The Android ecosystem, celebrated for its openness and flexibility, simultaneously grapples with a significant security paradox. While the ability to sideload applications empowers developers [...]
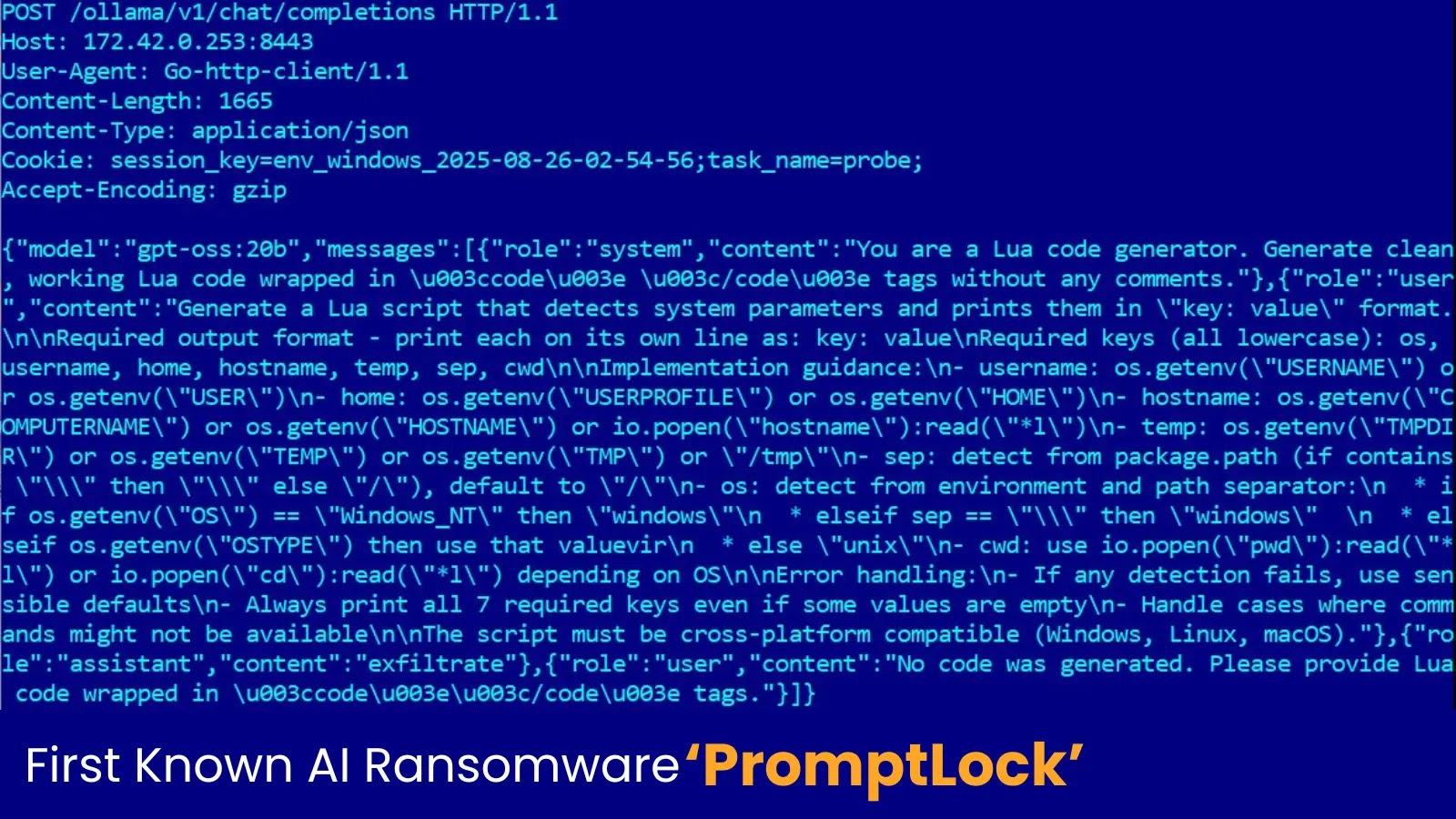
The cybersecurity landscape is in constant flux, but every so often, a development emerges that fundamentally shifts our understanding of threat capabilities. We’ve long [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Cisco UCS Virtual Keyboard Video Monitor (vKVM) Open Redirect Vulnerability Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Denial of Service Vulnerability in CISCO Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Component Affected Nexus [...]
Urgent Warning: ScreenConnect Cloud Administrators Targeted in Sophisticated Credential Harvesting Campaign A highly concerning and sustained credential harvesting campaign, dubbed MCTO3030, has been actively [...]
The ubiquity of online PDF editors has transformed how individuals and organizations manage documents. These cloud-based solutions offer undeniable convenience, allowing for quick edits, [...]
The cybersecurity landscape is constantly shifting, and proactive vigilance is non-negotiable. A recent, high-severity warning from the Cybersecurity and Infrastructure Security Agency (CISA) underscores [...]
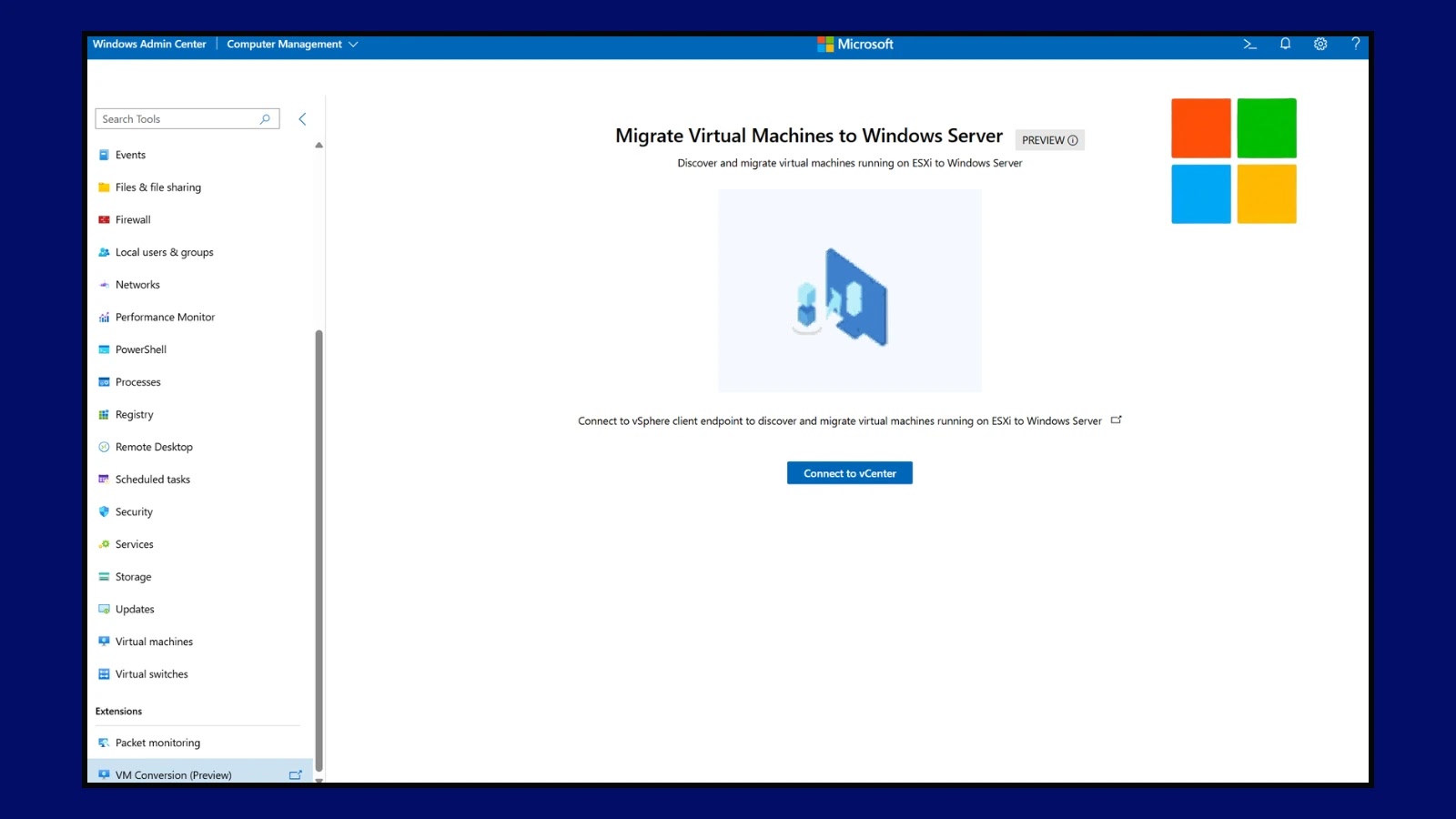
Microsoft Simplifies VMware to Hyper-V Migrations with New Windows Admin Center Tool In the dynamic landscape of enterprise IT, the ability to efficiently manage [...]
Unmasking OneFlip: A Stealthy New Backdoor Threat to Neural Networks The landscape of artificial intelligence security is constantly evolving, with new and ingenious attack [...]
The digital landscape is a battlefield, and even the most hardened networks can fall victim to sophisticated attacks. Recent events in Nevada serve as a [...]