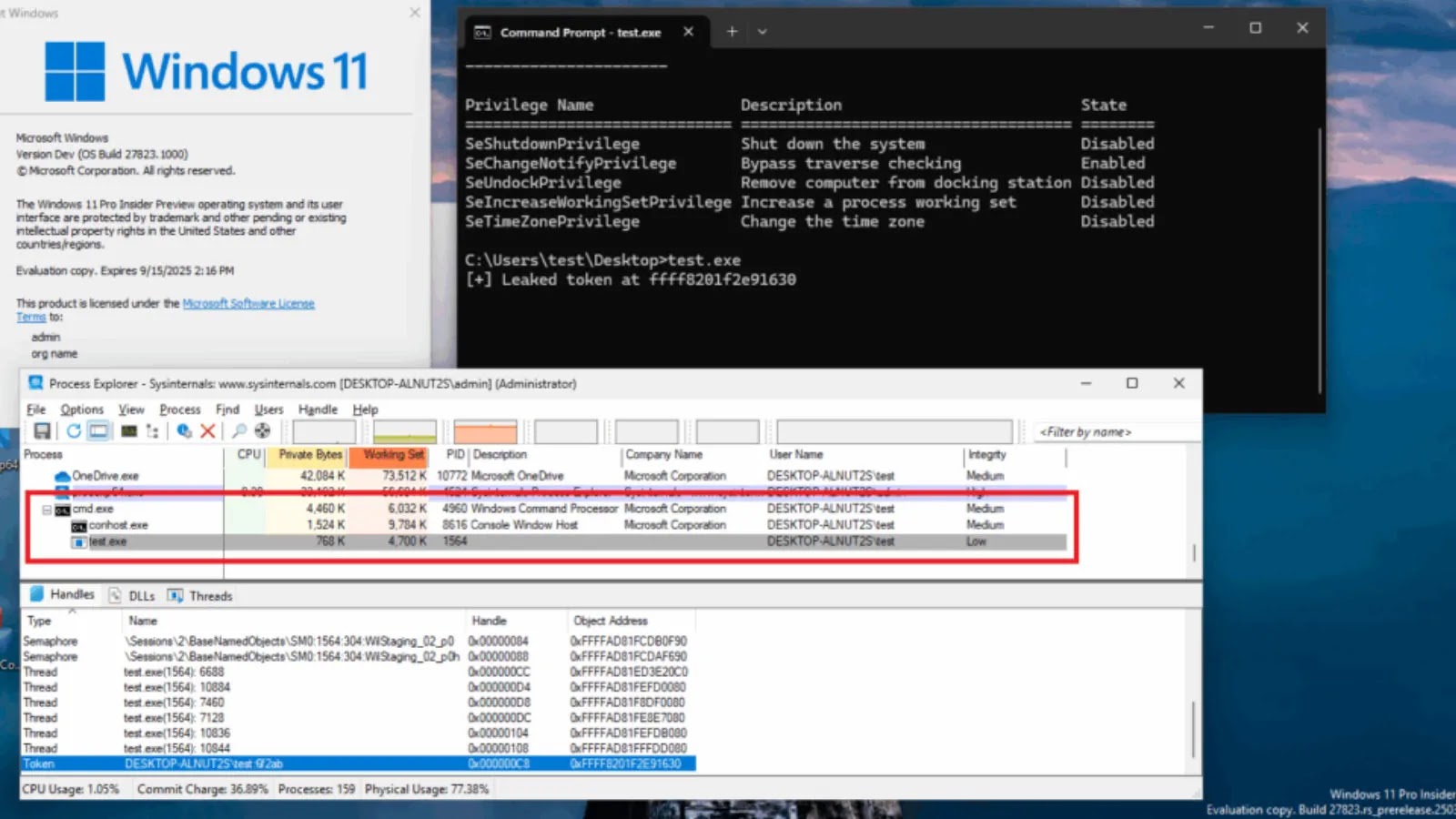
In the intricate landscape of cybersecurity, even the most fundamental components of an operating system can harbor critical vulnerabilities. Recently, Microsoft addressed a concerning [...]
A New Frontier for Adversaries: Malware Hides in Azure Functions The cybersecurity landscape is constantly shifting, with threat actors continually innovating to evade detection. [...]
In the intricate world of cybersecurity, a fix for one vulnerability can, at times, inadvertently introduce another. Such is the paradoxical nature of software [...]
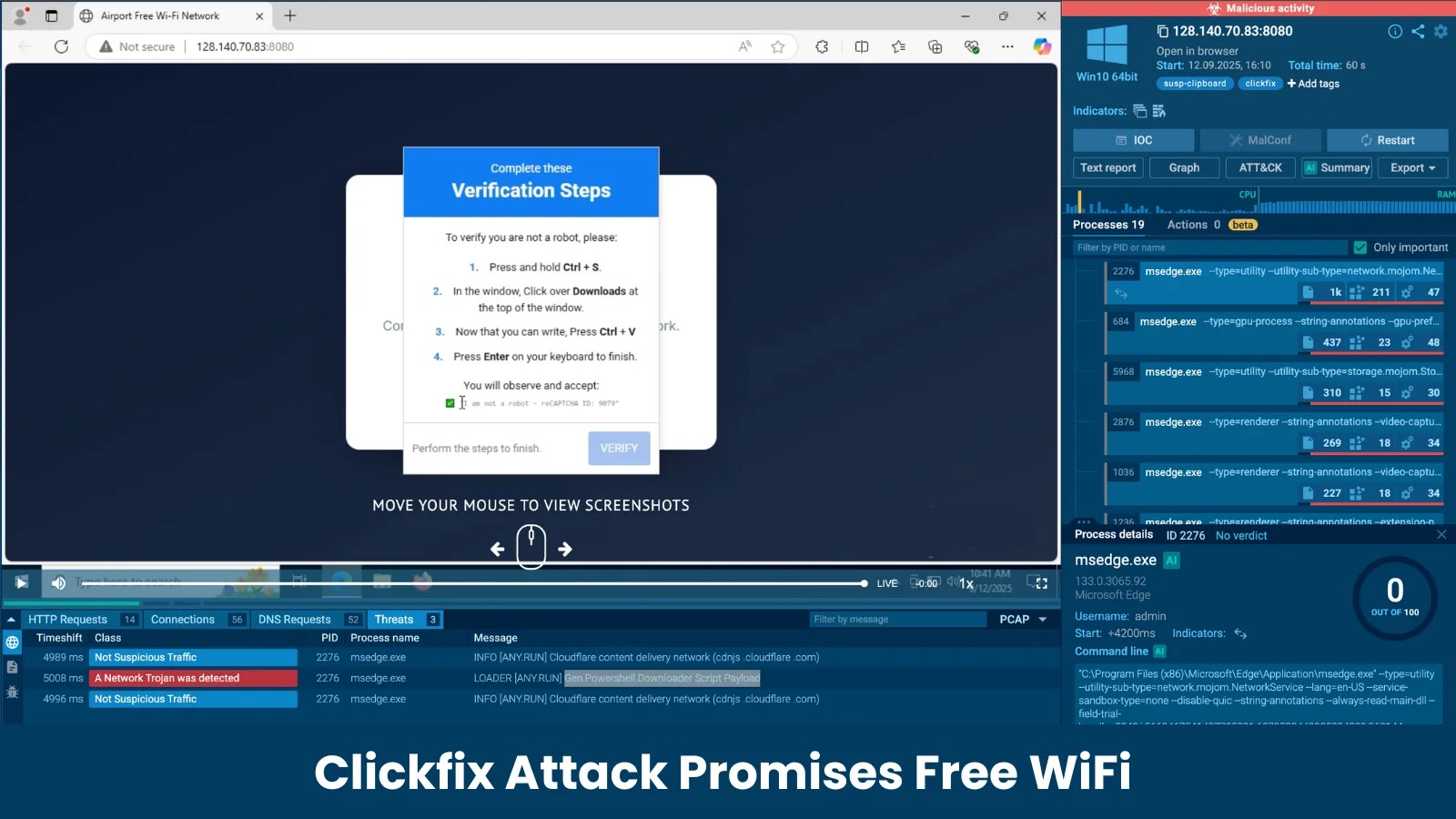
The Deceptive Lure of “Free WiFi”: Unpacking the Clickfix Attack In an increasingly connected world, the promise of free internet access often proves irresistible. [...]
The digital threat landscape constantly shifts, and attackers are always refining their methods to bypass existing defenses. A recent discovery by cybersecurity researchers highlights this [...]
A disturbing trend in cybercrime has surfaced, exposing a sophisticated malvertising campaign that weaponizes GitHub repositories to distribute malware. This isn’t your typical phishing [...]
Buterat Backdoor: A Persistent Threat to Enterprise Security Enterprise networks are under constant siege. Among the myriad of digital threats, sophisticated backdoor malware represents [...]
In the intricate landscape of network security, choosing the right tools is paramount. Security professionals face an increasingly complex threat environment, and the ability [...]
Organizations worldwide rely on Salesforce to power their critical business operations, managing everything from customer relationships to vital sales data. This reliance makes Salesforce [...]
This week’s cybersecurity news delivers a stark reminder of the interconnected vulnerabilities inherent in our digital infrastructure. Even industry leaders dedicated to security are [...]