The cybersecurity landscape is in a constant state of flux, with threat actors continuously refining their strategies to breach defenses. A recent and particularly concerning [...]
In a significant development for the cybersecurity landscape, a new threat actor, dubbed Storm-2603, has been identified deploying a sophisticated backdoor framework, AK47 C2 [...]
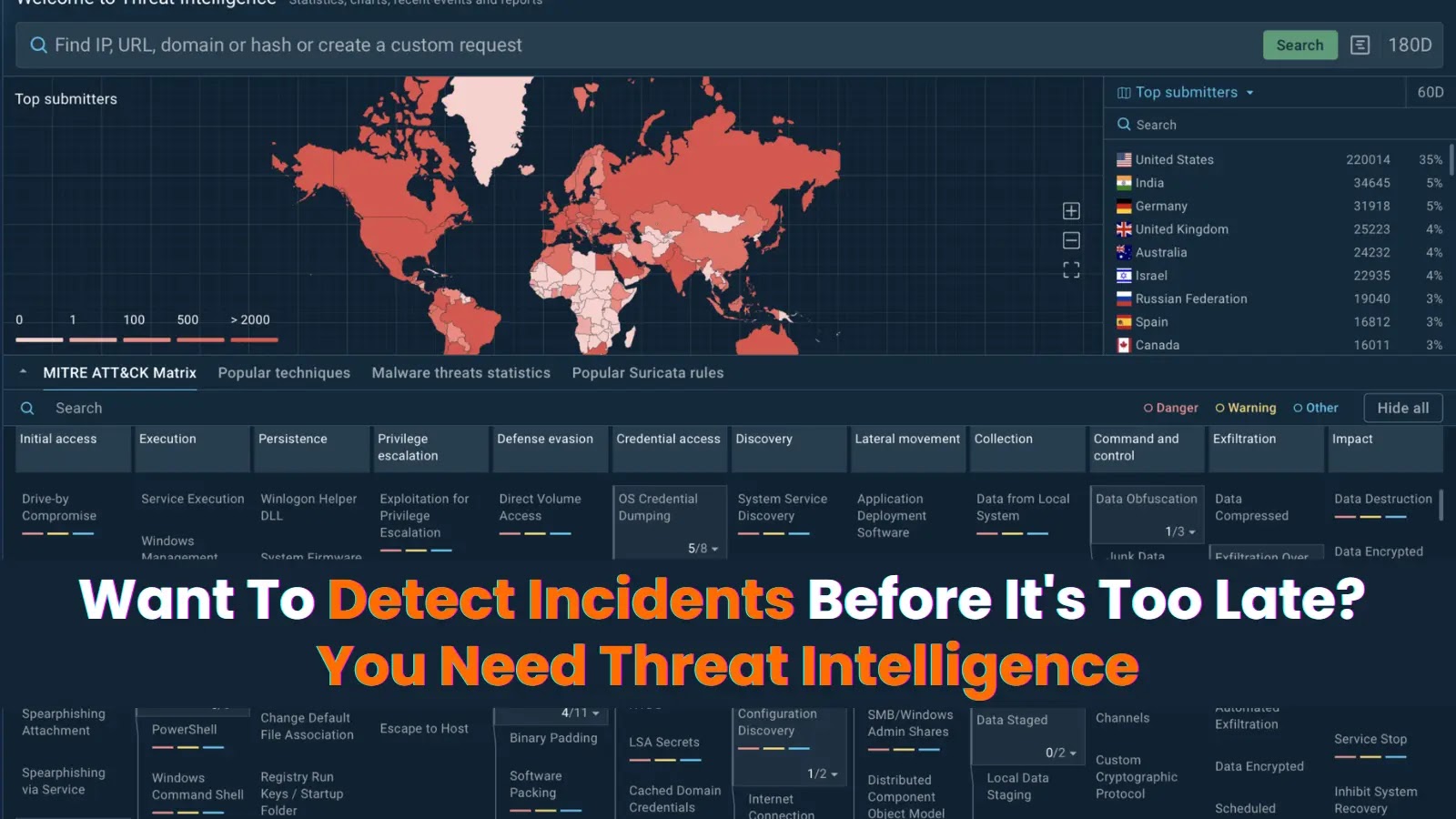
Want To Detect Incidents Before It’s Too Late? You Need Threat Intelligence The difference between a minor security incident and a devastating breach often [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Sonicwall Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected SonicOS SMA100 series [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in Drupal Modules Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Drupal Real-time [...]
The Critical Role of Anti-Phishing Tools in 2025 Phishing attacks remain a persistent and evolving threat, consistently ranking among the most common and damaging [...]
The Silent Saboteur: When EDR Becomes a Weapon Against Itself The digital defense landscape is in a constant state of flux, with security solutions [...]
Unveiling the Criticality of Kubernetes Monitoring in 2025 In the complex landscape of modern cloud-native applications, Kubernetes has emerged as the definitive standard for [...]
In the intricate landscape of global cybersecurity, the evolving tactics of state-sponsored threat actors represent a persistent and significant challenge. North Korean cybercriminals, in [...]
Thousands of SharePoint Servers Exposed: A Critical Internet-Facing Threat The digital landscape is constantly shifting, and with it, the pervasive threat of cyberattacks intensifies. [...]