Urgent Alert: Critical DoS Vulnerability in Cisco Secure Firewall Snort 3 Detection Engine In the evolving landscape of network security, firewalls stand as the [...]
Unmasking the Adversary: Why Deception Technology is Your Next Cybersecurity Imperative The relentless evolution of cyber threats means that even organizations with robust perimeter [...]
The digital landscape is a constant battleground, where even the most ubiquitous software can become an unexpected vector for attack. Recently, a critical zero-day vulnerability [...]
In the relentlessly evolving landscape of cyber threats, understanding the methodologies of sophisticated adversaries is paramount. A recent campaign by the Russian threat actor [...]
Cisco’s Critical Warning: CVSS 10.0 FMC RADIUS Flaw Puts Networks at Risk A severe vulnerability has surfaced, demanding immediate attention from network administrators and [...]
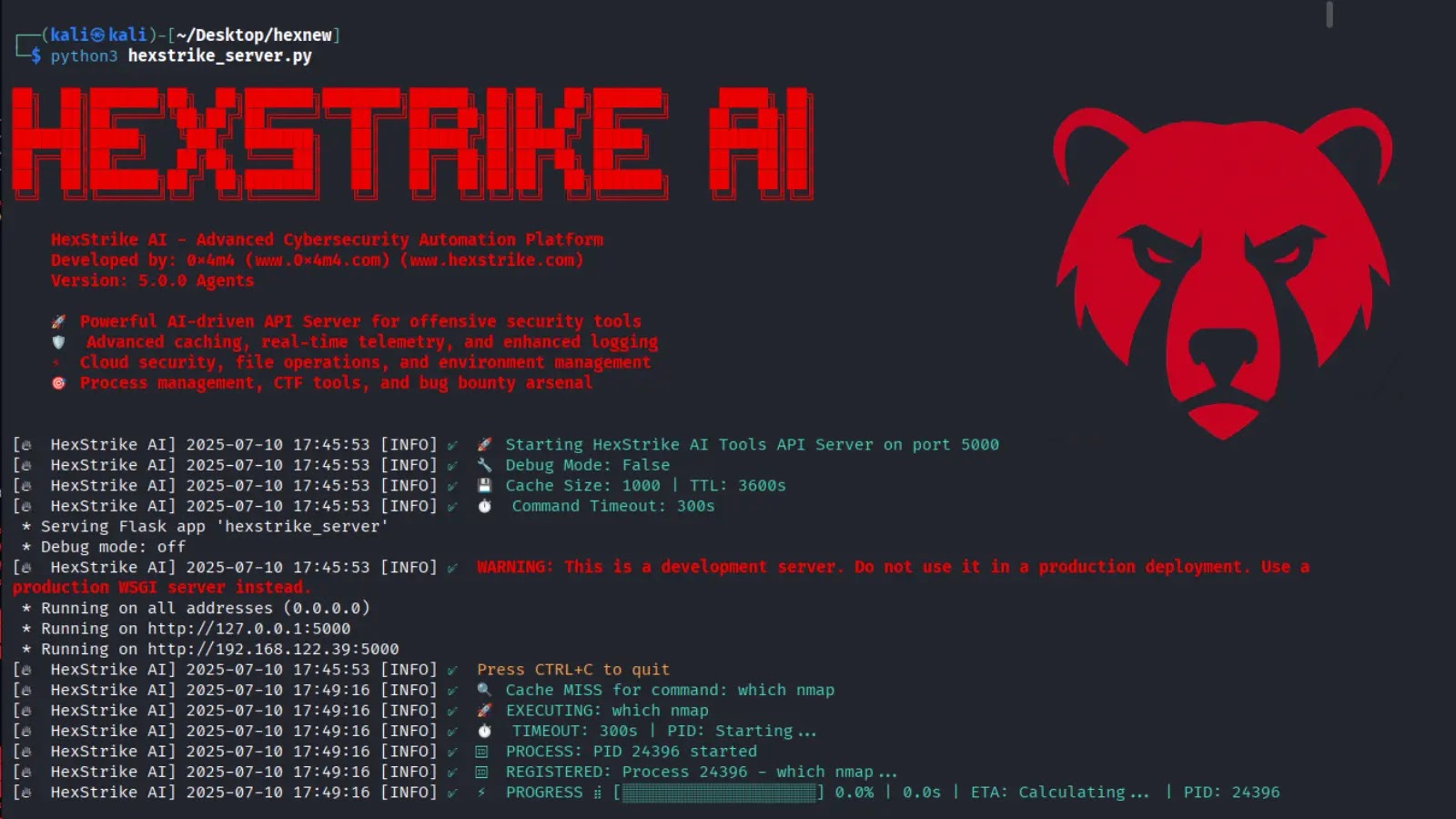
HexStrike AI: Revolutionizing Cybersecurity with LLM-Powered Automation The landscape of cybersecurity is undergoing a profound transformation, driven by the rapid advancements in artificial intelligence. [...]
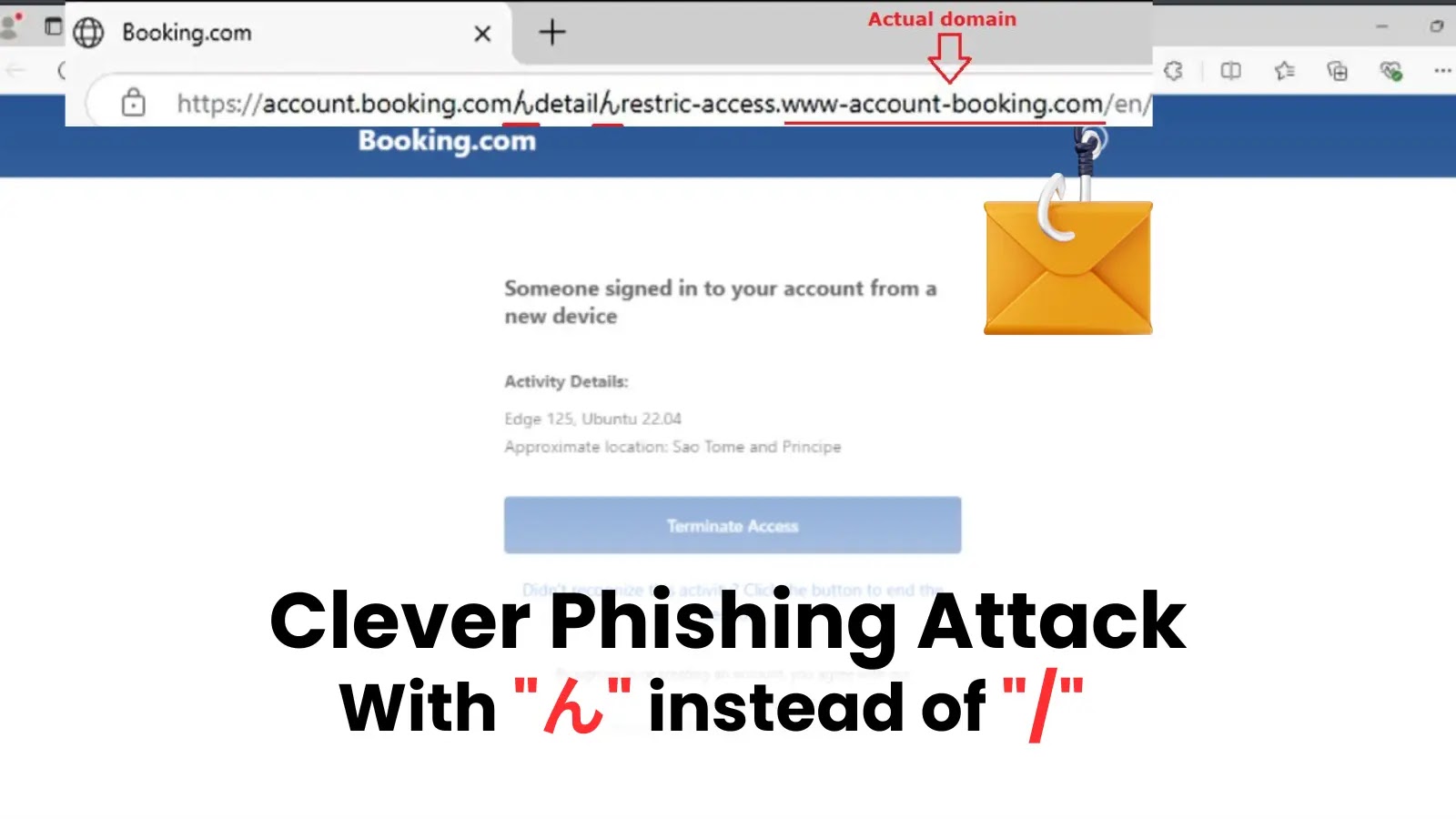
The Deceptive “ん” Phishing Attack: A New Twist in URL Mimicry In the evolving landscape of cyber threats, attackers constantly innovate, finding subtle ways [...]
The digital frontier, while offering unprecedented opportunities, also serves as a battleground for illicit activities. A recent significant development underscores the persistent threat posed [...]
Zero Trust + AI: Reimagining Privacy in the Age of Agentic AI Privacy used to be a perimeter problem. We secured our digital assets [...]
Unmasking UAT-7237: The APT Group Pilfering Taiwan’s Web Infrastructure The digital frontier is a constant battleground, and the recent breach of Taiwan’s web servers [...]