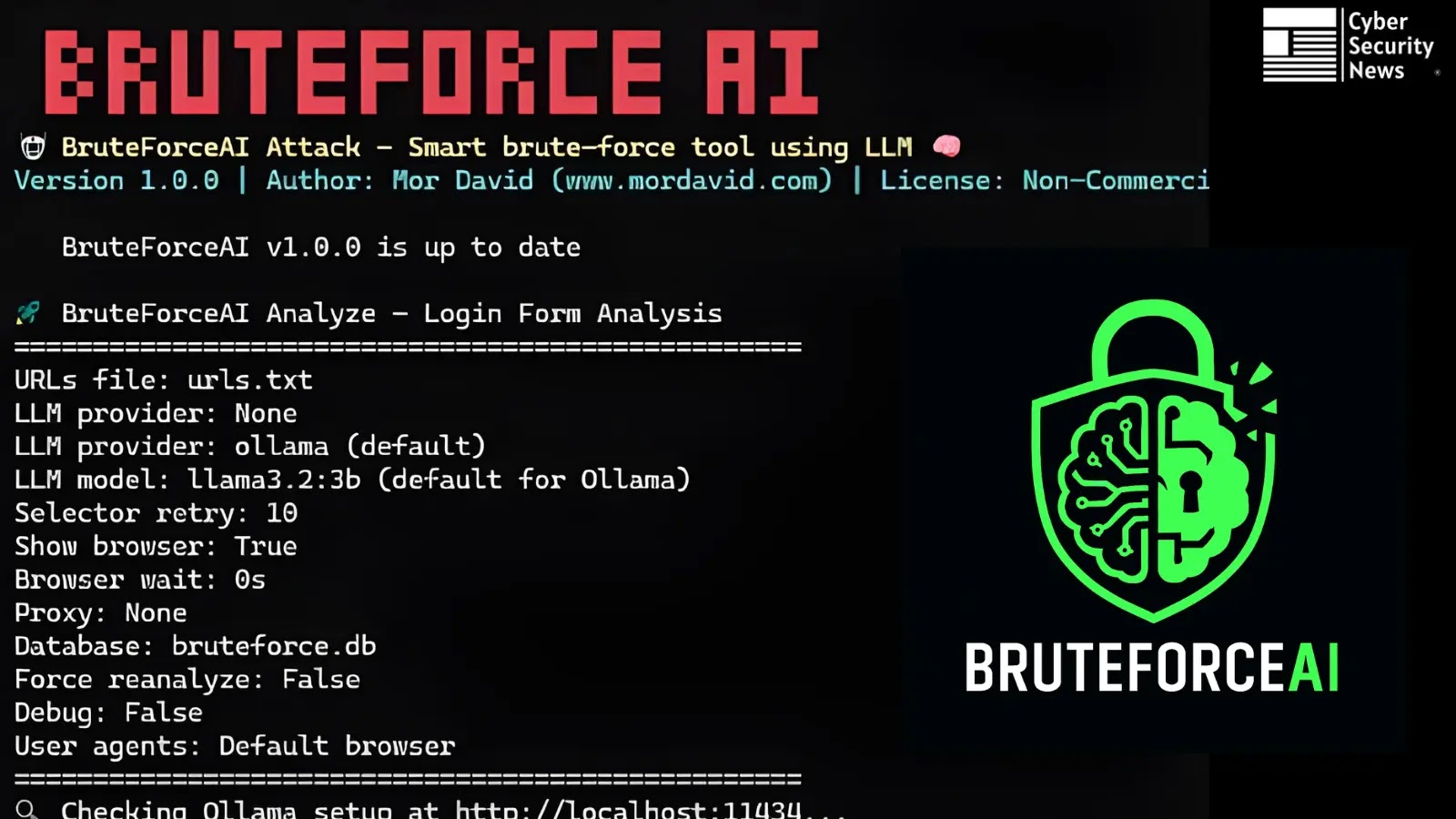
The landscape of cyber threats is constantly evolving, with attackers leveraging increasingly sophisticated tools and techniques. For organizations, the critical task of identifying and [...]
DOGE Accused of Copying Nation’s Social Security Data to Unsecured Cloud: A Crisis of Trust and Data Security A recent whistleblower disclosure has sent [...]
The manufacturing sector, the backbone of innovation and production, faces a persistent and evolving threat landscape. In a recent development underscoring this vulnerability, a [...]
The landscape of cyber threats is in constant flux, with adversaries continually refining their tactics to breach organizational defenses. A recent and particularly concerning [...]
A significant security alert has been issued regarding an urgent patch for Google Chrome. A critical use-after-free vulnerability has been discovered in the browser’s ANGLE [...]
The digital landscape continually presents new attack vectors, and the recent breach involving Salesloft Drift highlights a particularly insidious one: the compromise of third-party application [...]
In the high-stakes arena of cyber espionage, understanding the adversary is paramount to effective defense. Few threats loom as persistently as state-sponsored advanced persistent [...]
The mobile threat landscape just got significantly more perilous. A formidable new iteration of the Hook Android banking trojan has emerged, boasting capabilities that [...]
The Critical Vulnerability: CVE-2025-53118 in Securden Unified PAM A significant security flaw has been identified in Securden Unified PAM, a widely used privileged access [...]
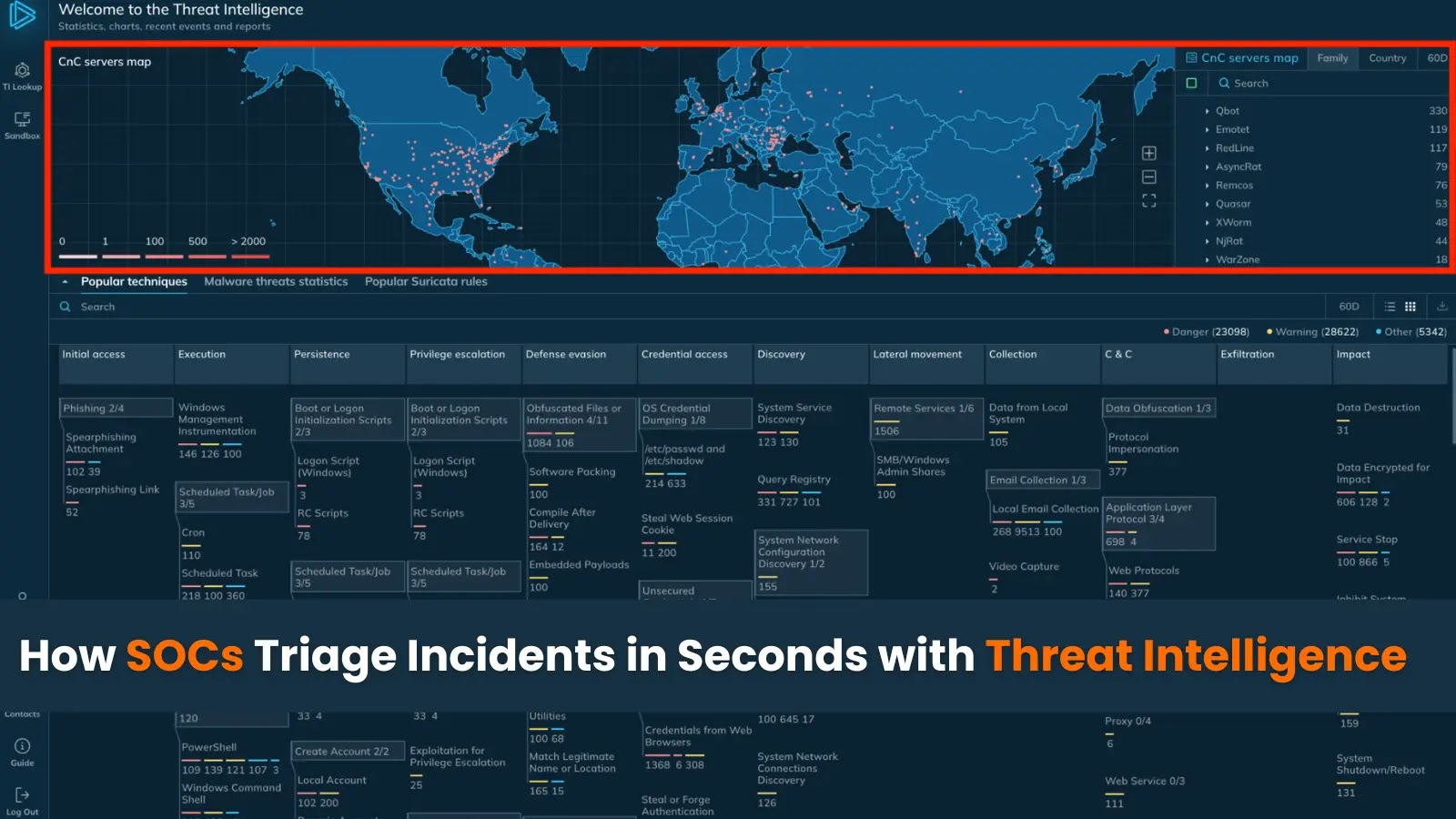
How SOCs Triage Incidents in Seconds with Threat Intelligence In the high-stakes world of cybersecurity, every second counts when responding to potential threats. Security [...]