The Silent Threat: RubyGems Malware Weaponizes 60+ Packages to Steal Credentials The digital landscape is a constant battleground, and threat actors continually evolve their [...]
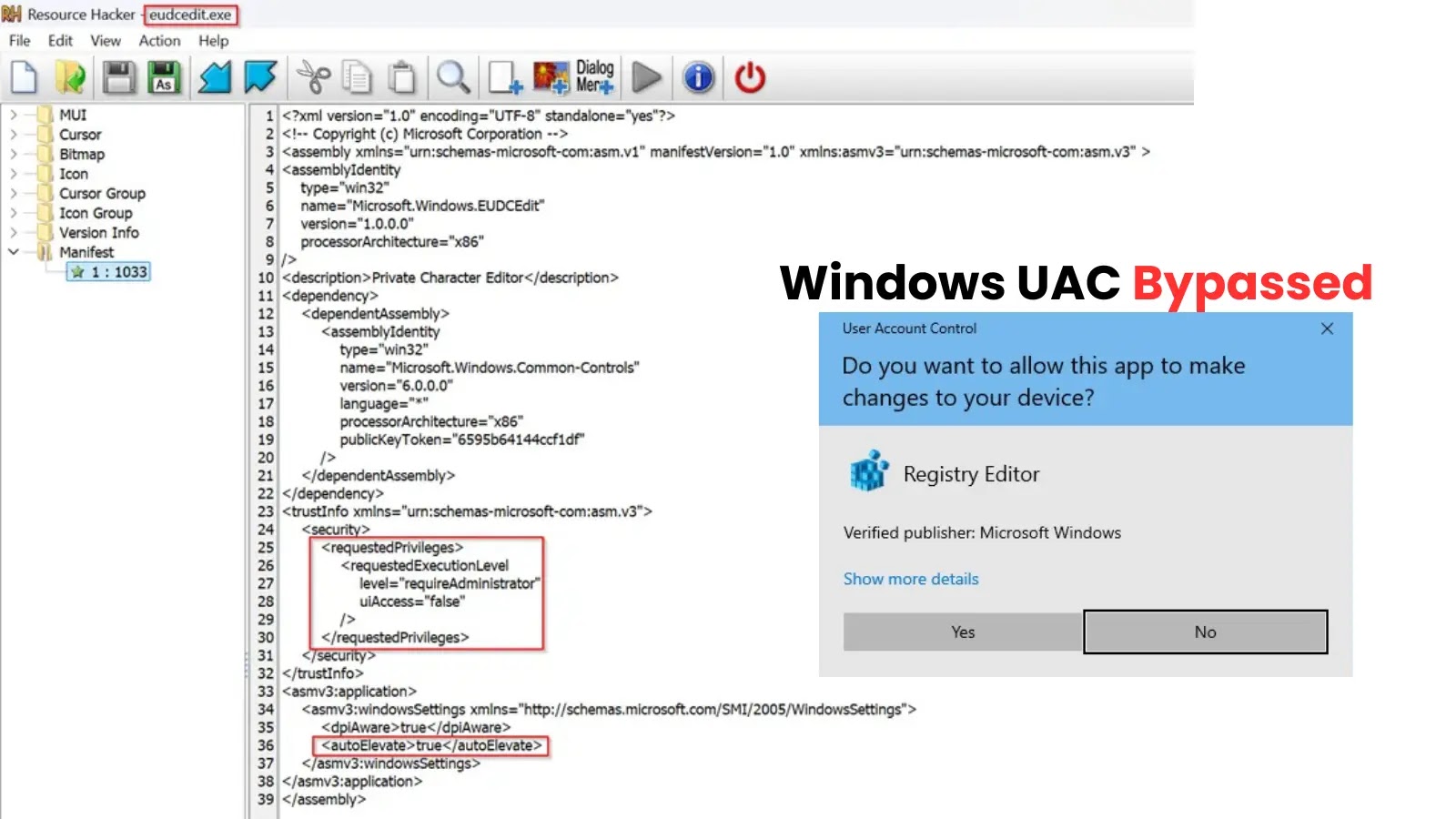
Unmasking the UAC Bypass: Private Character Editor Exploited for Privilege Escalation System administrators and cybersecurity professionals globally are no stranger to the persistent challenge [...]
The Silent Menace: Threat Actors Weaponizing Malicious Go Packages Supply chain attacks represent a critical and escalating threat in the cybersecurity landscape. Unlike traditional [...]
The digital frontier of cryptocurrency, while promising immense innovation, also presents a fertile ground for sophisticated cyberattacks. Imagine logging into your trusted crypto wallet, only [...]
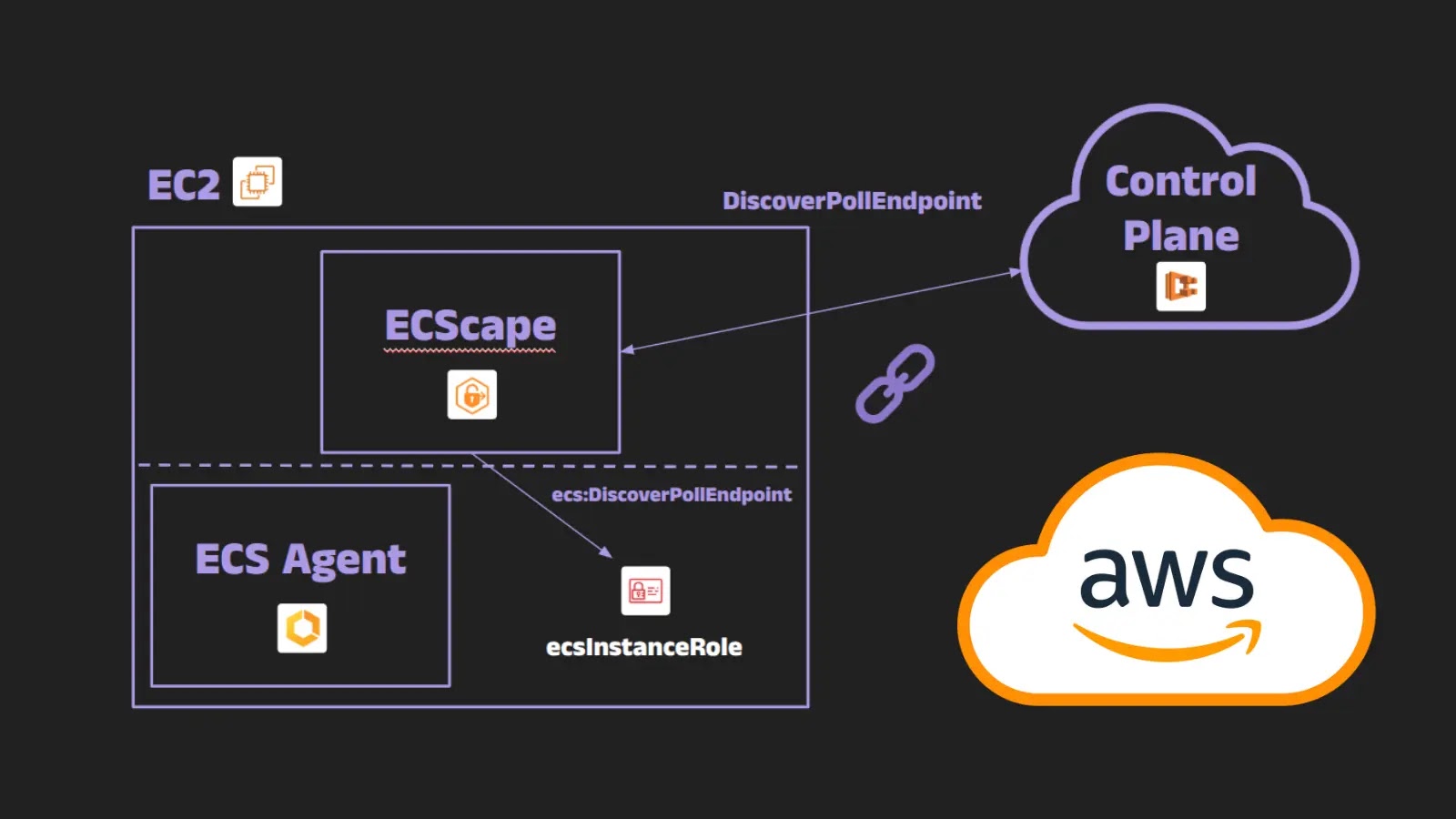
Cloud environments offer unprecedented scalability and flexibility, but they also introduce complex security challenges. A recent discovery, dubbed “ECScape,” highlights a significant vulnerability within [...]
Unveiling ChatGPT-5: A New Era in AI Agent Technology The landscape of artificial intelligence is experiencing a seismic shift with the official release of [...]
Urgent Action Required: CISA Mandates Immediate Patching of Critical Exchange Server Vulnerability (CVE-2025-53786) The cybersecurity landscape is in constant flux, and organizations must remain [...]
The digital landscape is under constant siege, with threat actors continually innovating new methods to bypass defenses. A concerning new trend has emerged: cybercriminals [...]
The long arm of justice often moves slowly, but for sophisticated cybercriminals, it invariably catches up. A recent extradition from France to the United States [...]
In an era where every new cybersecurity headline seems to scream “zero-day,” a recent statement from SonicWall has brought a crucial perspective to light. [...]