Incident response Tools or incident management software are essential security solutions to protect businesses and enterprises from cyber attacks.
Our reliance on the internet is growing, and so make a threat to businesses, despite increased investments and expertise in cyber security. More data breaches and cyberattacks exist on organizations, governments, and individuals than ever before.
New technologies like Machine Learning, Artificial Intelligence, and 5G, as well as better coordination between hacker groups and state actors, have made threats riskier.
The faster your organization detects and responds to an unauthorized access or IoT security incident, the less likely it is to have a negative impact on the information, customer trust, reputation, and profitability.
What is an Incident Response?
Incident response refers to an organization’s strategy for responding to and managing a cyberattack.
A cyberattack or security violation may lead to chaos, copyright claims, a drain on overall organizational resources and time, and a decline in brand value.
An incident response aims to mitigate damage and speedily return to normalcy. A well-defined incident response plan can restrict attack damage and save money and time after a cyber attack.
Why Incident Response Tools are Important?
Incident response manages the repercussions of an IoT security breach or failure.
Before an incident occurs, it is critical to have a response procedure in place to limit the extent of damage caused by the event and save the organization time and money in the recovery process.
Incident response Tools helps an organization to detect, analyze, manage, and respond to a cyberattack. It helps to reduce the damage and do fast recovery as quickly as possible.
Organizations often use several best incident response tools to detect and mitigate cyberattacks.
Here we have listed some of the most important cyber incident response software widely used with the most sophisticated features.
As you know, the investigation is always required to safeguard your future; you must learn about and prepare for the attack.
Security Incident Response software has to be available for every organization to identify and address exploits, malware, cyberattacks, and other external security threats.
These Incident Response Tools usually work with other traditional security solutions, like firewalls and antivirus, to analyze the attacks before it happens.
To do this appropriately, these tools gather the information from the logs, identity system, endpoints, etc. it also notices suspicious activities in the system.
If we use these best Incident Response Tools it becomes easy for us to monitor, resolve, and identify security issues quickly.
It streamlines the process and eliminates repetitive tasks manually.
Maximum modern tools have multiple capacities to block and detect the threat and even alert the security teams to investigate further issues.
Security terms differ for different areas and completely depend on the organization’s needs. In this case, pleases select the best tool is always challenging, and it also has to give you the right solution.
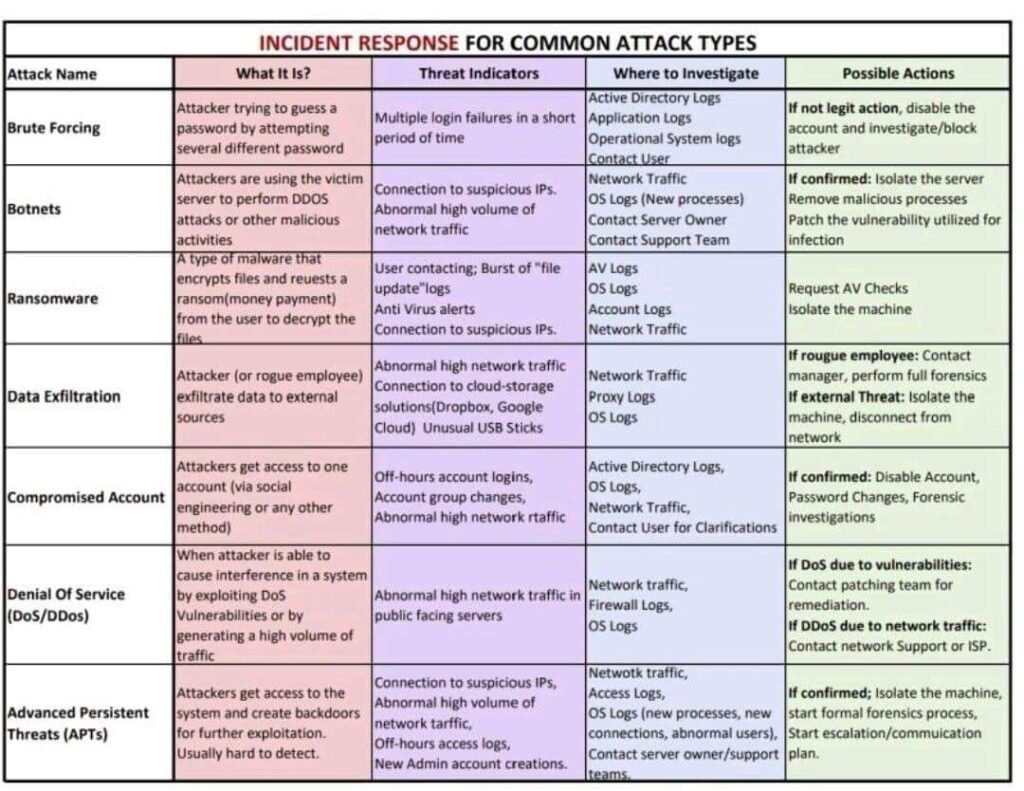
Incident Response Phases
The incident response methods are based on six important steps: preparation, identification, containment, eradication, recovery, and lesson.
| Incident Response Phases | How to Respond |
| Preparation | This will require figuring out the exact members of the response team and the stimulates for internal partner alerts. |
| Identification | This is the process of finding threats and responding effectively and quickly. |
| Containment | After figuring out what to do, the third step is to limit the damage and stop it from spreading. |
| Eradication | This step entails eliminating the threat and restoring internal systems as precisely as possible to their initial state. |
| Recovery | Security experts must ensure that all compromised systems are no longer risky and can be put back online. |
| Lesson | One of the most important and often forgotten steps. The incident response team and its partners get together to talk about how to improve their work in the future. |
In today’s technology-driven society, organizations face increasing security risks that have become unavoidable.
Therefore, the incident response team needs robust incident response tools to overcome and manage security incidents.
So let’s first understand what an incident response tool is and dive deep into the tools.
Why do we use Incident Response Tool?
Even though businesses have a lot of security practices in place, the human factor is still the most important.
According to the annual Verizon Data Breach Investigations Report, over 85% of all breaches are caused by phishing attacks.
IT security professionals must be ready for the worst since 13% of breaches caused by people contain ransomware, and 10% of ransomware attacks cost organizations an average of $1 million. For this reason, organizations should invest in incident response software.
The incident response tools are crucial because they help businesses detect and respond to cyberattacks, manipulates, malware, and other security threats inside and outside the organization in a reasonable timeframe.
Most of today’s incident response software has several features, including the ability to automatically detect and block threats while notifying the appropriate security teams to investigate the issue.
Incident response tools may be used in various ways depending on the organization’s needs.
This could involve monitoring the system and individual nodes, networks, assets, users, etc.
Many organizations find it hard to choose the best incident response software.
To help you find the right solution, here is a list of incident response tools to help you discover, prevent, and deal with different security threats and attacks on your IoT security tools system.
How do We Pick the Best Incident Response Tools?
We analyzed the industry with the requirement to protect digital assets and discussed the respective industries’ needs with the experts based on the following Points.
How effectively are the incident response software performing for the following operations?
- Preparation & Identification
- Containment & Eradication
- Recovery and restoration
- Event False positive Checks
- Identification of incidents
- Containment and quarantine of attackers and incident activity
- Recovery from incidents, including restoration of systems
- Features, Speed, User friendly
- Activities in each phase of incident response
Incident Response Market
| By Security Type | Web Security Application Security Endpoint security Network Security Cloud Security |
| By Deployment Mode | Cloud On-premises |
| By Organization Types | Small Enterprises Medium Enterprises Large Enterprises |
Best Cyber Incident Response Tools List
| Incident Response Tools | Key Features |
|---|---|
| 1.- Manage Engine Log360 | 1. It examines on-premises systems and cloud platforms 2. Logs are consolidated and stored. 3. Use User and Entity Behaviour Analytics (UEBA) to keep track of standard events. 4. The Manage Engine package has other security features like data integrity tracking and a threat intelligence 5. feed that makes threat hunting faster. |
| 2. SolarWinds | 1. User Activity Monitoring. 2. File Integrity Monitoring. 3. Network Security Monitoring. 4. Microsoft IIS Log Analysis. 5. Firewall Security Management. 6. Network Security Tools. 7. Snort IDS Log Analysis. 8. IT DISA STIG Compliance. |
| 3. CrowdStrike Falcon Insight XDR | 1. Unparalleled coverage 2. Speed investigations 3. Threat intel integration 4. 24/7 managed threat hunting 5. Continuous raw events capture 6. proactive threat hunting |
| 4. IBM QRadar | 1. Excellent filtering to produce the desired outcomes 2. Excellent threat-hunting capabilities 3. Netflow analysis 4. Capability to analyze large amounts of data quickly 5. Identify hidden threads 6. Analytics of user behavior |
| 5. Splunk | 1. Query-based historical and current analysis. 2. AI-powered threat detection. 3. It works with Windows, Linux, and macOS. |
| 6. AlienVault | 1. Compatible with Linux and Windows 2. Monitoring of behavior 3. Detection of intrusions |
| 7. LogRhythm | 1. It has a response playbook 2. Automated smart responses 3. Back-end for Elasticsearch that is open source. |
| 8. Varonis | 1. Investigating potential incidents 2. Containment, eradication, and recovery 3. Advice on detections, procedures, and cyber resilience 4. Deep forensics analysis |
| 9. OpenVAS | 1. An Advanced Task Wizard is also included in the OpenVAS web interface. 2. It includes several default scan configurations and allows users to create custom configurations. |
| 10. Rapid7 InsightlDR | 1. Endpoint Detection and Response (EDR) 2. Network Traffic Analysis (NTA) 3. User and Entity Behavior Analytics (UEBA) 4. Cloud and Integrations. 5. Security Information and Event Management (SIEM) 6. Embedded Threat Intelligence. 7. MITRE ATT&CK Alignment. 8. Deception Technology. |
| 11. Snort | 1. Modifications and extensions are feasible. 2. Customized tests and plugins are supported |
| 12. Suricata | 1. It supports JSON output 2. It supports Lua scripting 3. Support for pcap (packet capture) 4. This tool permits multiple integrations. |
| 13. Nagios | 1. It is simple to identify network issues and provide security and scalability. 2. It also helps with keeping track of logs and databases. 3. It has an easy-to-use and informative web interface that makes it easy to monitor a network. |
| 14. Sumo Logic | 1. Monitor & troubleshoot 2. Integrate real-time threat intelligence 3. Monitor & troubleshoot 4. integrated logs, metrics, and traces 5. Quickly detect applications & Incidents |
| 15. Dynatrace | 1. Full stack availability and performance monitoring 2. Easy monitoring with no configuration 3. Automated Incident Management4. 4. AWS Monitoring 5. Azure Monitoring 6. Kubernetes Monitoring |






