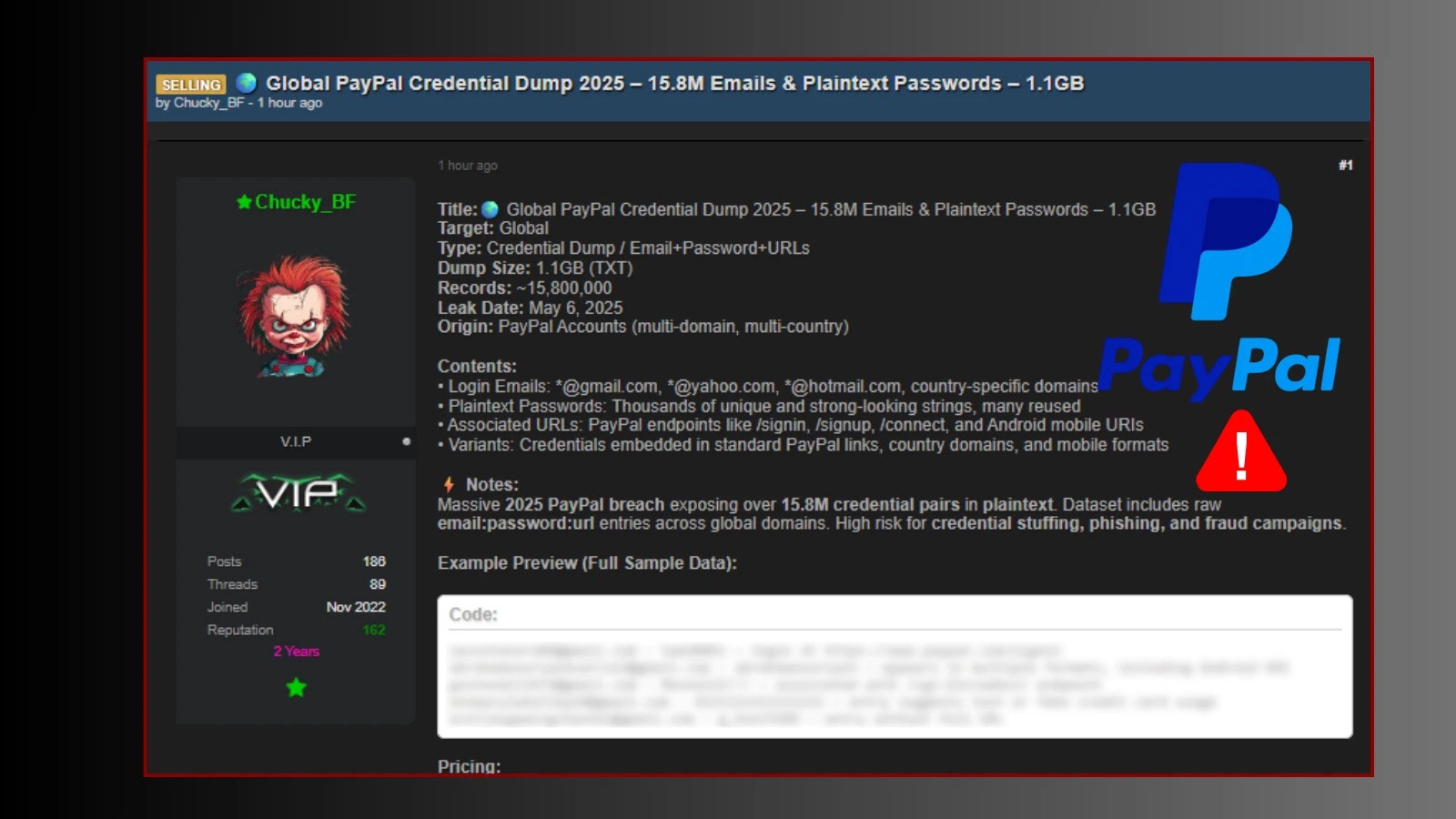
Urgent Warning: Alleged PayPal Credential Leak – 15.8 Million Plaintext Pairs at Risk The digital threat landscape continues to evolve at an alarming pace, [...]
In a startling revelation that underscores the relentless and evolving threat landscape, a significant cache of highly sensitive hacking tools and detailed technical documentation, [...]
Windows 11 24H2 Update: A Critical Threat to Data Integrity The digital landscape is fraught with unforeseen challenges, and few are as immediately alarming [...]
Hundreds of TeslaMate Installations Exposing Sensitive Vehicle Data In a significant cybersecurity discovery, a researcher has unveiled a critical vulnerability affecting hundreds of TeslaMate [...]
Workday Data Breach: A Deep Dive into the Third-Party CRM Compromise The digital landscape is a minefield of potential cybersecurity threats. Even the most [...]
The Critical Threat to Industrial Control Systems: Rockwell ControlLogix Ethernet Vulnerability The operational technology (OT) landscape is a critical foundation for modern industry, yet it [...]
Urgent Alert: Critical PostgreSQL Vulnerabilities Expose Databases to Arbitrary Code Injection During Restoration Organizations relying on PostgreSQL, a cornerstone of modern data infrastructure, face [...]
In the intricate landscape of software security, few vulnerabilities pose as persistent and critical a threat as Use-After-Free (UAF). These insidious flaws, deeply rooted [...]
In an era where data breaches headline nightly news and regulatory bodies levy hefty fines, the burden of maintaining robust cybersecurity and achieving regulatory [...]
The software supply chain, a foundational element of modern development, faces an insidious and escalating threat: malicious packages lurking within public repositories. These aren’t [...]