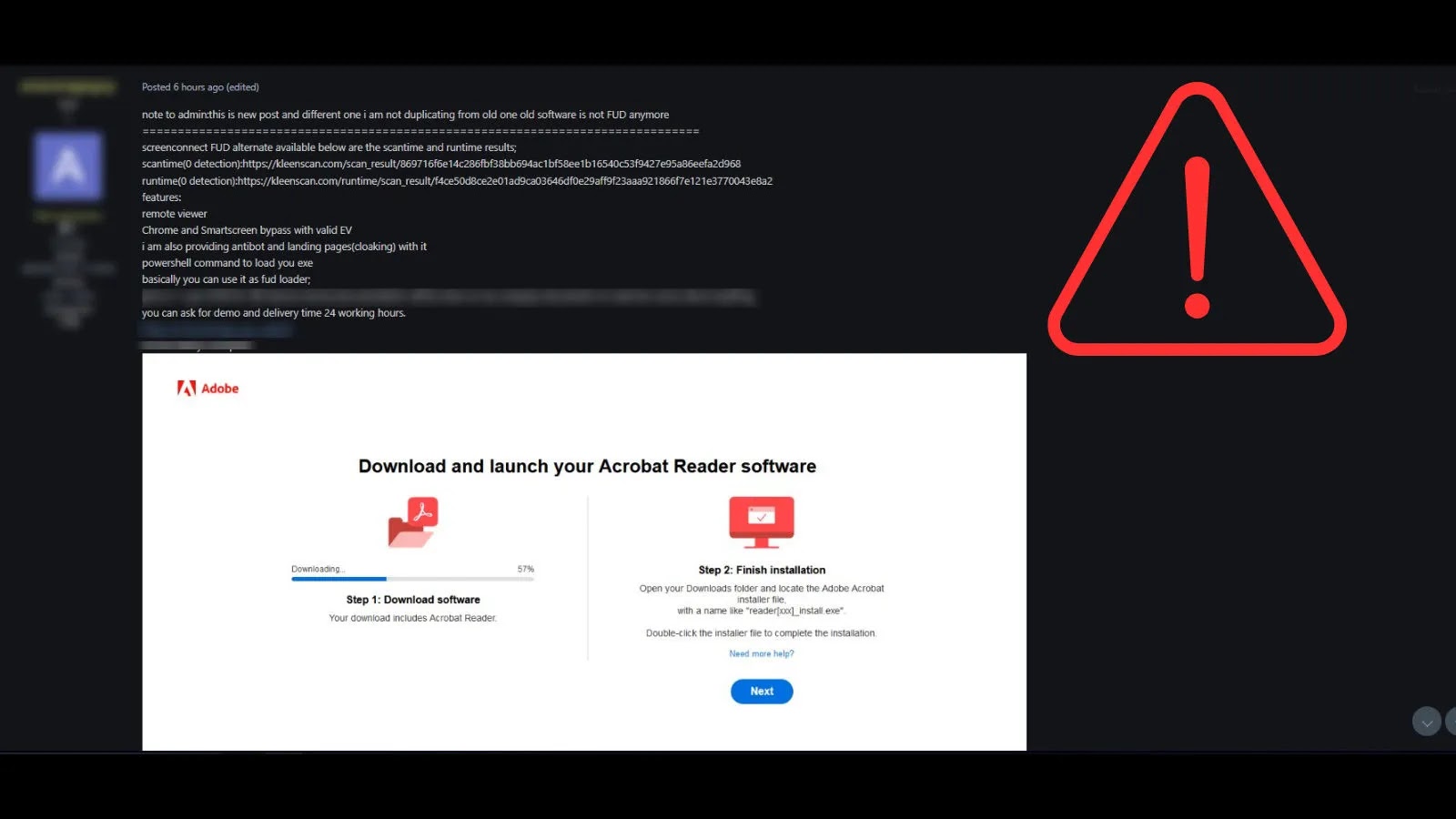
A disturbing new trend has emerged in the cybersecurity landscape, highlighting the sophisticated tactics adversaries are now employing. Security teams globally are grappling with [...]
The cybersecurity landscape is in a perpetual state of flux, with threat actors consistently innovating to bypass established defenses. A concerning new development has [...]
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical warning that demands immediate attention from organizations leveraging Ivanti Endpoint Manager Mobile (EPMM) systems. [...]
BreachLock’s Dual Recognition: Elevating Offensive Security in the Gartner Spotlight In the rapidly evolving cybersecurity landscape, proactive defense is paramount. Organizations are continually seeking [...]
Nokia CBIS/NCS Manager API Vulnerability: A Critical Authentication Bypass Exploit A significant security flaw has recently come to light, impacting Nokia’s widely used CloudBand [...]
The AI-Powered Phishing Threat: Deception Redefined The landscape of cyber threats is constantly shifting, but few attack vectors have proven as persistently effective as [...]
The landscape of cyber warfare is in constant flux, with threat actors continuously refining their tactics and forging new alliances. A recent, deeply concerning development [...]
In the relentlessly expanding digital landscape, Application Programming Interfaces (APIs) form the bedrock of modern online operations, facilitating seamless service integration and pioneering novel customer [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Atlassian Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: High Software Affected Confluence Data [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Microsoft Edge Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Microsoft Edge [...]