No Coding, No Compromise: A Breach Prevention SaaS Security Guide – 2023
With the growing trend of businesses transitioning their operations to cloud-based Software as a Service (SaaS) platforms, ensuring the security of these systems has become of utmost importance.
Cybercriminals become attracted to SaaS platforms because of their convenience for deploying malicious code, and they often store sensitive data.
As more and more companies use no-code SaaS solutions because they are easy and quick to use, it becomes more important to think about the security effects.
A report from Gartner says that by 2024, the SaaS business will bring in $260.63 billion.
DoControl’s 2023 SaaS Security Threat Landscape Report(Download) finds that 50% of enterprises and 75% of mid-market organizations have exposed public SaaS assets.
This significant growth shows that SaaS solutions are becoming more popular, and security risks could grow if handled better.
So, let’s explore why it’s crucial to prioritize SaaS security, how no-code SaaS security will help ensure your SaaS applications and data are safe, and how a leading SaaS security provider, DoControl, can be an effective solution to safeguard against SaaS-based threats.
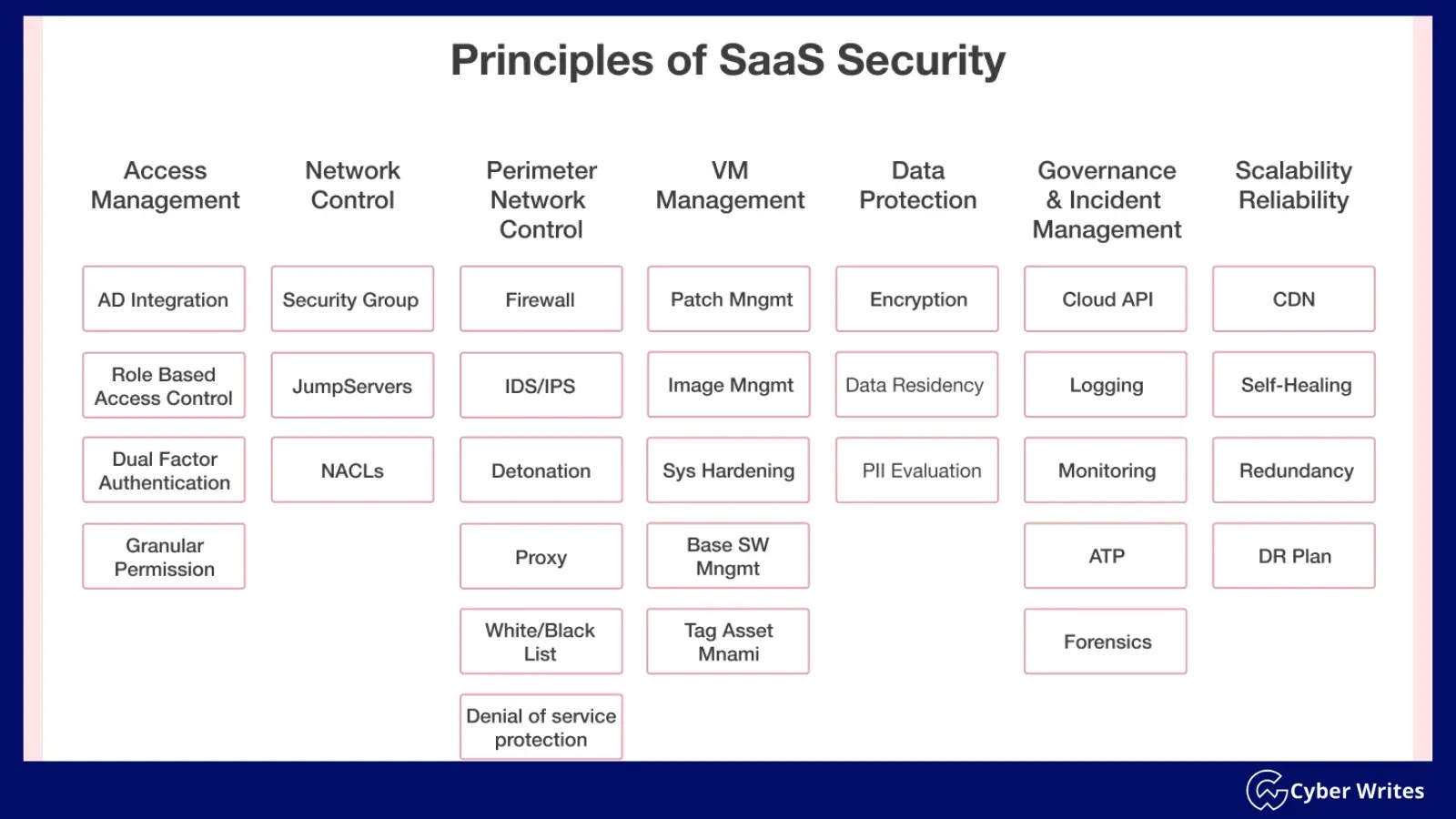
What is No-Code SaaS Security?
No-code SaaS Security is the set of security protocols and measures used to protect apps and data in Software as a Service (SaaS) environments built with no-code platforms.
No-code platforms offer the opportunity to develop applications without coding skills, increasing accessibility to a broader audience.
No-Code SaaS Security implements protections like multi-factor authentication, data encryption, compliance management, regular audits, and real-time monitoring to address SaaS-based security threats.
Importance of SaaS Security
- Data Protection: Sensitive information such as client data, financial records, and intellectual property is frequently stored in SaaS applications. A breach in security could provide unauthorized access to sensitive information and possibly cause harm.
- Compliance and Regulations: Data protection laws like GDPR, HIPAA, and PCI DSS impose strict standards on many businesses. If your SaaS isn’t secure enough, you could face substantial fines and legal penalties for not complying.
- Business Continuity: SaaS programs are vulnerable to cyberattacks like ransomware, which can result in challenging downtime. Zero exposure to these dangers is made accessible by solid SaaS security, which keeps enterprises running effectively.
- Reputation management: If customers and clients lose faith in a company due to a data breach, this could seriously harm its reputation.
- Insider Threats: Strong SaaS security reduces internal threats like employee fraud or unintentional data mismanagement.
Best Practices for No-Code SaaS Security

- Access Control: Everyone should be encouraged to utilize Multi-Factor Authentication (MFA). Follow the Principle of Least Privilege (PoLP) and allow only the essential privileges.
- Data Encryption: Protect data while it is stored, in transit, and processed using robust encryption standards.
- Regular Security Audits: Consistently look for security flaws and suspicious activity in your SaaS applications with regular monitoring and auditing.
- Vendor Risk Assessment: Ensure that no-code platform providers meet the industry’s security standards by conducting effective security audits of their products.
- Secure APIs: If the no-code platform uses APIs to communicate with other services, the APIs should be protected according to industry standards such as OAuth.
- Disaster Recovery: Data should be backed up frequently, and a disaster recovery plan should be evaluated regularly.
- Use Secure Data Connections: Access the SaaS program via secure data transfer methods, such as a virtual private network (VPN).
- Endpoint Security: Ensure a safe and up-to-date network for accessing the SaaS application from any device.
Start protecting your SaaS data in just a few minutes!
With DoControl, you can keep your SaaS applications and data safe and secure by creating workflows tailored to your needs. It’s an easy and efficient way to identify and manage risks. You can mitigate the risk and exposure of your organization’s SaaS applications in just a few simple steps.
Difference Between No-Code and Traditional SaaS Security
| SaaS Operations | No-Code SaaS Security | Traditional SaaS Security |
|---|---|---|
| Development Environment: | It focuses on software developed with no-code platforms, eliminating the need for code in the application development process. This expands access to app creation but poses new issues for screening and protecting apps made by those needing more technical expertise. | It involves software built by programmers who have become familiar with a particular level of security and who employ conventional programming techniques. |
| Risk Profile | It may pose a different kind of risk than more conventional systems since users who aren’t security experts may make mistakes or be unaware of how to implement security measures properly. | Developers with some training or experience in app security write the code. |
| Vendor Dependency: | Since application developers have little control over the underlying infrastructure, they must depend more heavily on the platform provider for security features while working with SaaS. | Traditionally, SaaS security has depended on a combination of vendor-supplied and custom-built security measures to give businesses the most flexibility in determining their level of risk. |
| Customization | However, the no-code platform’s restrictions could make it challenging to customize security settings to individual needs. | As developers have complete access to the source code, they can add whatever security protections are necessary. |
DoControl’s No-code SaaS with Zero Trust
DoControl’s No-Code SaaS with zero-trust security offers a centralized, automated, and risk-aware SaaS Security Platform (SSP) for protecting mission-critical applications and data.
By collaborating with DoControl, the following features will be beneficial to protect your SaaS business from the risks of insider attacks, data breaches, and disruptions in operations.
- Unified Data Access Controls: DoControl uses a centralized system to regulate access to all your data across all your SaaS applications, and high-risk actions and events in SaaS can activate an automated Workflow.
- Prevent Data Loss in SaaS Ecosystems: All files stored in a SaaS service are scanned and identified in real-time for sensitive data categories like PII, PCI, and PHI. Customizable, granular data access regulations that can be applied to any scenario, such as blocking access to certain sensitive data types in specific SaaS environments.
- Cloud Access Security Broker (CASB): Explore the complete SaaS attack surface, evaluate leading threat models, remediate in bulk, and repeat the process automatically.
- Protect SaaS-to-SaaS: DoControl scans and monitors critical SaaS application data activity, performs end-user behavioral analytics to avoid insider threats, and automatically initiates safe procedures to protect sensitive enterprise data.
- Incident Response: Discover all the SaaS apps that integrate into the mainframe, identify the ones that aren’t complying, and give them a risk score to authorize or cancel access to use an application.
Conclusion
Since no-code platforms make application development more accessible by letting non-technical people build software, there is a greater chance that security holes will be made by accident.
A survey by DevSecOps found that 68% of companies say that the speed with which software is deployed makes it harder to maintain security.
Even though no-code settings speed up these cycles even more, they face the same challenges.
To reduce these risks, it is essential to use specialized security strategies like DoControls No Code, Zero Trust models, robust encryption methods, and real-time tracking.
These steps, along with regular audits and employee training, make up a complete approach to no-code SaaS security that can protect sensitive data, stay compliant, and protect the company’s integrity.






