The digital frontier is constantly under siege, with threat actors relentlessly innovating their attack methodologies. Among these, the emergence of the EncryptHub threat group, [...]
The landscape of enterprise IT and personal computing is constantly evolving, with new architectures and operating systems pushing the boundaries of what’s possible. Seamless [...]
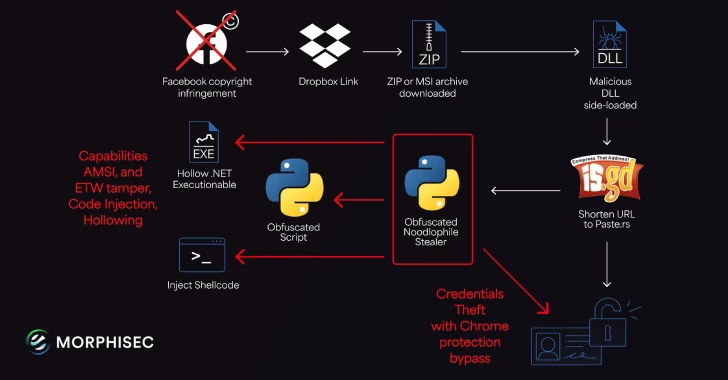
Noodlophile Malware: Unmasking the Global Copyright Phishing Threat The digital landscape is a constant battleground, and sophisticated threats emerge daily. Today, we delve into [...]
The cybersecurity landscape is constantly evolving, with new threats emerging that challenge even the most robust defenses. A sophisticated zero-day exploitation script targeting SAP [...]
The Covert Channel: How Threat Actors Weaponize Telegram for Data Exfiltration In the evolving landscape of cyber threats, adversaries constantly seek novel methods to [...]
PyPI Fortifies Supply Chain: Over 1,800 Expired-Domain Emails Blocked to Counter Account Takeovers The digital landscape of software development is in a constant state [...]
The Python Package Index (PyPI), a cornerstone of the Python development ecosystem, has once again been leveraged by malicious actors. A sophisticated supply chain [...]
Unmasking PipeMagic: How Threat Actors Leverage Microsoft Help Index Files for Stealthy Malware Delivery The cybersecurity landscape is in constant flux, with threat actors [...]
Weaponizing Trust: How Hackers Exploit Cisco Secure Links to Bypass Defenses The digital threat landscape is in constant flux, with adversaries perpetually refining their [...]
Urgent Cybersecurity Alert: Over 1000 N-able N-central RMM Servers Exposed to 0-Day Vulnerabilities The cybersecurity landscape has been rocked by the discovery of over [...]