Elmo’s X Account Hacked: A Stark Reminder of Social Media Account Security Risks In a deeply disturbing incident that sent shockwaves through the cybersecurity [...]
Unmasking Digital Malice: The Islamophobic WiFi Hack and its Profound Implications The digital frontier, while offering unprecedented connectivity, remains a battleground against malicious intent. [...]
CISA Sounds the Alarm: Wing FTP Server Under Active Exploitation A critical cybersecurity alert has been issued by the Cybersecurity and Infrastructure Security Agency [...]
Critical Zero-Day: Symantec Endpoint Management Suite Exposes Enterprises to Remote Code Execution The digital perimeter of enterprise networks is under constant siege, and a [...]
The digital battleground just escalated. Recent reports from Cloudflare reveal a worrying surge in hyper-volumetric Distributed Denial of Service (DDoS) attacks, with individual incidents [...]
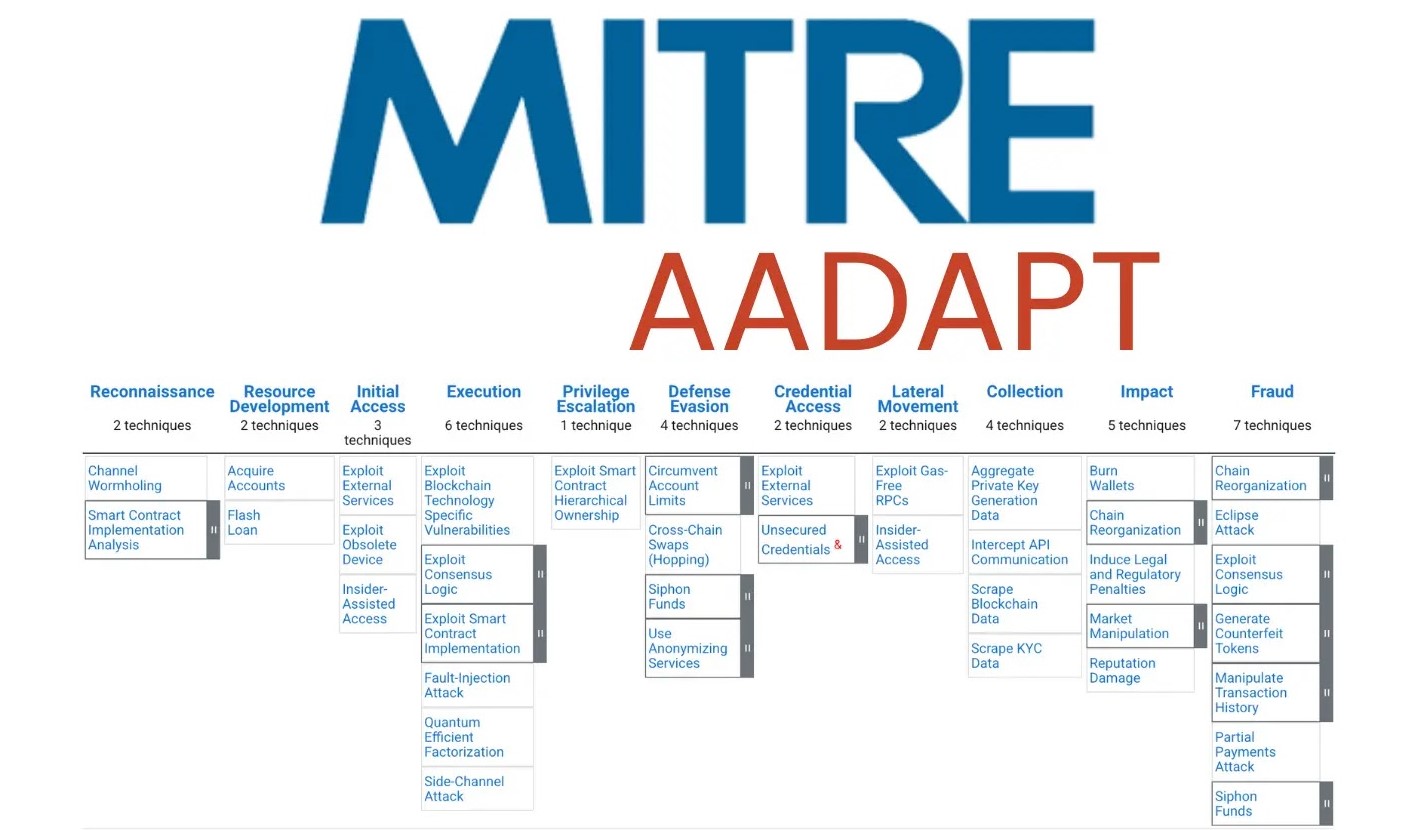
Unveiling AADAPT: MITRE’s Critical Framework for Digital Asset Security The landscape of digital assets, from cryptocurrencies to tokenized real estate, continues its meteoric rise, [...]
Unmasking the LaRecipe Vulnerability: A Critical Threat to Server Control In the expansive realm of software development, tools designed to streamline processes are invaluable. [...]
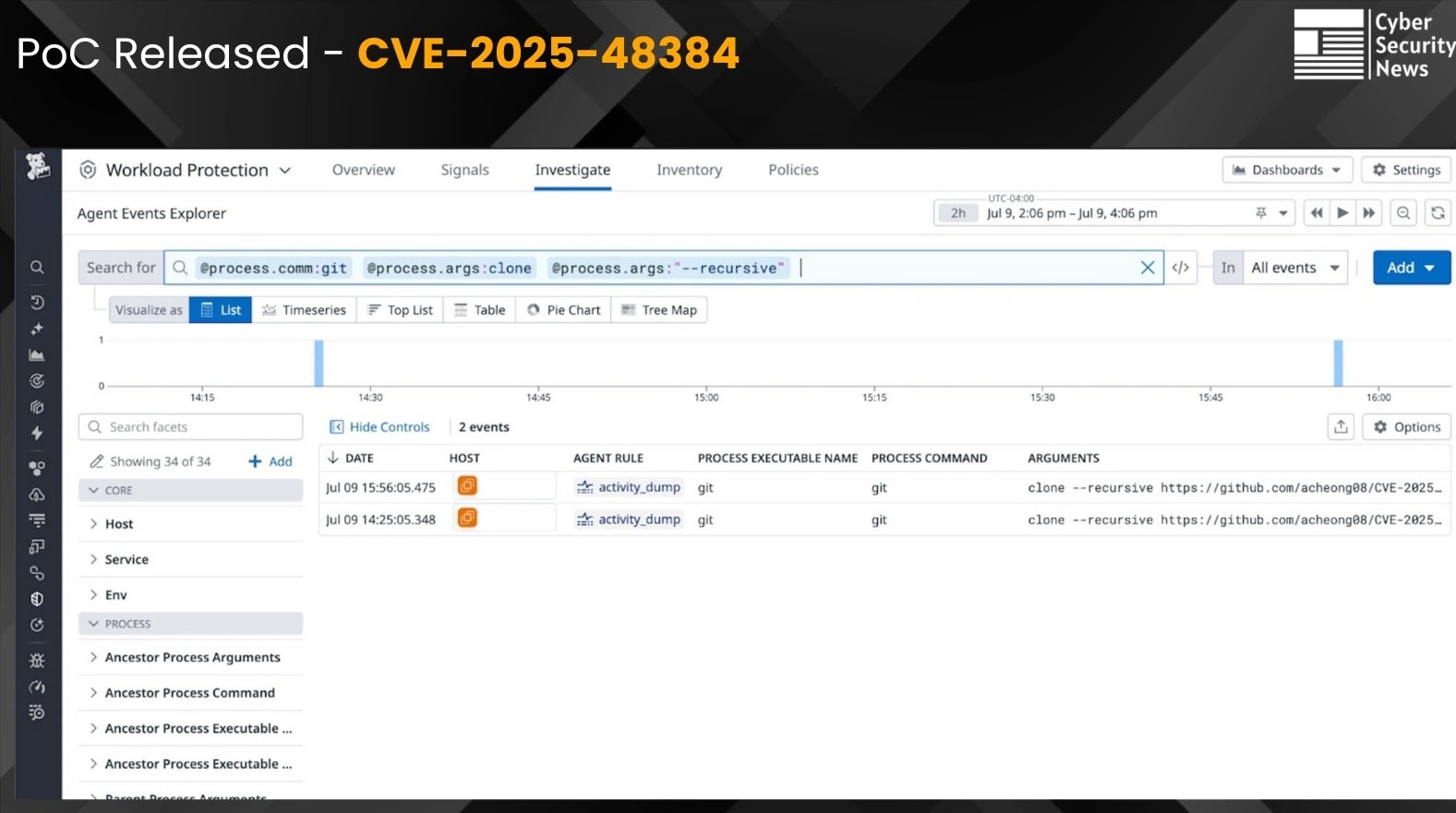
The rapid pace of software development relies heavily on version control systems, and Git stands as an undisputed leader. However, its pervasive use also [...]
In a significant victory against international cybercrime, a coordinated operation recently led to the arrest of fourteen individuals implicated in a large-scale tax fraud scheme. [...]
The promise of Artificial Intelligence agents automating complex tasks, from financial reconciliation to real-time incident response, heralds a new era of operational efficiency. Yet, [...]