The dark web’s digital black markets are constantly evolving, and a new threat looms large for macOS users. A sophisticated new stealer, whimsically dubbed [...]
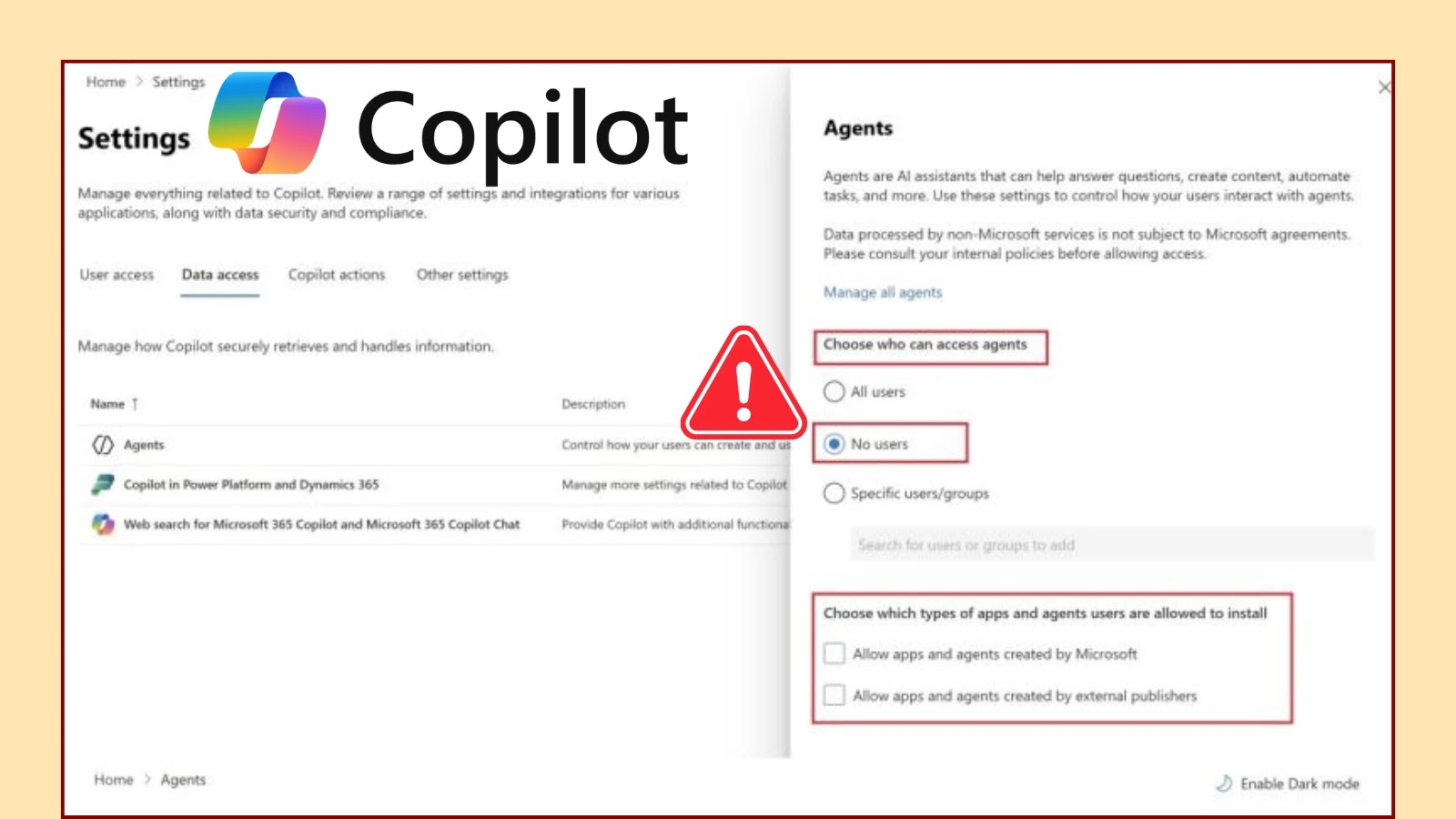
In the rapidly evolving landscape of enterprise technology, the promise of artificial intelligence offers unprecedented efficiency and innovation. Yet, integration of powerful AI capabilities, [...]
Unmasking Cyber Threats: The Imperative of Robust Incident Response in 2025 The digital landscape of 2025 presents an increasingly complex and hostile environment for [...]
Unveiling the Sentinel: Why Network Monitoring is Non-Negotiable in 2025 The intricate tapestry of modern business operations is woven with threads of interconnected networks. [...]
Colt Confirms Customer Data Stolen: A Deep Dive into the Ransomware Breach The telecommunications industry, a cornerstone of global connectivity, has once again been [...]
For years, Linux environments have been lauded as strongholds of security, widely considered robust against the persistent onslaught of cyber threats. However, this established [...]
The digital threat landscape constantly evolves, and staying ahead of sophisticated attack vectors is paramount for any organization. Recently, a disturbing new social engineering [...]
The Stealthy Surge of Anatsa Malware: A Deep Dive into Android’s Persistent Banking Threat In the relentless landscape of mobile security, a persistent threat continues [...]
The cybersecurity landscape has undergone a seismic shift, and the ground beneath defenders’ feet is trembling. For years, the “grace period” – that critical [...]
A New Threat Emerges: QUIC-LEAK Vulnerability Exposes Servers to DoS Attacks The digital infrastructure underpinning a significant portion of the internet relies on efficient [...]