What is the Difference Between ISO 27001 & 27002 Compliance? – A Detailed Guide
ISO 27001 and ISO 27002 are international standards that provide a framework for managing information security within an organization.
In an increasingly interconnected world, where organizations rely heavily on technology and digital systems, safeguarding sensitive information and maintaining robust security measures is paramount.
Perimeter81 Providers ISO 27001 and ISO 27002 compliance offer a systematic approach to identifying, implementing, monitoring, and continually improving an organization’s information security management system (ISMS).
By achieving compliance, organizations demonstrate their commitment to protecting sensitive information, mitigating risks, and maintaining their digital assets’ confidentiality, integrity, and availability.
This short guide explores the significance of ISO 27001 and ISO 27002 compliance in managing IT security and highlights its benefits to organizations in today’s digital landscape.
Here You can read the best compliance management software 2023.
What is ISO 27001?

ISO 27001 is an international standard that stipulates the requirements for establishing, implementing, maintaining, and continuously improving an organization’s Information Security Management System (ISMS).
It is published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
ISO 27001 provides a framework for systematically managing and protecting sensitive information, including data, processes, systems, and infrastructure.
The primary objective of ISO 27001 is to help organizations establish a comprehensive and risk-based approach to information security.
It provides a systematic methodology for identifying and assessing information security risks, implementing appropriate controls to mitigate those risks, and continually monitoring and improving the effectiveness of the ISMS.
ISO 27001 takes a comprehensive approach to information security, encompassing various aspects such as organizational policies, procedures, people, technology, and physical security.
It sets out requirements that organizations must meet to achieve certification, ensuring they have implemented a robust and well-documented ISMS that aligns with international best practices.
The key benefits of implementing ISO 27001 include the following:
- Risk management: ISO 27001 helps organizations identify and prioritize information security risks, enabling them to allocate resources effectively to mitigate those risks and protect their critical assets.
- Compliance: ISO 27001 assists organizations in meeting legal, regulatory, and statutory requirements related to information security, ensuring they operate within the boundaries of applicable laws and regulations.
- Stakeholder confidence: Achieving ISO 27001 certification enhances the trust and confidence of stakeholders, including customers, partners, and shareholders, as it demonstrates the organization’s commitment to protecting sensitive information.
- Continual improvement: ISO 27001 promotes a culture of continual improvement by establishing a framework for regularly monitoring and evaluating the effectiveness of the ISMS. This allows organizations to adapt to evolving threats and vulnerabilities and enhance their overall security posture over time.
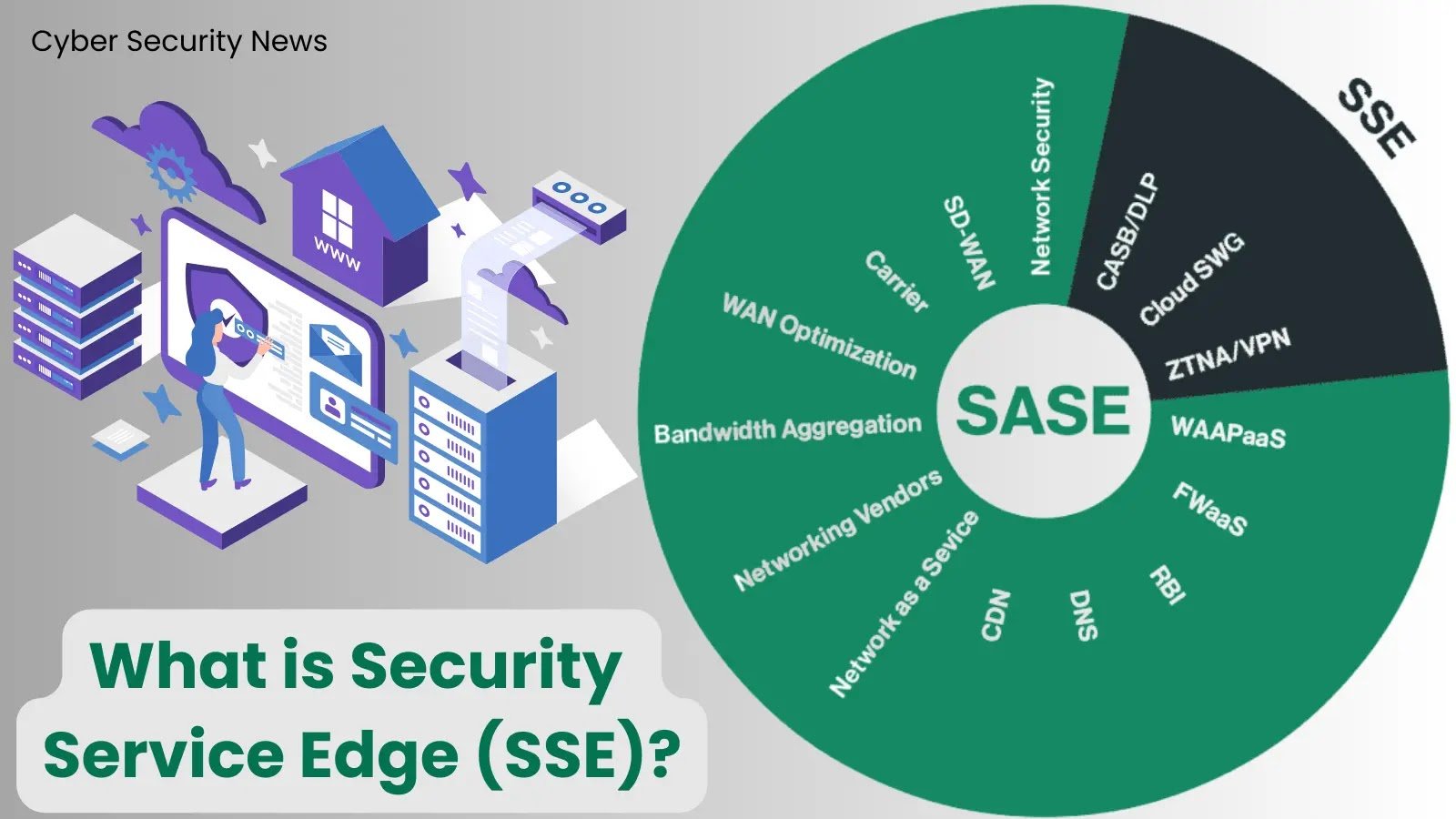
What is ISO 27002?
 ISO 27002 inforgraphics
ISO 27002 inforgraphics
ISO 27002, also known as ISO/IEC 27002:2013, is an international standard for establishing, carrying out, upholding, and enhancing an Information Security Management System (ISMS).
It provides an exhaustive set of controls and measures organizations can implement to ensure their information assets’ confidentiality, integrity, and availability.
ISO 27002 serves as a companion document to ISO 27001, which outlines the requirements for establishing an ISMS.
While ISO 27001 focuses on the overall management system and risk assessment, ISO 27002 delves into the specific controls organizations can implement to address information security risks identified during risk assessment.
Implementing ISO 27002 from Perimeter81 brings several benefits to organizations regarding information security management. Some key benefits include:
- Comprehensive guidance: ISO 27002 provides complete guidelines and best practices for implementing information security controls. By following these guidelines, organizations can ensure that they have addressed critical security areas and have a well-rounded approach to protecting their information assets.
- Risk-based approach: ISO 27002 aligns with the risk management principles of ISO 27001. It helps organizations assess and prioritize information security risks and effectively select appropriate controls to mitigate them. This risk-based approach ensures that resources are allocated efficiently and that security efforts focus on the most significant threats.
- Enhanced security posture: By implementing the controls recommended by ISO 27002, organizations can improve their overall security posture. The standard covers various domains, including access control, cryptography, physical security, incident management, and more, providing a comprehensive framework for addressing security vulnerabilities and protecting sensitive information.
- Compliance with regulations and standards: ISO 27002 assists organizations in meeting regulatory and legal requirements related to information security. It helps ensure compliance with industry-specific regulations and standards, such as the General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), and others.
- Stakeholder confidence and trust: Adhering to ISO 27002 demonstrates an organization’s commitment to information security and can enhance stakeholder confidence. Customers, partners, and other stakeholders are likelier to trust an organization that follows recognized international standards and implements robust security controls to protect their data and sensitive information.
- Alignment with industry best practices: ISO 27002 is based on widely accepted best practices in information security management. By aligning their practices with these standards, organizations can demonstrate that they follow industry-leading approaches to protecting information and mitigating security risks.
- Continual improvement: ISO 27002 emphasizes the importance of continual improvement in information security management. By regularly reviewing and updating their security controls based on evolving threats and vulnerabilities, organizations can adapt to changing circumstances and maintain a proactive stance against emerging risks.
- Competitive advantage: ISO 27002 certification or adherence to its guidelines can provide a competitive advantage for organizations. It showcases their commitment to information security, which can be a differentiating factor when seeking new clients, business partners, or contracts.
Perimeter81 ISO 27001 compliance confirms we meet the highest risk assessment and management level.
ISO 27001 and ISO 27002 Compliance Checklist
ISO 27001 and ISO 27002 are globally acknowledged as the leading international standards for managing information security. Presenting a fundamental compliance checklist for these standards:
ISO 27001 Checklist
Understanding the Organization’s Context
- Gaining a comprehensive understanding of the various factors that can affect information security is crucial.
- Identify the parties involved and their specific requirements.
Effective Leadership
- Ensuring the commitment of top management and establishing a comprehensive security policy.
- Establishing clear roles and responsibilities for information security.
Planning
- Perform a risk assessment taking into account the specific context and scope.
- Explain the process of developing a risk treatment plan.
- Set up objectives for information security.
Support
- Make sure there are enough resources available.
- Spread knowledge about the importance of safeguarding information.
- Outline the necessary skills for ensuring information security.
Operation
- Implement the risk treatment plan.
- Oversee updates to the information security system.
- Outline and describe processes and procedures.
Performance Evaluation
- Monitor, measure, analyze, and evaluate the performance of information security.
- Perform internal audits.
- Reviewing the information security management system from a management perspective.
Improvement
- Identify discrepancies and implement necessary measures for resolution.
- Consistent enhancement of the information security management system.
ISO 27002 Compliance Checklist
Information Security Policies
- Assess and record security policies.
Organization of Information Security
- Assign responsibilities.
- Information security in project management.
Human Resource Security
- Before being hired (for example, during the screening process).
- Throughout the duration of your job, it is important to stay informed and receive proper training.
- Procedures for terminating or changing employment.
Asset Management
- Identify and categorize information assets.
- Ensure the secure handling of media.
Access Control
- Administer user access.
- Oversee and control access privileges.
Cryptography
- Implement appropriate cryptographic controls as needed.
Physical and Environmental Security
- Ensure the physical premises are properly secured.
- Safeguard your systems from potential hazards.
Operations Security
- Ensure accurate and reliable operations.
- Ensure your system is secure from malicious software.
- Information for backup purposes.
Communications Security
- Ensure the proper management of network security.
- Ensuring the security of information transfer.
How does ISO 27001 and ISO 27002 Helps your Business
- Enhanced Information Security: ISO 27001 provides a framework for establishing, implementing, maintaining, and continually improving an ISMS within an organization. It helps identify and manage information security risks effectively, ensuring sensitive information’s confidentiality, integrity, and availability. By implementing ISO 27001, businesses can protect their valuable data and minimize the risk of security breaches or unauthorized access.
- Regulatory Compliance: Many industries have specific regulatory requirements for information security. ISO 27001 helps businesses demonstrate compliance with these regulations and legal obligations. Organizations can ensure they meet the requirements and avoid penalties or legal consequences by aligning their security practices with the ISO standard.
- Customer Trust and Competitive Advantage: ISO 27001 certification is widely recognized and respected globally. By obtaining certification, businesses can demonstrate their commitment to information security best practices, which enhances customer trust and confidence. It also provides a competitive advantage by differentiating the organization from competitors who may not have achieved the same level of security controls.
- Risk Management: ISO 27001 requires organizations to conduct a comprehensive risk assessment and establish a risk treatment plan. This systematic approach to risk management helps identify potential threats, vulnerabilities, and impacts on the organization’s information assets. By proactively addressing risks and implementing appropriate controls, businesses can minimize the likelihood and impact of security incidents.
- Continuous Improvement: ISO 27001 promotes a culture of continual improvement in information security management. It requires regular monitoring, measurement, analysis, and evaluation of the ISMS’s performance. By conducting internal audits, management reviews, and corrective actions, organizations can identify areas for improvement and enhance their security practices over time.
- Business Partnerships and Contracts: ISO 27001 certification can facilitate business partnerships and contracts with other organizations. Many businesses, especially those handling sensitive information, require their partners or vendors to have robust information security controls. ISO 27001 certification can prove a strong security posture, making establishing trust and secure business relationships easier.
- Employee Awareness and Training: Implementing ISO 27001 involves educating employees about information security risks, policies, and procedures. This helps raise awareness among staff members and promotes a security-conscious culture throughout the organization. By investing in employee training and awareness programs, businesses can minimize human error and strengthen the overall security posture.
Overall, ISO 27001 and ISO 27002 provide a structured approach to information security management, enabling businesses to protect their assets, meet regulatory requirements, gain customer trust, and continuously improve their security practices.
Implementing these standards demonstrates a commitment to information security and can benefit an organization’s operations, reputation, and competitive advantage.
Most Important Considerations of ISO 27001 and ISO 27002
- Management Support and Leadership: Senior management support and leadership are crucial for the successful implementation of ISO 27001 and ISO 27002. Top management should demonstrate a commitment to information security and allocate necessary resources for its implementation and maintenance.
- Risk Assessment and Management: Conducting a thorough risk assessment is critical in implementing ISO 27001. Organizations need to identify and assess the risks associated with their information assets and determine appropriate risk treatment measures. This involves analyzing threats, vulnerabilities, potential impacts, and likelihood of occurrence.
- Scope Definition: Clearly define the scope of the ISMS implementation, including the boundaries of the information assets and processes to be included. This ensures that the implementation efforts are focused and relevant.
- Legal and Regulatory Compliance: Consider the legal and regulatory requirements applicable to the organization’s industry and geographical location. Ensure that the ISMS is designed to meet these requirements and establish processes to monitor and ensure ongoing compliance.
- Information Security Policies: Develop and implement comprehensive policies that align with the organization’s objectives, risk appetite, and legal requirements. These policies should provide clear guidelines and expectations for employees regarding protecting information assets.
- Security Controls: ISO 27002 provides a set of controls that organizations can adopt to mitigate information security risks. Evaluate these controls based on the organization’s specific risks and requirements and select the most appropriate ones for implementation. Customize and adapt the controls as necessary to fit the organization’s context.
- Training and Awareness: Provide employees with adequate training and awareness programs to ensure they understand their roles and responsibilities in safeguarding information assets. This includes raising awareness about information security risks, policies, procedures, and best practices.
- Documentation and Records: Establish a robust documentation and record-keeping system to maintain evidence of the implementation and effectiveness of the ISMS. This includes documenting policies, procedures, risk assessments, control implementation, incident response, and monitoring activities.
- Internal Audits and Reviews: Conduct regular internal audits and management reviews to assess the effectiveness and compliance of the ISMS. These activities help identify areas for improvement, monitor performance, and ensure the ISMS remains aligned with the organization’s objectives.
- Continuous Improvement: Implement a process for continuous improvement of the ISMS. This involves regularly reviewing the performance of the system, addressing non-conformities, implementing corrective actions, and adapting the ISMS to changes in the organization’s environment, technology, and threats.
- Third-Party Relationships: Consider the security of third-party relationships, such as suppliers, contractors, and service providers. Assess their security controls and ensure appropriate contractual agreements are in place to protect the organization’s information assets.