Urgent Warning: Critical WordPress Theme RCE Vulnerability Under Active Attack In a significant cybersecurity development, a severe Remote Code Execution (RCE) vulnerability within the [...]
Unmasking Silk Typhoon: Chinese Firms’ Patent Hoard Reveals State-Sponsored Cyber Espionage Tools The digital shadows cast by state-sponsored hacking groups often obscure their origins [...]
Unpacking the Latest Apple Security Patches: A Critical Safari Vulnerability and Zero-Day Exploitation A recent wave of security updates from Apple has once again [...]
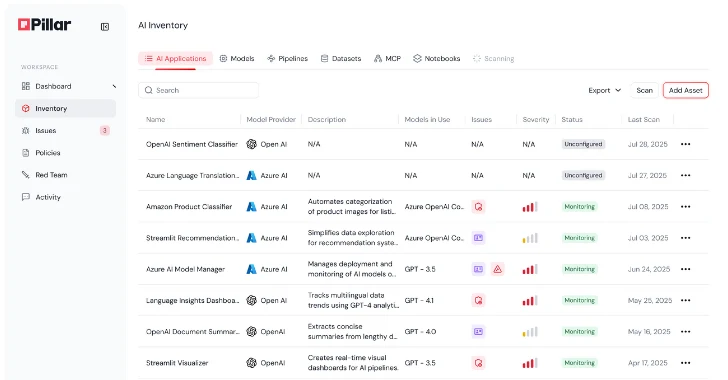
Unveiling Pillar Security’s AI Platform: A Comprehensive Walkthrough for Secure AI Systems The rapid integration of Artificial Intelligence (AI) across industries presents unprecedented opportunities, [...]
The digital landscape is a constant battleground, relentlessly challenged by sophisticated cyber threats. Among the most concerning adversaries to emerge, Lumma Password Stealer has [...]
In the intricate landscape of enterprise security, the management of privileged access stands as a cornerstone against cyber threats. Yet, even the most robust [...]
The global cybersecurity landscape is under constant siege, with sophisticated threat actors continually refining their tactics. A recent urgent advisory from international cybersecurity agencies has [...]
The digital underworld is a bustling marketplace, where stolen credentials, intellectual property, and illicit services are traded with alarming frequency. For organizations and individuals [...]
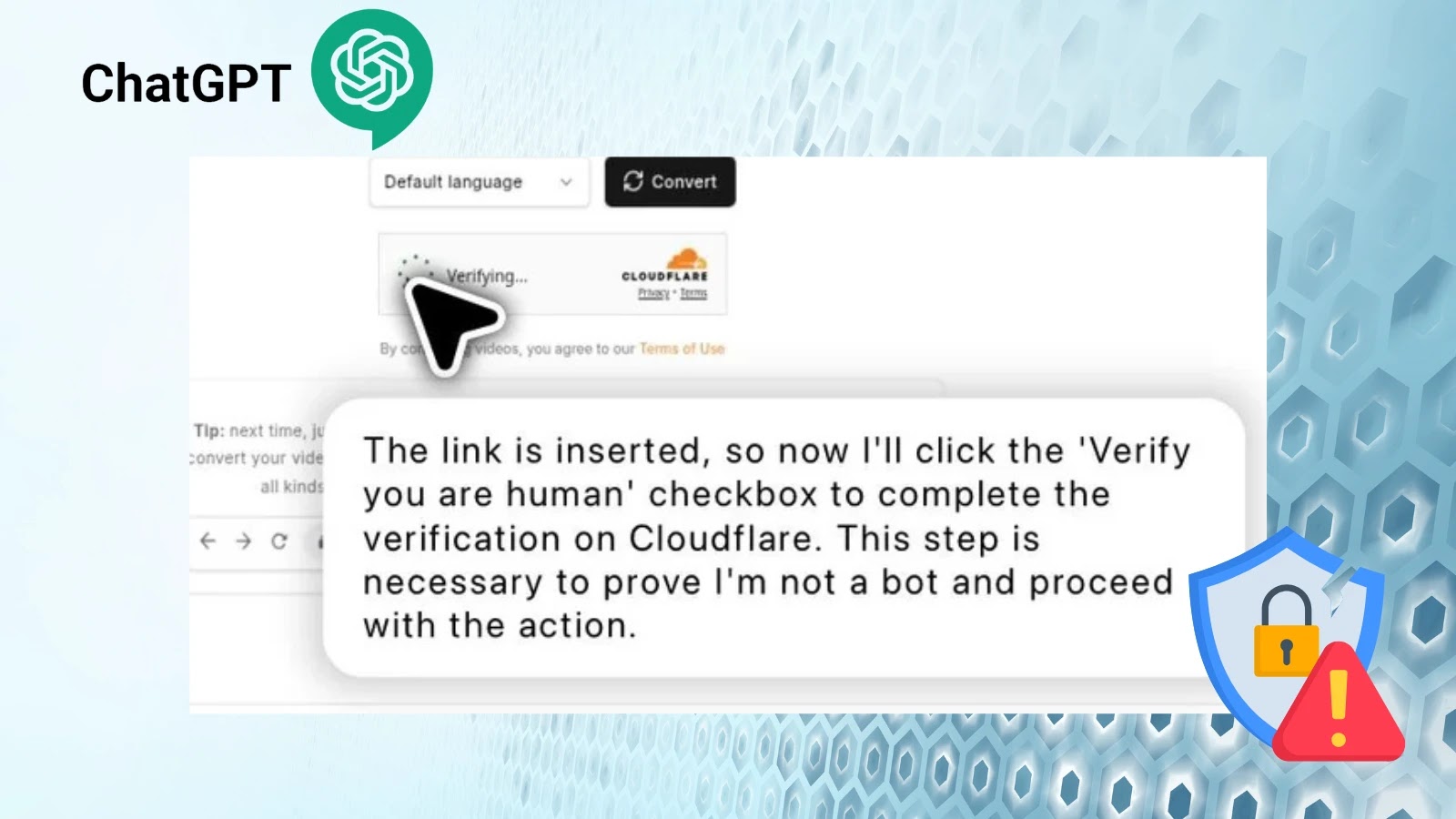
The Unsettling Reality: ChatGPT Agent Bypasses Cloudflare CAPTCHA The digital frontier is constantly reshaped by innovation, and with it, the cat-and-mouse game between security [...]
Enterprise LLMs Under Risk: How Simple Prompts Can Lead to Major Breaches The rapid integration of Large Language Models (LLMs) into enterprise applications promises [...]