Email is the lifeblood of modern communication, but it remains a primary vector for cyberattacks. As organizations invest heavily in sophisticated email filtering solutions, [...]
Unpacking the Claude AI Exploitation: A Deep Dive into Model Context Protocol Vulnerabilities The convergence of powerful AI systems and seemingly isolated digital components [...]
In the high-stakes world of enterprise security, the integrity of identity and access management (IAM) is paramount. A security flaw in a cornerstone product [...]
Navigating the Shadowy Depths: SquidLoader’s Elusive Threat to Financial Security In the high-stakes world of cybersecurity, a threat that can bypass conventional defenses with [...]
In the intricate landscape of software development and system administration, tools like Vim are indispensable. Millions of developers and IT professionals rely on this [...]
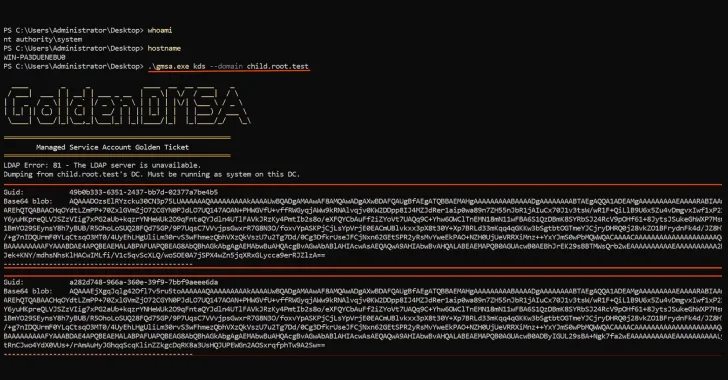
Unveiling the Critical Golden dMSA Attack: A Major Security Flaw in Windows Server 2025 A significant cybersecurity threat has emerged with the disclosure of [...]
The digital landscape is a constant battleground, and for MacOS users, a new sophisticated threat has emerged: NimDoor malware. This insidious campaign, attributed to [...]
Urgent Alert: Google Chrome 0-Day Vulnerability Actively Exploited in the Wild In the dynamic realm of digital security, a critical alert has emerged from [...]
The digital fabric connecting our lives, services, and governance is under constant siege. No entity, regardless of its size or location, is immune to [...]
International Law Enforcement Dismantles Diskstation Ransomware, Protecting Synology NAS Users In a significant victory for cybersecurity, a coordinated international law enforcement effort, spearheaded by [...]