Microsoft Integrates Azure Firewall with Azure Standard Load Balancer to Boost Security
Microsoft Integrates Azure Firewall with Azure Standard Load Balancer to Boost Security
Microsoft Azure has unveiled new integration capabilities between Azure Firewall and Azure Standard Load Balancer, enabling users to create more robust and secure network architectures.
Whether you opt for a public or internal load balancer, this integration provides flexibility to meet your organization’s connectivity and security needs.
Microsoft offers guidance to mitigate challenges with the public load balancer, particularly issues such as asymmetric routing, while recommending the internal load balancer scenario for its simplicity.
Let’s take a closer look at the two scenarios, the challenges they present, and how to incorporate extra layers of security into your setup.
Public Load Balancer Integration
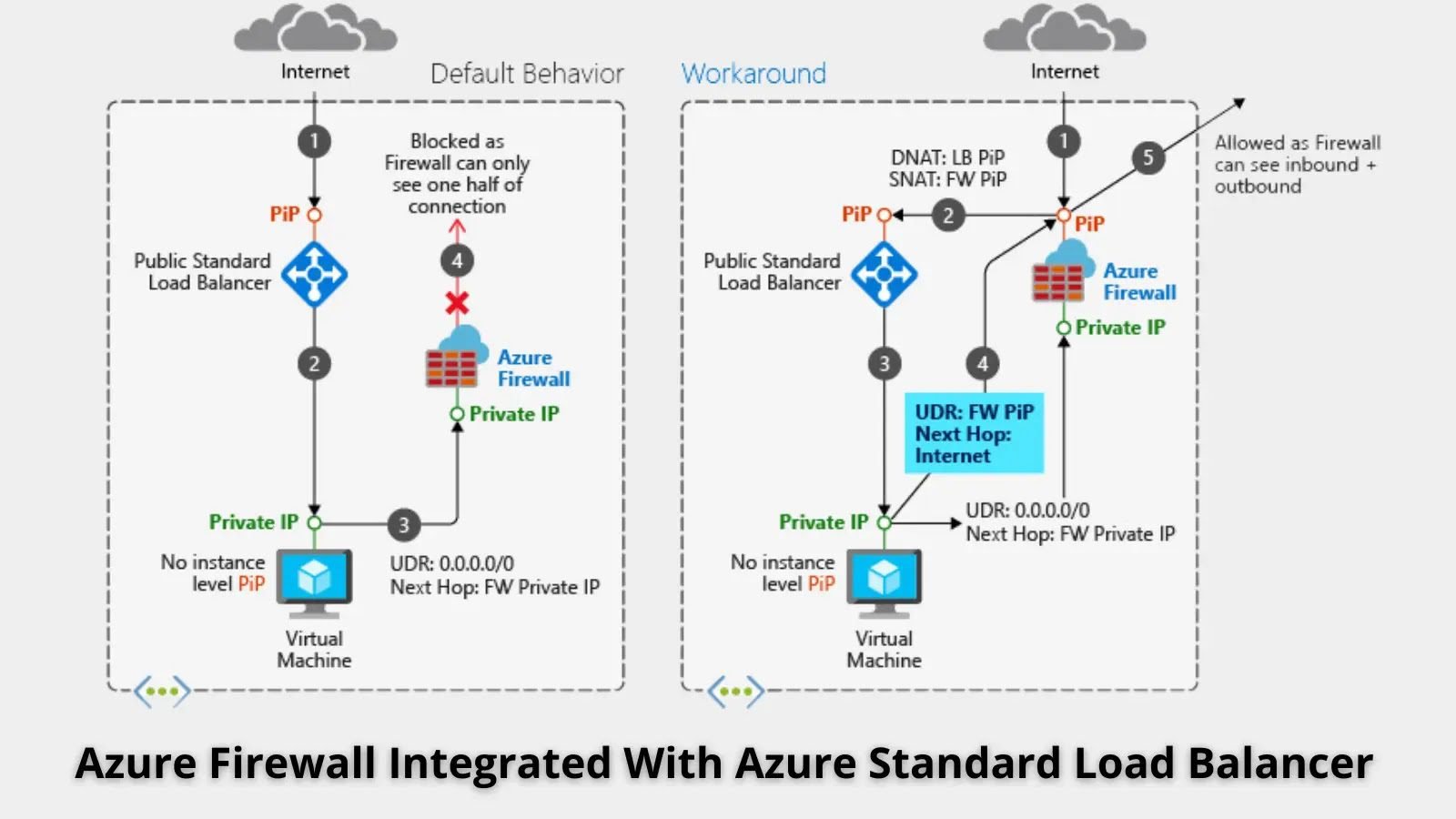
In this approach, the Azure Standard Load Balancer is deployed with a public frontend IP address, facilitating inbound traffic. However, using a public load balancer alongside Azure Firewall introduces the challenge of asymmetric routing.
Asymmetric routing occurs when network traffic takes different paths during its inbound and outbound journeys. This is problematic with Azure Firewall because its stateful design expects traffic to follow the same path in both directions. For example:
- Incoming packets arrive at the public IP address of the load balancer.
- Outbound packets, however, take the default route via the firewall’s private IP address.
Since the firewall cannot match the returning packets with an active session, it drops these packets, disrupting the connection.
Solution to Asymmetric Routing
To address this issue, Microsoft recommends introducing a route table entry to ensure proper packet routing. Here’s the process:
- Default Route: When deploying Azure Firewall into a subnet, create a default route directing packets to the firewall’s private IP address on the AzureFirewallSubnet.
- Host Route for Public IP: Create an additional route for the firewall’s public IP address. Packets destined for the public IP address should bypass the default route and instead be routed through the Internet. This ensures that the firewall processes traffic seamlessly.
Example:
- Firewall public IP:
203.0.113.136 - Firewall private IP:
10.0.1.4
The route table ensures that packets destined for 203.0.113.136 are routed via the Internet, not through the private IP.In a typical setup, you might add a NAT rule to translate incoming traffic. For example, Remote Desktop Protocol (RDP) traffic targeting the firewall’s public IP (203.0.113.136) can be forwarded to the load balancer’s public IP (203.0.113.220).
To ensure load-balancer health probes work effectively, ensure a web service is running on hosts in your backend pool. For TCP health probes, configure port 80, or use HTTP/HTTPS as needed.
Internal Load Balancer Integration
The internal load balancer scenario offers a smoother integration with Azure Firewall. Unlike the public load balancer, it avoids asymmetric routing issues completely. Here’s how:
- The load balancer uses a private frontend IP address.
- Incoming traffic arrives at the firewall’s public IP address.
- The firewall applies its rules and translates the packets to the load balancer’s private IP address.
- Outbound traffic from the backend hosts returns to the firewall via its private IP address, maintaining a consistent routing path.
For outbound Internet access, configure user-defined routes (UDRs) on the virtual machines’ subnet. These routes should point to the firewall as the next hop.
Enhancing Security with Network Security Groups (NSGs)
To further bolster your network security, consider adding Network Security Groups (NSGs) to your load-balanced setup. NSGs allow you to define inbound and outbound traffic rules for specific subnets or virtual machines. For instance:
- Deploy an NSG on the backend subnet hosting your load-balanced resources.
- Configure rules to permit only traffic originating from the firewall’s IP address and designated ports.
By integrating Azure Firewall with Azure Standard Load Balancer, businesses can achieve a secure and scalable network infrastructure tailored to their requirements. Whether leveraging the simplicity of an internal load balancer or optimizing a public load balancer setup, Azure provides the tools and guidance to succeed.