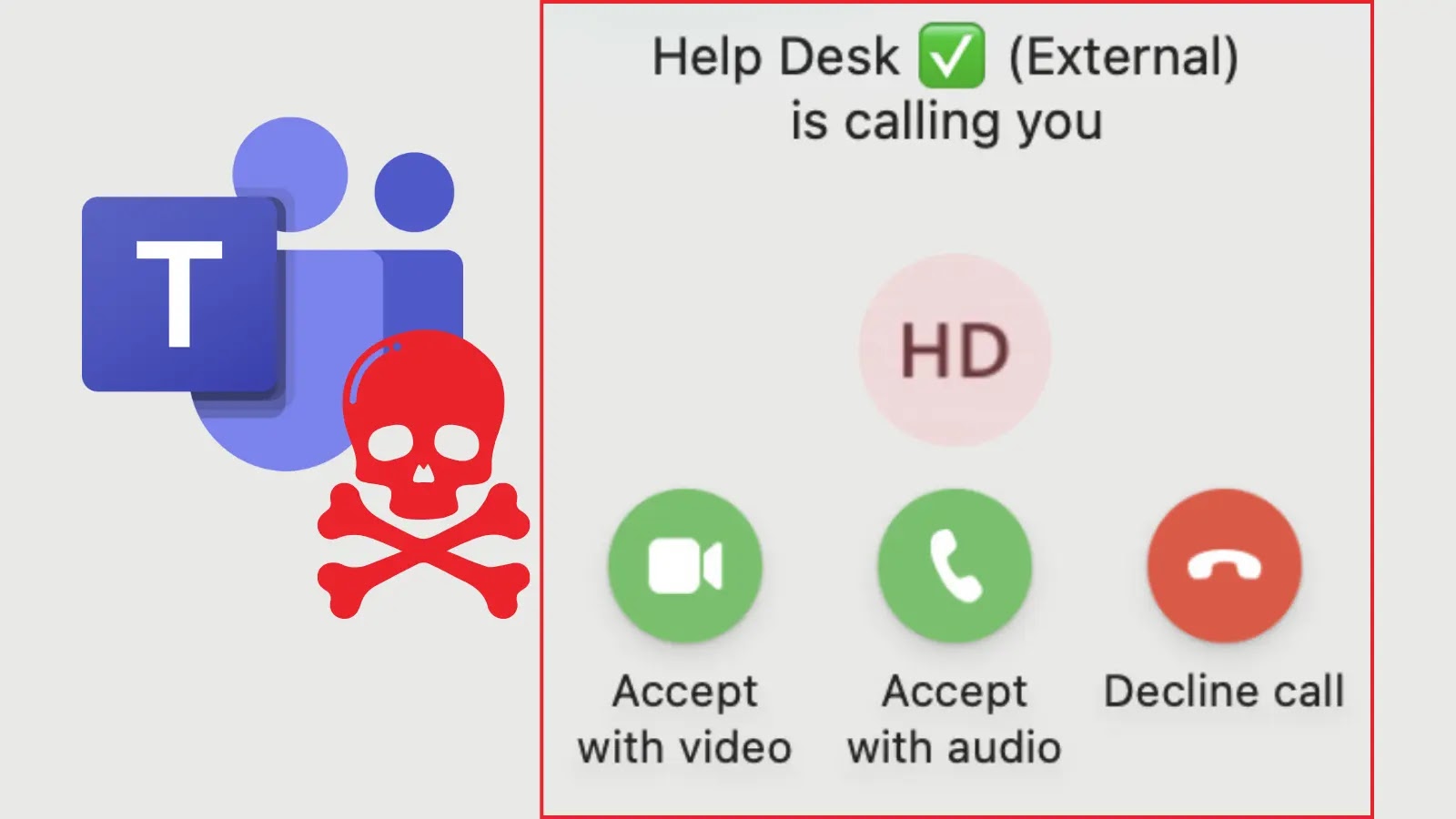
The Silent Threat: How Microsoft Teams Becomes a Beachhead for Remote Access Attacks Infiltrating an organization often begins with a meticulously crafted deception. Recent [...]
Social Engineering Attacks in 2025: The Psychology of Social Engineer In the ever-evolving landscape of cybersecurity, understanding the psychology of social engineers and the tactics [...]
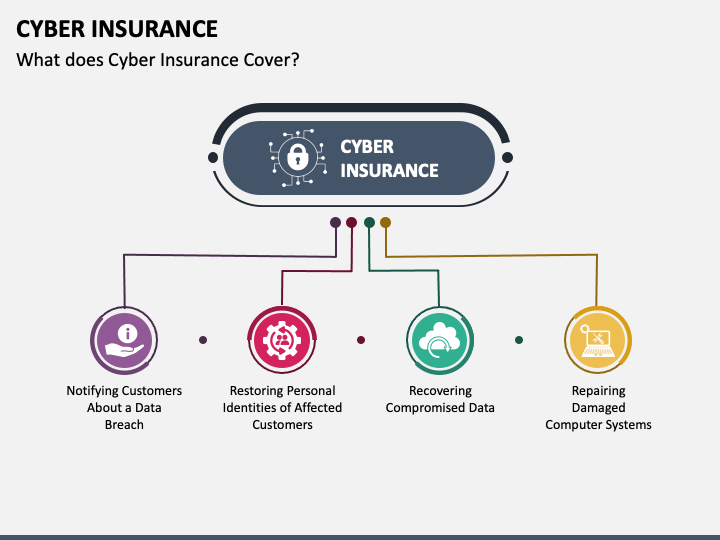
What it Cyber Insurance Policies Doesn’t Covers: Coverage and Cyber Liability In an era where digital threats loom large, securing your business against cyber [...]
In the intricate landscape of network infrastructure and data center management, the security of administrative interfaces is paramount. A single vulnerability in these critical [...]
Unmasking UTG-Q-1000: When National Benevolence Becomes a Data Exfiltration Weapon The global cybersecurity landscape is under constant siege, with threat actors evolving sophisticated tactics [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Authorization Bypass vulnerability in WhatsApp Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected WhatsApp for [...]
ShadowSilk: Unmasking the Covert Campaigns Exploiting Penetration Testing Tools and Public Vulnerabilities The cybersecurity landscape is in constant flux, and threat actors are perpetually [...]
Urgent Warning: FreePBX Servers Under 0-Day Attack – Immediate Action Required In a critical development for voice over IP (VoIP) infrastructure, a severe zero-day [...]
Unmasking TamperedChef: A Weaponized PDF Editor Steals Credentials In an increasingly complex threat landscape, adversaries continuously refine their tactics. A recent discovery by Truesec, [...]
Emulating Scattered Spider: Proactive Defense Against Sophisticated APTs The landscape of cyber threats is dynamic, with advanced persistent threats (APTs) continually refining their tactics. [...]