Urgent Alert: Critical CrushFTP 0-Day RCE Vulnerability Unleashes Unauthenticated Access The cybersecurity landscape has been rocked by the disclosure of a severe zero-day vulnerability [...]
Unveiling Gunra Ransomware’s Linux Evolution: A New Threat Landscape Emerges The cybersecurity landscape faces a persistent and evolving challenge from ransomware operators. Among the [...]
The digital landscape is a constant battleground, with ransomware threats lurking around every corner. For victims ensnared in the加密 web of data encryption, the [...]
Alleged Nokia Breach: A Deep Dive into the Tsar0Byte Claim and Third-Party Risk The digital landscape is a relentless battleground, and even global giants [...]
Navigating the Threat: NestJS Vulnerability Exposes Developer Machines to RCE Attacks In the evolving landscape of software development, frameworks are the bedrock upon which [...]
Enterprises globally rely on powerful infrastructure automation tools to streamline operations and manage vital secrets. When a critical vulnerability surfaces within such a foundational [...]
Raspberry Robin’s Persistent Evolution: Exploiting Windows Vulnerabilities The cybersecurity landscape faces a persistent and evolving threat as Raspberry Robin, a sophisticated malware downloader also [...]
Streamlining SOC Operations: How Top CISOs Combat Alert Fatigue and Uncover Real Threats In the relentless pursuit of robust security, many organizations invest heavily [...]
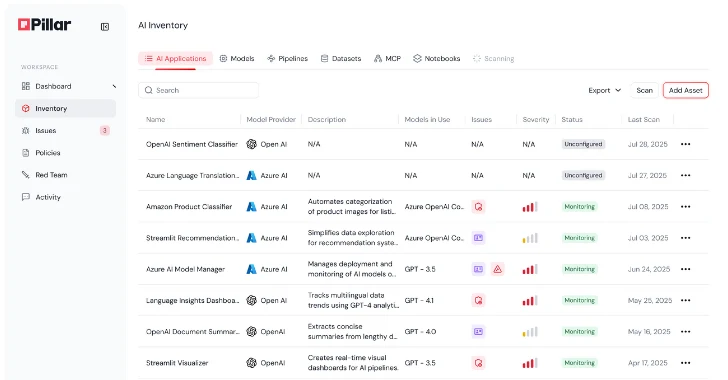
The rapid advancement of Artificial Intelligence (AI) has brought unprecedented capabilities to various industries. However, this evolution also introduces novel and complex security challenges. [...]
Hackers Can Manipulate BitLocker Registry Keys Via WMI to Execute Malicious Code as Interactive User
Unmasking BitLocker’s Hidden Lateral Movement Vulnerability: A Deep Dive for Security Professionals In the intricate landscape of cybersecurity, attackers consistently evolve their tactics, leveraging [...]