In an increasingly interconnected world, the threat of cyberattacks looms larger than ever before. With each passing day, hackers are becoming more sophisticated in their methods, targeting unsuspecting victims with ruthless precision. The latest trend in this malicious underworld involves hackers infiltrating MSSQL servers, a popular database management system, to deploy ransomware – a form of digital extortion that holds valuable data hostage until a ransom is paid. This alarming development has sent shockwaves throughout the cybersecurity community and raised urgent concerns about the vulnerability of businesses and individuals alike. As we delve into the details of these attacks and explore potential countermeasures, it becomes clear that proactive action must be taken to safeguard our digital assets from falling prey to this insidious threat.
Hackers attacking MSSQL(Microsoft SQL) Servers to deploy the Ransomware
Recently, threat actors have been utilizing brute force attacks to compromise exposed MSSQL databases to distribute the Free World ransomware. This attack campaign, dubbed DB#JAMMER, is notable, according to Securonix Threat Labs, for the way its infrastructure and toolkit are used. The Free World is a more recent version of Mimic ransomware. The FreeWorld text appeared in binary file names as well as ransomware extensions.
“Threat actors targeted an MSSQL server and were able to gain a code execution foothold on the host using the enabled xp_cmdshell function present on the server,” researchers said. Upon exploitation, the attackers started enumerating the system, issuing shell commands to weaken security, and deploying tools that let them stay persistent on the host.
How the Attack is Carried out?
By brute forcing an MSSQL login, the threat actors got into the target host. After successfully establishing a connection, they immediately scanned the database for other login credentials.
After learning that the MSSQL function xp_cmdshell stored procedure was enabled, the attackers then started executing shell commands on the system. This function, which allows the execution of orders, should typically not be activated until necessary. The attackers carried out various operations on the host, including user creation and modification and registry alterations.
Reports say that the commands were executed in fast sequence, indicating that they were most likely copying them from their end’s tool list or document. Three new users—Windows, adminv$, and mediaadmin$—were created on the victim host. Each user was added to the “administrators” and “remote desktop users” lists. Weirdly, the attackers tried to run a lengthy one-liner to create users and change group membership. Still, many iterations of the command were run to account for groups in different languages.
Many of the system defenses, particularly those related to network security and RDP authentications, have been turned off by the attackers. Attackers connected to a remote SMB share to move tools in and out. Using the network share, the attacker installed malicious tools like cobalt strike and moved files to and from the victim’s PC. For the eventual dissemination of the FreeWorld ransomware through the AnyDesk software distribution, but not before performing a lateral movement step. Additionally, it is claimed that the unidentified attackers tried unsuccessfully using Ngrok to create RDP persistence.
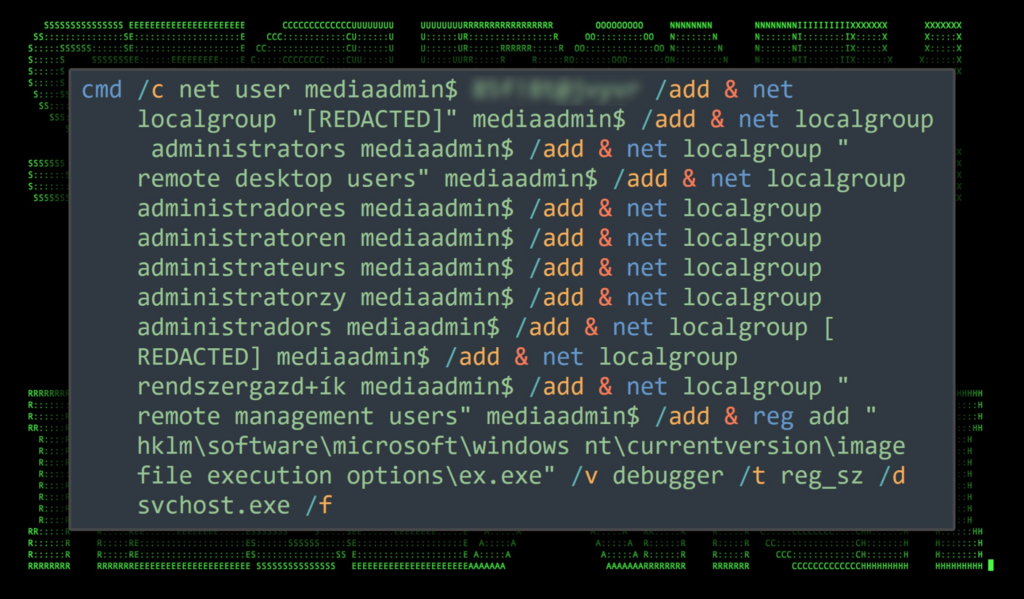
As a result, according to researchers, it was unclear if the attackers were making random or dictionary-based password spray attempts.
The significance of using strong passwords, especially for services accessible to the general public, must be emphasized.
In conclusion, the rise in attacks on MSSQL servers to deploy ransomware is a concerning trend that highlights the urgent need for increased cybersecurity measures. The vulnerabilities in these servers make them an attractive target for hackers seeking to exploit sensitive data and extort organizations for financial gain. It is crucial for businesses and individuals alike to prioritize the implementation of strong security protocols, such as regular software updates and patching, strong passwords, and multi-factor authentication. Additionally, maintaining up-to-date backups of critical data can provide an extra layer of protection against ransomware attacks. By taking proactive steps to safeguard their systems and networks, organizations can mitigate the risk of falling victim to these malicious cyberattacks and protect their valuable assets.




