Rockwell Automation Devices Flaw Let Hackers Gain Unauthorized Access
A critical security vulnerability in Rockwell Automation’s ControlLogix and GuardLogix controllers has been discovered. This vulnerability could potentially allow attackers to bypass security measures and gain unauthorized access to industrial control systems.
Researchers at Claroty’s Team82 uncovered the flaw, which is identified as CVE-2024-6242. It affected various models of Rockwell’s 1756 ControlLogix devices.
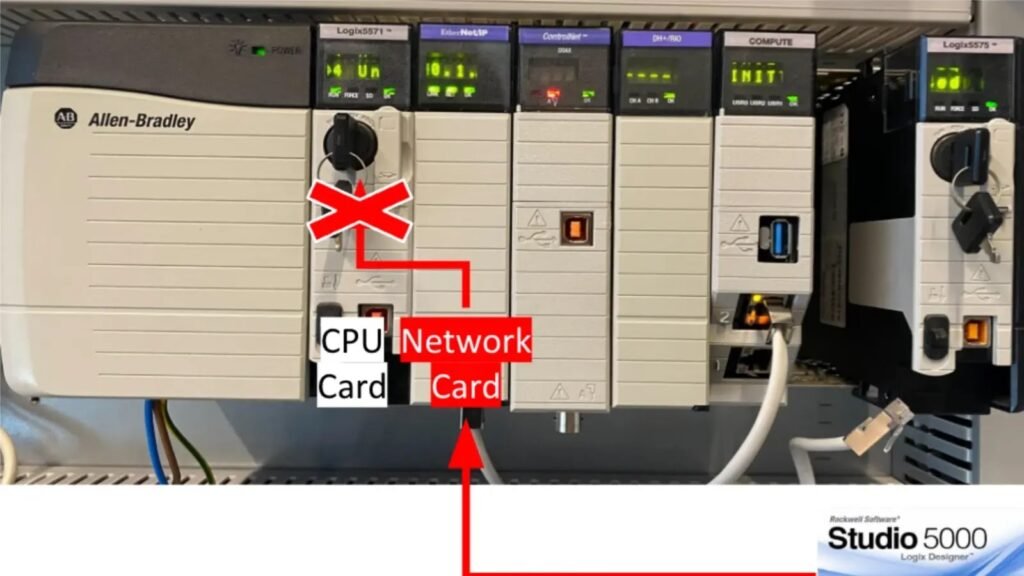
The vulnerability, which carries a CVSS v3.1 base score of 8.4, enables attackers to circumvent the “trusted slot” feature in ControlLogix controllers. This security mechanism is designed to enforce policies within the ControlLogix chassis, ensuring that only authorized slots can communicate with each other.
However, the discovered flaw allows malicious actors to “jump” between local backplane slots within a 1756 chassis using CIP (Common Industrial Protocol) routing, effectively traversing the security boundary to protect the CPU from untrusted cards.

Exploiting this vulnerability could allow an attacker with network access to the device to send elevated commands to the PLC CPU, such as downloading logic or modifying user projects and device configurations. This poses a significant risk to industrial environments where these controllers are deployed.
The affected products include:
- ControlLogix 5580 (1756-L8z)
- GuardLogix 5580 (1756-L8zS)
- 1756-EN4TR
- Various models of 1756-EN2T, 1756-EN2F, 1756-EN2TR, and 1756-EN3TR
Rockwell Automation has released firmware updates to address the vulnerability. Users are strongly advised to update their devices to the manufacturer’s latest firmware versions.
Rockwell recommends limiting allowed CIP commands on controllers by setting the mode switch to the RUN position as a mitigation measure for those unable to immediately update.
To aid in detecting potential exploitation attempts, Claroty has released a Snort rule designed to identify suspicious CIP Forward Open Requests that may indicate attempts to bypass the local chassis security.
Organizations using affected Rockwell Automation devices are urged to assess their risk exposure and implement the necessary updates and mitigations to protect their systems from potential attacks.
As industrial systems become increasingly connected, vulnerabilities like CVE-2024-6242 underscore the need for robust security measures and continuous monitoring in operational technology (OT) environments to safeguard against cyber threats targeting critical infrastructure.