Unmasking Phantom Net Voxel: APT28’s Signal-Based Offensive In a landscape where digital communication is increasingly critical, the discovery of a sophisticated spearphishing campaign targeting [...]
A chilling revelation has sent ripples through the WordPress community: a critical authentication bypass vulnerability has been discovered in the Case Theme User WordPress plugin. [...]
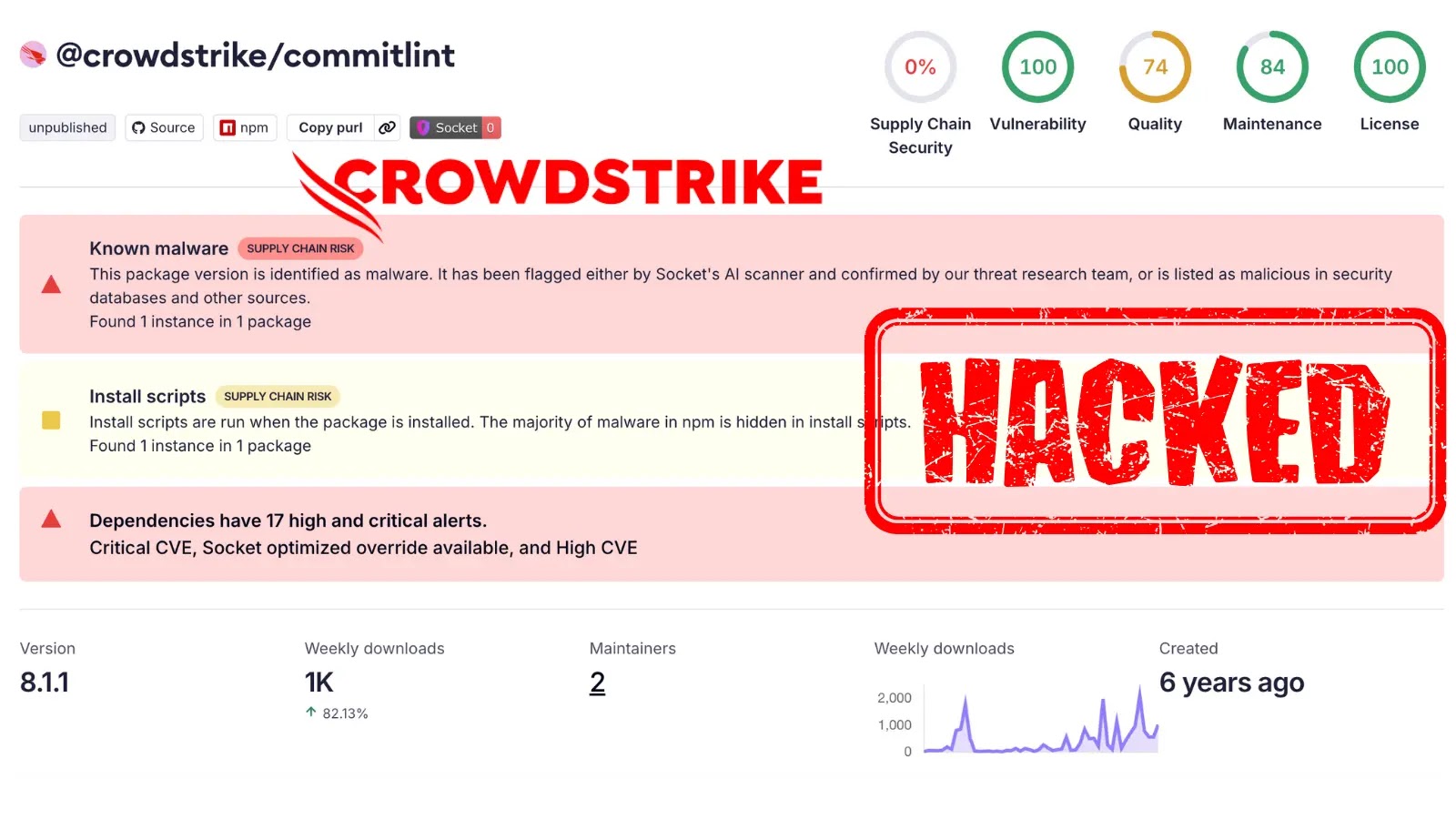
The digital supply chain, a critical lifeline for modern software development, has once again been targeted. A recent campaign, dubbed the “Shai-Halud attack,” has [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Schneider Electric Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: MEDIUM Software Affected ATV630/650/660/680/6A0/6B0/6L0 Altivar [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Apple Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: High Software Affected Apple iOS [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Denial of Service Vulnerability in CISCO Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Cisco [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Image Verification Bypass Vulnerability in CISCO Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Component Affected ASR [...]
Unmasking the Authorization Bypass: Spring Framework’s Critical Security Flaws In the intricate world of enterprise application development, Spring Framework stands as a cornerstone, empowering [...]
The rapid integration of AI assistants and development tools has undeniably revolutionized how we interact with technology. Beneath the surface of enhanced productivity, however, new [...]
Unmasking AWSDoor: A New Era of Cloud Persistence The digital frontier of cloud computing, while offering unparalleled flexibility and scalability, also presents a constantly [...]