The landscape of artificial intelligence security is in constant flux, with new vulnerabilities emerging as rapidly as the technology itself evolves. A recent discovery [...]
In a startling revelation that underscores the subtle yet potent vulnerabilities within modern AI systems, new research from Trail of Bits has exposed a [...]
Unmasking APT36: Weaponized .desktop Files Target Indian BOSS Linux Systems The digital defense perimeter of India faces a sophisticated new threat. In early August [...]
Unpacking the WhatsApp Desktop Code Execution Threat A significant security flaw has emerged, placing WhatsApp Desktop users on Windows PCs at risk of arbitrary [...]
Urgent Alert: Chrome 0-Day Vulnerability Exploited in the Wild – PoC Released In the high-stakes world of digital security, a swift response to vulnerabilities [...]
WinRAR 0-Day Vulnerabilities Exploited in Wild: A Critical Case Study for Cybersecurity Professionals The recent revelation of two critical zero-day vulnerabilities within WinRAR, a [...]
The digital storefronts we frequent, processing our transactions and housing our personal data, are increasingly lucrative targets for cybercriminals. The recent incident at French [...]
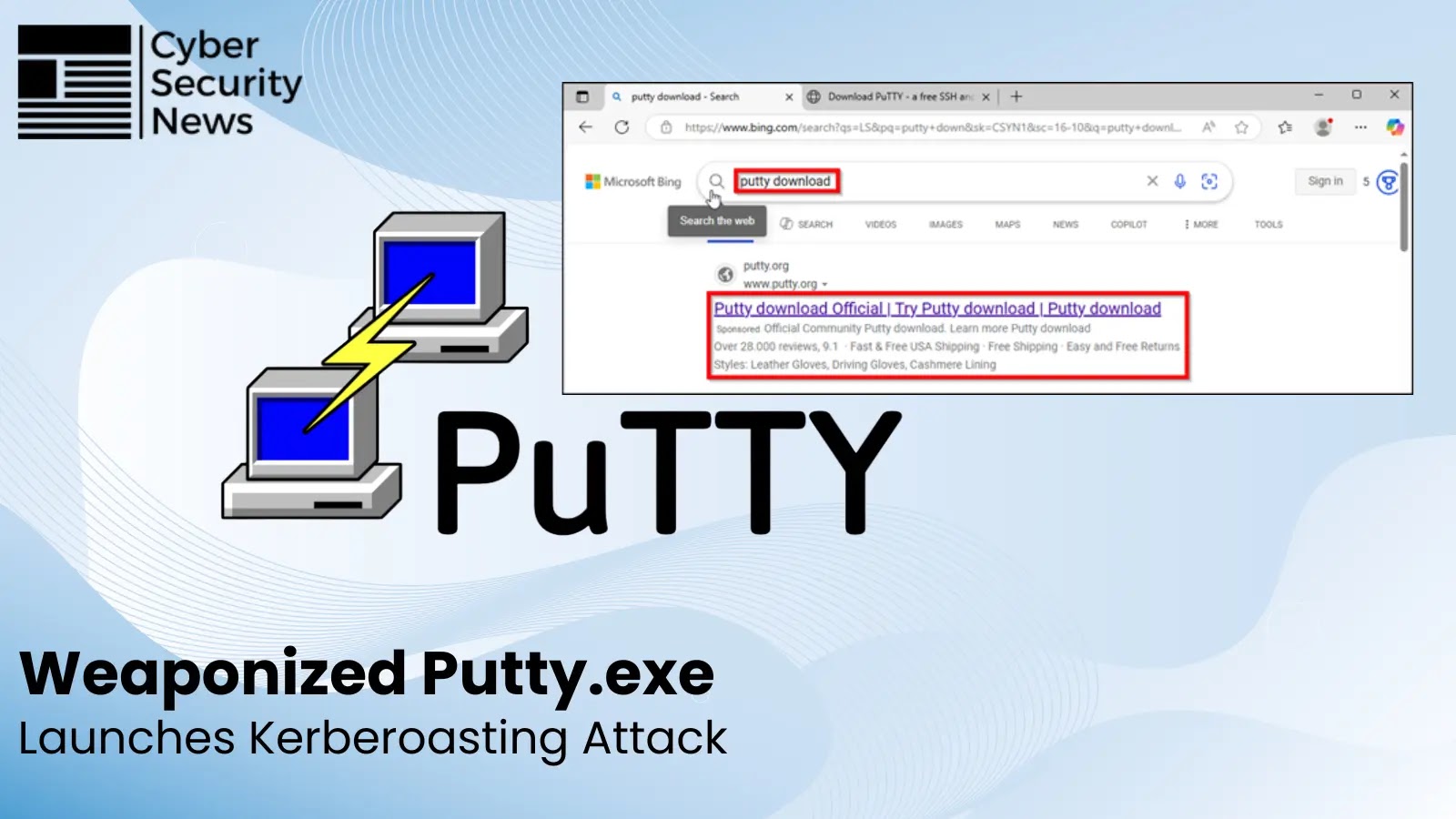
The Silent Compromise: Weaponized PuTTY, Bing Ads, and the Active Directory Assault In the evolving landscape of cyber threats, the sophistication of attack vectors [...]
In an era where digital privacy is increasingly scrutinized, a recent comprehensive analysis of the top social media platforms has brought to light a [...]
Stealthy Espionage: UNC6384 Leverages Valid Code Signing Certificates for Covert Operations In the evolving landscape of cyber warfare, advanced persistent threats (APTs) continually refine [...]