective security measures, it is important to recognize their limitations. While they can provide an added layer of protection against unauthorized access and credential theft, they may not be foolproof. Cybercriminals are constantly evolving their tactics and finding ways to bypass these security measures. Therefore, it is crucial for organizations to adopt a multi-faceted approach to cybersecurity that includes regular training of employees, robust monitoring systems, and proactive threat intelligence. Only by staying vigilant and continuously adapting our security strategies can we hope to stay one step ahead of cyber threats. Safeguarding sensitive data and preserving the integrity of our digital infrastructure requires a collective effort from all stakeholders involved.




