What is Malicious Activity on Google play apps? Malicious activity on Google Play apps refers to any unauthorized, harmful, or deceptive behavior exhibited by certain [...]
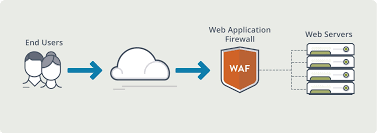
1. What is meany by WAF? A firewall that monitors, filters, and stops HTTP traffic going to and from a website or web application is [...]
What are Firmware updates : Firmware updates are software updates specifically designed to improve or modify the functionality of electronic devices, such as smartphones, computers, [...]
A router is a networking device that connects different networks together and directs data packets between them. It acts as a central hub for internet [...]
Common Network Protocols And Their Vulnerabilities Network protocols are essential for communication between devices and systems on a network. However, some protocols have vulnerabilities that [...]
What is VPN? VPN stands for Virtual Private Network. It is a technology that allows users to create a secure and encrypted connection over a [...]
What is a Proxy Server and how do they protect the computer network? A Proxy Server is an intermediary server that acts as a gateway [...]
Some potential challenges that might arise with the deployment of Wi-Fi 7 based on typical challenges faced when introducing new wireless technologies: Infrastructure Upgrade Device [...]
How can you secure a Wi-Fi network using encryption and authentication methods? Securing a Wi-Fi network is crucial to prevent unauthorized access and protect sensitive [...]
Sophos firewall configure an interface. Configuring an interface on a Sophos XG Firewall involves setting up the network parameters, such as IP address, subnet mask, [...]