Urgent Alert: CISA Warns of Exploited SharePoint Server 0-Day RCE Vulnerability Organizations worldwide face an immediate and severe threat: a critical zero-day remote code [...]
Unmasking CVE-2025-34300: Lighthouse Studio’s Critical RCE Vulnerability A silent giant in the market research landscape, Sawtooth Software’s Lighthouse Studio, faces a critical security reckoning. [...]
The digital threat landscape is a relentless battleground, demanding constant vigilance from cybersecurity professionals. Even in ostensibly secure environments, adversaries are finding new pathways [...]
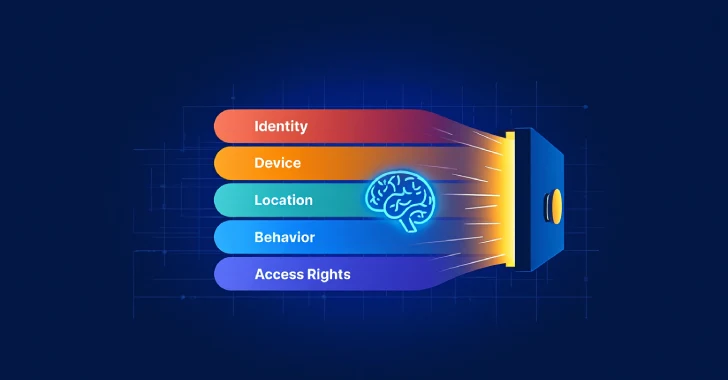
The Unseen Guardian: How AI is Forging the Future of Zero Trust By 2025, Zero Trust has evolved from a conceptual framework into an [...]
Unmasking KAWA4096: The Latest Ransomware Weaponizing WMI for Data Destruction The digital threat landscape is in constant flux, with new and increasingly sophisticated ransomware [...]
Critical RCE Vulnerability Strikes Livewire: Immediate Action Required for Laravel Applications A severe security vulnerability has been identified within Laravel’s popular Livewire framework, exposing [...]
The Silent Backdoor: HPE Aruba’s Hardcoded Credential Nightmare Unveiled Imagine a locked door, seemingly secure, only to discover a universally known key hidden beneath the [...]
The promise of strong, phishing-resistant multi-factor authentication (MFA) often rests on technologies like FIDO keys. Yet, even the most robust security mechanisms can be [...]
Navigating the Storm: Critical NVIDIA AI Container Toolkit Vulnerability Exposed The landscape of artificial intelligence is rapidly expanding, with containerized environments forming its crucial [...]
The Silent Threat: 3,500 Websites Hijacked for Covert Crypto Mining The digital landscape is a constant battleground, and a recent development has sent a [...]