—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Apple Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Apple iOS [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple buffer overflow vulnerabilities in Dahua Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected [...]
The cybersecurity landscape has just been reshaped. In a monumental move with far-reaching implications, Palo Alto Networks, a titan in network security, has announced its [...]
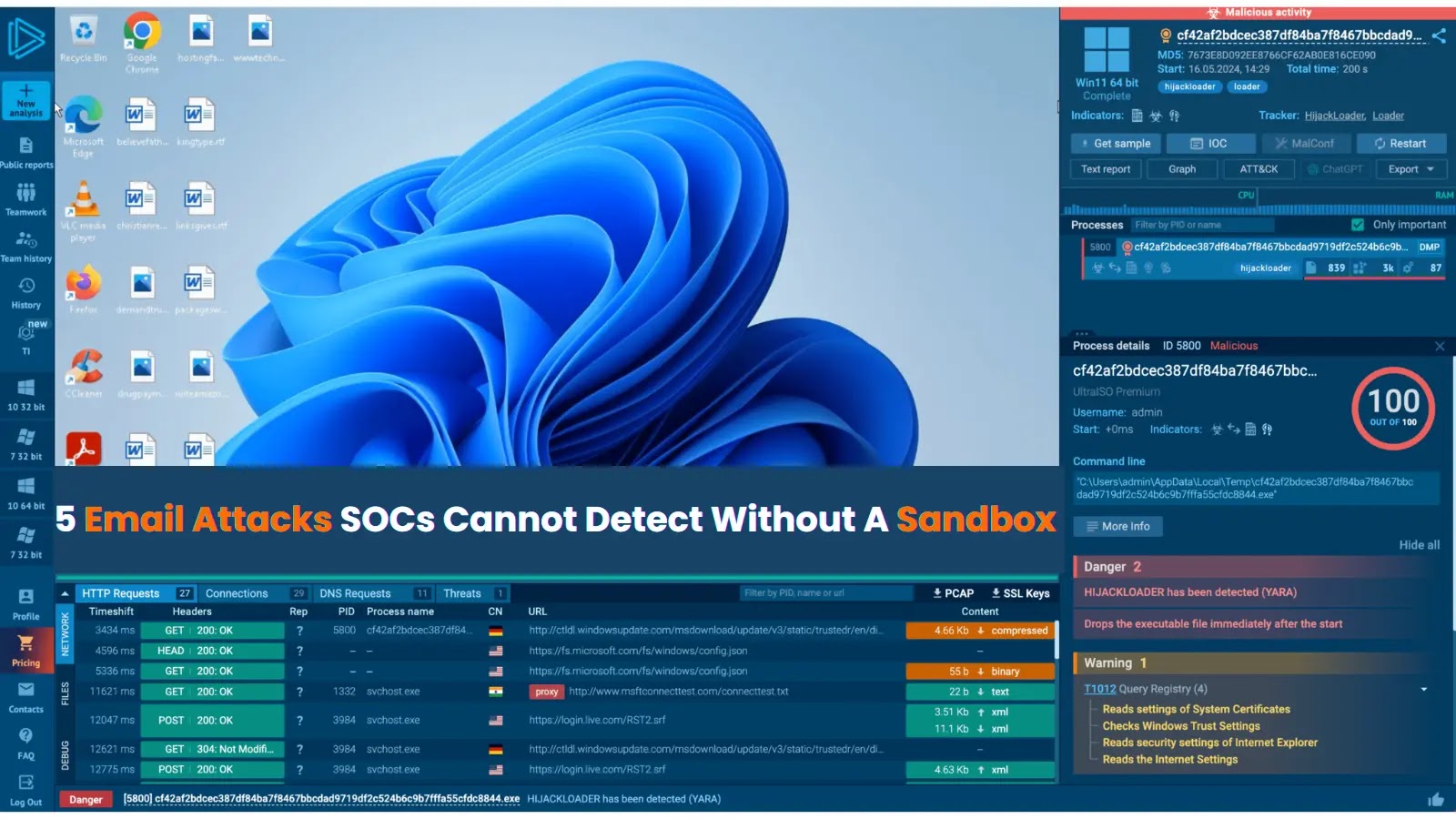
Despite the proliferation of collaboration tools like Slack and Microsoft Teams, email steadfastly remains the single most exploited attack vector for organizations globally. Its [...]
The digital threat landscape is in a constant state of flux, with threat actors continuously refining their methodologies to bypass hardened defenses. A recent and [...]
The cybersecurity landscape is a perpetual arms race, and threat actors, particularly sophisticated ransomware groups like LockBit, are consistently refining their tactics to breach [...]
The Unyielding Email Frontline: Securing Your Enterprise in 2025 The digital perimeter of every organization faces an increasingly sophisticated onslaught. In 2025, attackers wield advanced [...]
Lazarus Subgroup ‘TraderTraitor’: Unpacking the Threat to Cloud Platforms and Supply Chains In an era where digital infrastructure is increasingly cloud-centric and supply chains [...]
The security of our physical spaces increasingly relies on the robustness of the digital infrastructure underpinning them. When vulnerabilities surface in widely deployed surveillance [...]
Unveiling the Critical Role of Website Monitoring Tools in 2025 In the relentless pursuit of seamless digital experiences, website performance is paramount. Downtime, sluggish [...]