The landscape of cybersecurity is constantly shifting, and with the rapid advancements in artificial intelligence, a new and insidious threat has emerged: “AI-induced destruction.” [...]
Unmasking Out-of-Bounds Read and Write Vulnerabilities: A Critical Threat to System Integrity Imagine a digital fortress with robust walls, yet a hidden flaw allows [...]
DragonForce Ransomware: Unmasking a Rapidly Evolving Threat The cybersecurity landscape faces a persistent and often overwhelming challenge from ransomware operations. Among the newer, more [...]
Imagine navigating a legitimate website, intending to complete a routine task, only to be confronted by a CAPTCHA. You diligently solve it, as you’ve always [...]
Urgent CISA ICS Advisories: Critical Vulnerabilities Impacting Industrial Control Systems The Cybersecurity and Infrastructure Security Agency (CISA) has issued a series of critical advisories [...]
Urgent macOS Alert: SHAMOS Malware Surges, Threatening Credentials Via Fake Support Sites The digital landscape is under constant siege, and macOS users are now [...]
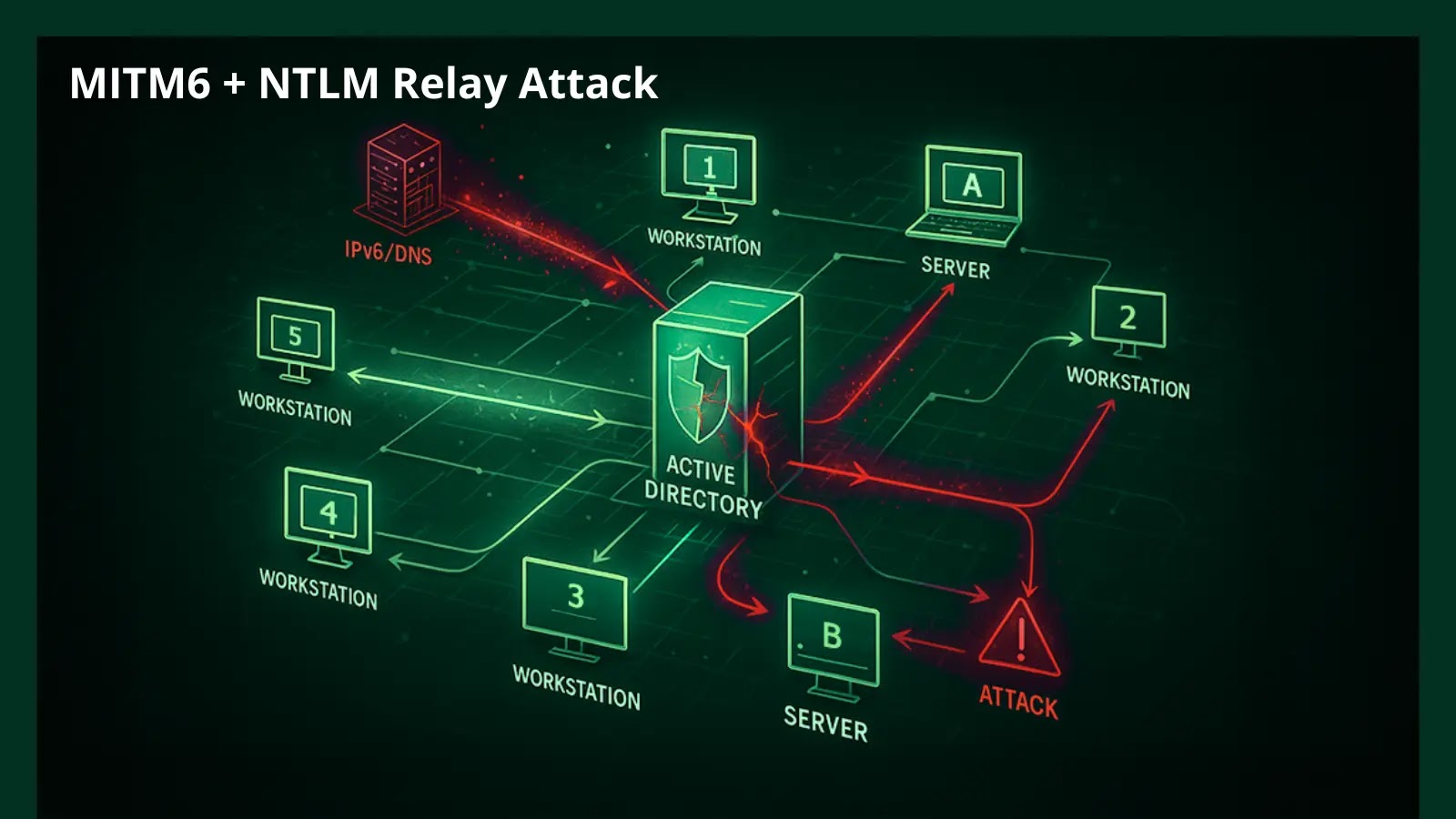
Unmasking the MITM6 + NTLM Relay Attack: A Path to Domain Admin in Minutes The digital landscape is a constant battleground, and threat actors [...]
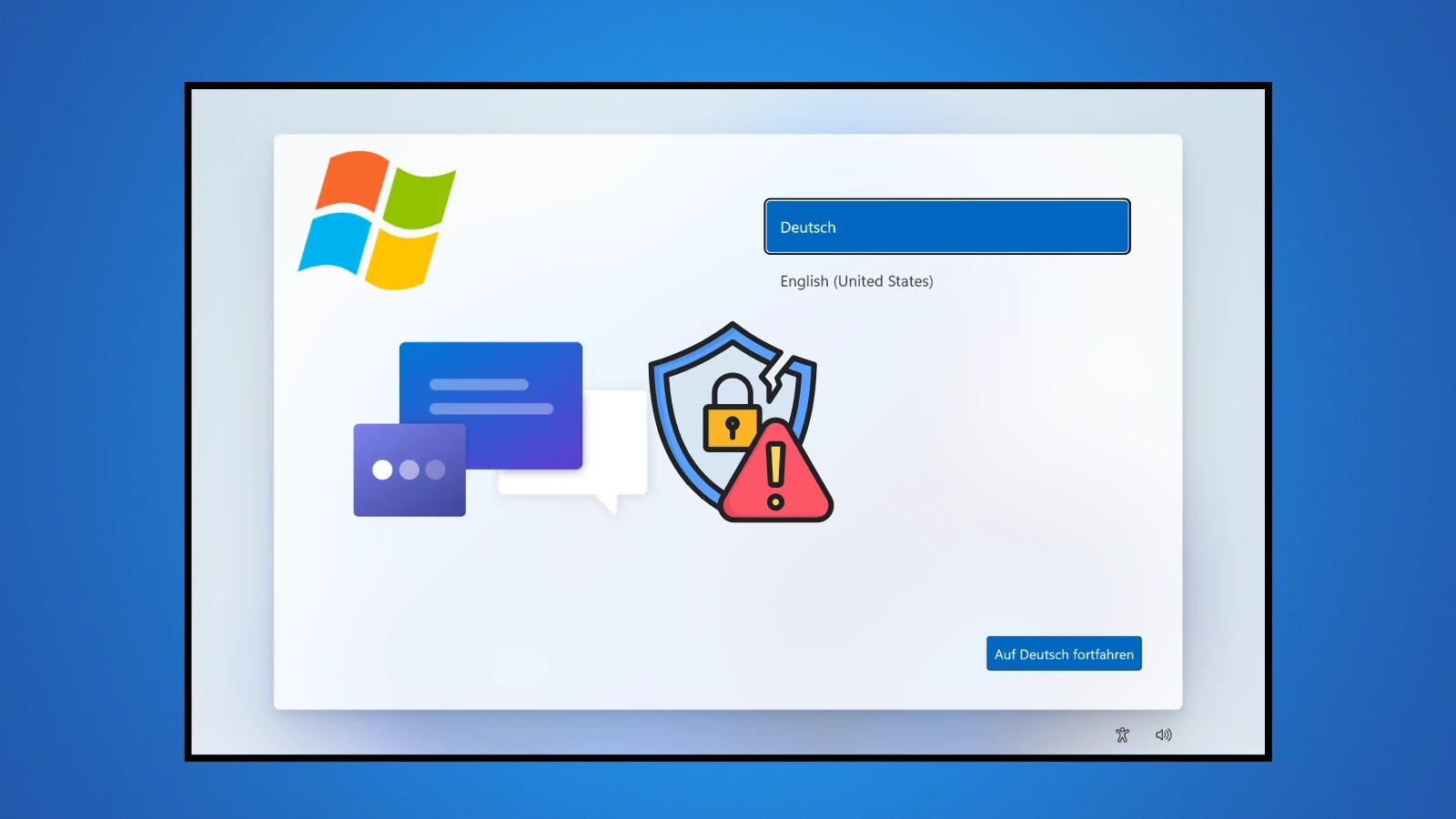
Unmasking the Covert Access: Bypassing Windows OOBE for Admin Privileges Imagine a freshly installed Windows machine, pristine and seemingly secure, yet fundamentally vulnerable from [...]
A critical vulnerability has surfaced within Fortinet’s FortiSIEM platform, posing a significant threat to organizations utilizing this security information and event management solution. Details [...]
Russian Hackers Exploiting 7-Year-Old Cisco Vulnerability to Collect Configs from Industrial Systems
Urgent Warning: Russian Hackers Exploit 7-Year-Old Cisco Flaw in Industrial Systems The cybersecurity landscape continually presents new threats, but sometimes, the gravest dangers lurk [...]