Unmasking the Threat: Full Control Over Your Rooted Android via Critical Vulnerability For many Android enthusiasts, rooting a device offers an unparalleled level of customization [...]
Unmasking PS1Bot: A New Multi-Stage Threat Emerging from Malvertising Campaigns In the relentless landscape of cyber threats, new adversaries emerge with alarming frequency, sophisticated [...]
Microsoft Sunsets PowerShell 2.0: A Step Towards Enhanced Security The digital landscape continually shifts, and with each evolution, operating systems must adapt to remain [...]
A critical alarm has sounded in the cybersecurity community: the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has officially added a severe WinRAR zero-day [...]
Navigating the New Frontier of AI-Powered Vulnerabilities: GitHub Copilot RCE Unveiled The pace of innovation in artificial intelligence is breathtaking, empowering developers with tools [...]
Organizations worldwide rely on GitLab for their software development lifecycle, from version control to continuous integration and deployment. A breach in such a critical [...]
In the intricate landscape of enterprise technology, Microsoft Exchange Server stands as a cornerstone for communication and collaboration. Its criticality, however, makes it a prime [...]
CISA Flags N-able N-central Flaws: Urgent Action Required for MSPs The cybersecurity landscape demands constant vigilance, especially for organizations that manage critical IT infrastructure [...]
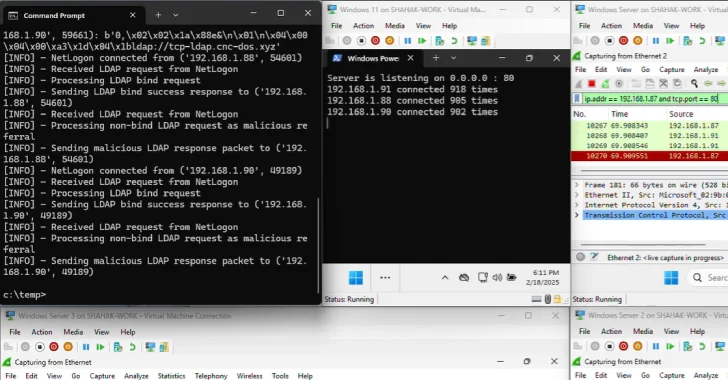
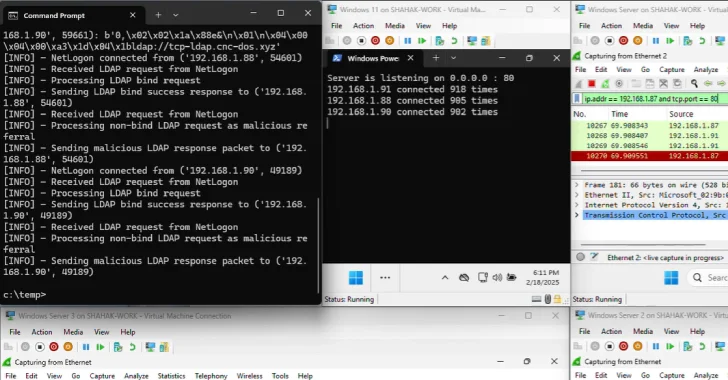
A disturbing new threat has emerged from the DEF CON 33 security conference, casting a long shadow over Windows environments globally. Researchers Yair and [...]
A disturbing new attack technique, dubbed Win-DDoS, has been unveiled, posing a significant threat to global network infrastructure. This novel approach enables attackers to [...]