What is Bridge in Computer Network? Types, Uses & Functions
In computer networks, various devices work together in computer networks to ensure seamless communication between network segments. The bridge plays a crucial role among these devices.
This article delves into the intricacies of bridges in cybersecurity, exploring their types, functions, advantages, disadvantages, and applications.
By the end of this comprehensive guide, you’ll have a thorough understanding of how bridges operate and their significance in modern networks.
What is a Bridge in Computer Networks?
A bridge is a networking device used to connect multiple Local Area Networks (LANs) into a larger LAN. Operating at the data link layer of the OSI model (Layer 2), bridges are sometimes referred to as Layer 2 switches.
Their primary function is to filter and forward data packets based on MAC addresses, effectively dividing network connections into segments with separate bandwidth and collision domains.
This segmentation enhances network performance by reducing traffic congestion and improving data flow efficiency.
Types of Bridges
Bridges come in various types, each designed for specific networking scenarios. The main types include:
- Transparent Bridge
Transparent bridges are so named because they are invisible to other devices on the network. They do not require configuration changes when devices are added or removed from the network.
The primary function of a transparent bridge is to block or forward data packets based on MAC addresses.
By learning the MAC addresses of devices on each network segment, transparent bridges can efficiently manage data traffic without user intervention.
- Source Routing Bridge
Developed by IBM for token ring networks, source routing bridges embed the entire route within the data frames. The source station determines the path the frame must follow to reach its destination.
This approach ensures that frames follow a specific route, which can benefit networks that require precise control over data paths.
- Translational Bridge
Translational bridges serve as intermediaries between different types of networking systems. They convert data from one system to another, enabling communication between disparate network technologies.
For example, a translational bridge might facilitate data transfer between a token ring network and an Ethernet network by translating the protocols used by each.
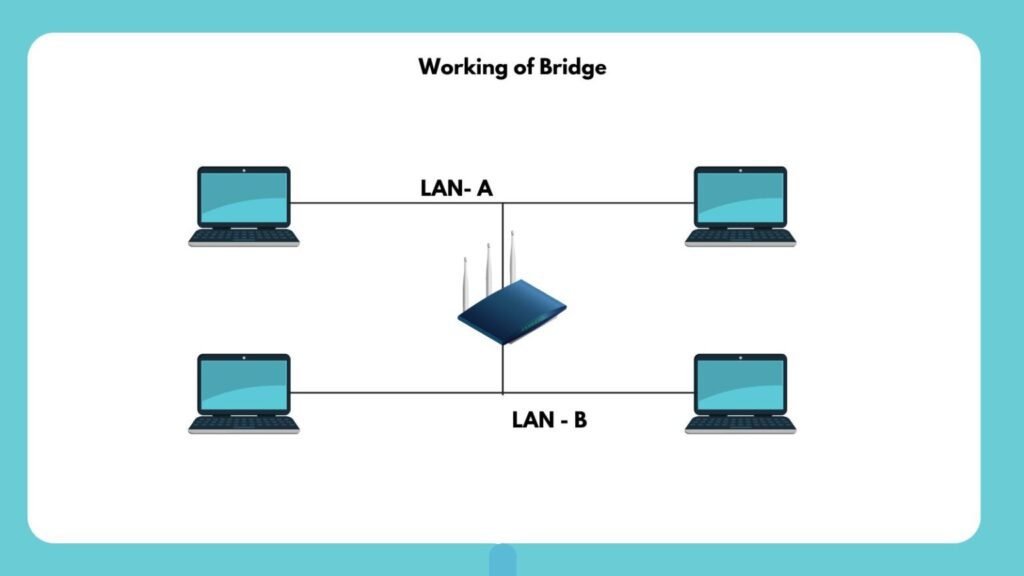
Working of Bridges

Understanding how bridges operate is essential for appreciating their role in network management. Here’s a step-by-step breakdown of their functioning:
- Receiving Data: Bridges receive data packets (frames) from connected network segments.
- Building a Table: They create a table of MAC addresses by observing incoming traffic, mapping which device resides on which segment.
- Filtering Data: If a packet from one segment is intended for another device on the same segment, the bridge filters it out, preventing unnecessary traffic on other segments.
- Forwarding Data: If a packet is meant for a device on a different segment, the bridge forwards it to the appropriate destination.
- Repeating for Both Sides: This process occurs bidirectionally, ensuring efficient data flow across all connected segments.
Models of Bridging
Bridges can be implemented using different models depending on geographical and infrastructural requirements:
- Local Bridging
Local bridging involves connecting LAN switches using local cables. This model allows devices on the same Ethernet segment to communicate directly at the link layer, facilitating seamless interaction within the exact physical location.
- Remote Bridging
Remote bridging connects two or more LANs over a Wide Area Network (WAN). This model is ideal for organizations with geographically dispersed offices that must maintain cohesive communication at the link layer despite physical distances.
Uses of Bridges in Computer Networks
Bridges offer several benefits and functionalities within computer networks:
- Network Capacity Enhancement: Bridges increase overall network capacity by integrating multiple LANs.
- Data Filtering: Bridges use databases to decide whether to accept or reject incoming data frames.
- Broadcasting Capability: Bridges can broadcast data across segments even if destination addresses are unavailable.
- Fault Tolerance: Bridges forward packets even when specific nodes are faulty.
- Traffic Management: They control traffic flow by filtering based on MAC addresses.
Functions of Bridges
Bridges perform several key functions that contribute to efficient network management:
- Segmentation: They divide LANs into multiple segments to optimize performance.
- Traffic Control: By managing data flow based on MAC addresses, bridges help control network traffic.
- Interconnection: Bridges can connect two LANs using similar protocols.
- Data Filtering: They filter data based on destination or MAC addresses to ensure efficient routing.
Advantages of Using Bridges
Bridges offer numerous advantages that make them valuable components in networking:
- Network Extension: Bridges can connect different network topologies, extending the reach of existing networks.
- Increased Bandwidth: By creating separate collision domains, bridges enhance available bandwidth.
- Protocol Transparency: They offer higher protocol transparency compared to other devices.
- Reliability and Maintainability: Bridges are highly reliable and easy to maintain.
- Simple Installation: No additional hardware or software is required beyond the bridge.
Disadvantages of Using Bridges
Despite their benefits, bridges also have some drawbacks:
- Cost: Bridges can be more expensive than simpler devices like hubs and repeaters.
- Speed Limitations: They may introduce latency due to additional processing required for MAC address filtering.
- Performance Issues: Bulk or broadcast traffic can lead to performance degradation.
- Broadcast Storms: High levels of broadcast traffic can result in broadcast storms that disrupt network operations.
Differences Between Bridges and Gateways
While both bridges and gateways connect different networks, they serve distinct purposes:
- Functionality: Bridges operate at Layer 2 (data link layer) and focus on filtering and forwarding based on MAC addresses. Gateways operate at higher layers (often Layer 3 or above) and translate different network protocols.
- Complexity: Gateways are generally more complex than bridges as they handle protocol conversions across different networking systems.
- Use Cases: Bridges are ideal for connecting similar networks within an organization, while gateways connect dissimilar networks or systems with different protocols.
Applications of Bridges in Networking
Bridges find applications in various networking scenarios:
- Enterprise Networks: Large organizations use bridges to manage internal traffic efficiently across multiple departments or floors.
- Campus Networks: Educational institutions employ bridges to connect different buildings or facilities within a campus.
- Data Centers: In data centers, bridges help manage traffic between servers and storage systems across segmented networks.
- Home Networks: Advanced home networks may use bridges to extend connectivity between different parts of a house or property.
Bridges are essential in modern computer networks, connecting multiple LANs into cohesive units.
They enhance performance through efficient data filtering and forwarding while offering flexibility through transparent, source routing, and translational bridges.
Despite some limitations in speed and cost, their advantages make them indispensable tools for managing complex networks.
Understanding how bridges operate helps organizations optimize their infrastructure for better communication and connectivity across diverse environments.
In enterprise settings or home networks, bridges are vital to ensuring robust and efficient network operations.