Critical Cisco ISE Vulnerability: Root-Level Command Execution for Unauthenticated Attackers A severe security alert has been issued regarding critical vulnerabilities in Cisco Identity Services [...]
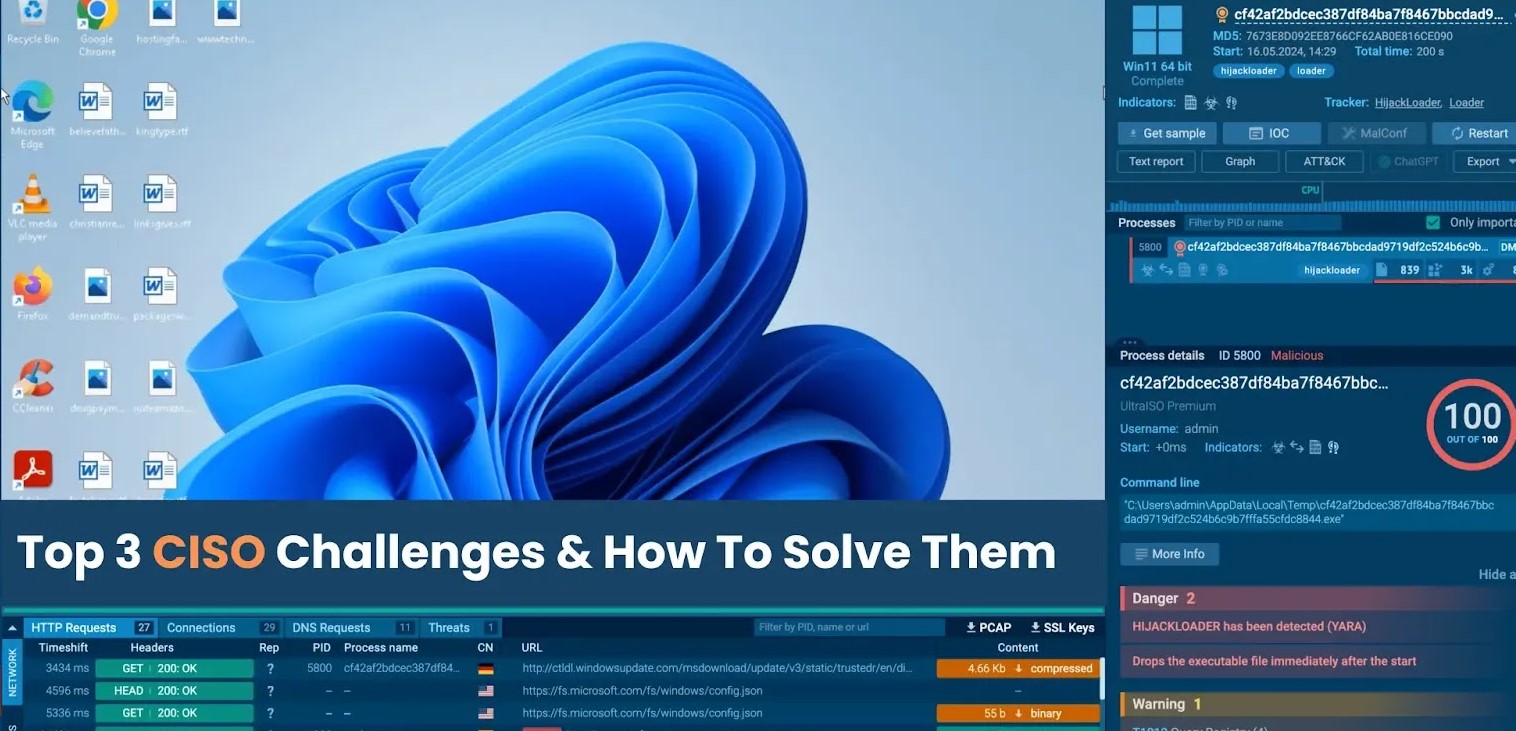
Leading a security team when threats outpace your defensive tools is a dilemma countless Chief Information Security Officers (CISOs) confront daily. The struggle is [...]
The digital footprint left on our mobile devices is a treasure trove of personal information. From intimate conversations to geographical traces, our smartphones hold [...]
Understanding UNG0002: A Persistent Espionage Threat A sophisticated and persistent cyber espionage campaign, attributed to the threat actor designated UNG0002 (Unknown Group 0002), has [...]
Iranian Threat Actors Leveraging AI-Crafted Emails to Target Cybersecurity Researchers and Academics
Iranian Threat Actors Elevate Cyber Warfare with AI-Crafted Phishing The landscape of cyber threats is in constant flux, with adversaries continuously refining their tactics [...]
The long arm of international law enforcement has once again demonstrated its reach into the shadowy world of cybercrime. A significant victory for cybersecurity, an [...]
The Alarming Truth: CitrixBleed 2 Exploited Before Public Disclosure In the relentlessly evolving landscape of cyber threats, the proactive exploitation of vulnerabilities before their [...]
Co-op Confirms 6.5 Million Members’ Data Compromised in Significant Cyberattack The UK’s retail giant, Co-op, has officially confirmed a massive data breach, impacting the [...]
The Silent Sabotage: Threat Actors Weaponize npm Packages with Protestware The digital supply chain, a cornerstone of modern software development, has once again become [...]
Unmasking the Covert Channel: How DNS Queries Become Attack Vectors The Domain Name System (DNS) is the internet’s bedrock, translating human-readable domain names into [...]