Unveiling the Secrets of Cloud Security Layers
Cloud security is a critical aspect of modern computing, considering the widespread adoption of cloud services for data storage, processing, and application deployment. Cloud security involves a multi-layered approach to protect data, applications, and infrastructure hosted in the cloud. Here are the key layers of cloud security:
- Physical Security:
- Physical security is the foundation of cloud security. Cloud service providers (CSPs) invest heavily in securing their data centers.
- Access to data centers is restricted and monitored with strict entry controls, biometric authentication, and surveillance systems.
- Redundant power supplies, environmental controls, and fire detection and suppression systems are in place to ensure the physical safety of the infrastructure.
- Network Security:
- Network security focuses on protecting the flow of data between servers, devices, and users within the cloud environment.
- Firewalls, intrusion detection and prevention systems (IDPS), and virtual private networks (VPNs) are implemented to monitor and control network traffic.
- Segmentation and isolation of networks prevent unauthorized access and lateral movement of threats within the cloud environment.
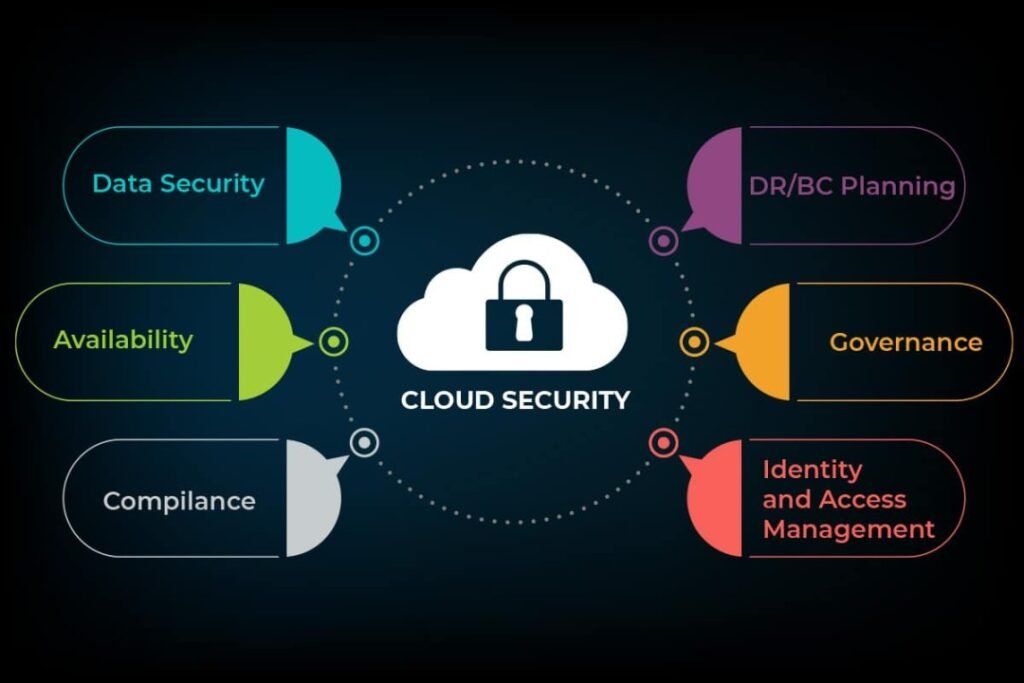
- Identity and Access Management (IAM):
- IAM ensures that only authorized individuals or systems can access resources in the cloud environment.
- Multi-factor authentication (MFA), strong password policies, and identity verification mechanisms help secure user access.
- Role-based access control (RBAC) defines and restricts permissions based on job responsibilities, reducing the risk of unauthorized access.
- Data Encryption:
- Encryption is used to protect data both in transit and at rest. SSL/TLS protocols secure data in transit, while encryption algorithms secure data stored in databases or on storage devices.
- Cloud providers often offer encryption services, allowing users to manage their encryption keys or opt for a fully managed key service.
- Application Security:
- Application security involves securing the code and runtime environment of applications deployed in the cloud.
- Regular security audits, code reviews, and vulnerability assessments help identify and mitigate potential security risks.
- Web application firewalls (WAFs) protect against common web application attacks, such as SQL injection and cross-site scripting (XSS).
- Security Monitoring and Incident Response:
- Continuous monitoring of cloud environments helps detect and respond to security incidents promptly.
- Security information and event management (SIEM) systems, log analysis, and real-time alerts contribute to proactive threat detection.
- Incident response plans outline the steps to be taken in the event of a security breach, ensuring a quick and effective response.
- Compliance and Governance:
- Compliance with industry regulations and standards is crucial in cloud security. Cloud providers often adhere to various compliance frameworks, and users must ensure their configurations and practices comply with applicable regulations.
- Governance policies and frameworks help organizations establish and enforce security policies, ensuring a consistent and secure cloud environment.
- Security Automation:
- Automation of security processes helps in managing the dynamic nature of cloud environments efficiently.
- Security automation tools can detect and respond to threats in real time, ensuring a rapid and consistent security posture.
- Supply Chain Security:
- Supply chain security involves assessing and securing the entire supply chain, including third-party vendors and services.
- Organizations need to vet the security practices of their cloud service providers and other third-party partners to ensure a comprehensive security posture.
By combining these layers of security, organizations can create a robust and resilient defense against a wide range of cyber threats in the cloud. Regular updates, security training, and a proactive approach to emerging threats are essential for maintaining a secure cloud environment.