Unmasking the Threat: iOS Video Injection Bypasses Biometric Security on Jailbroken iPhones Digital identity verification is a cornerstone of modern security, yet its robustness [...]
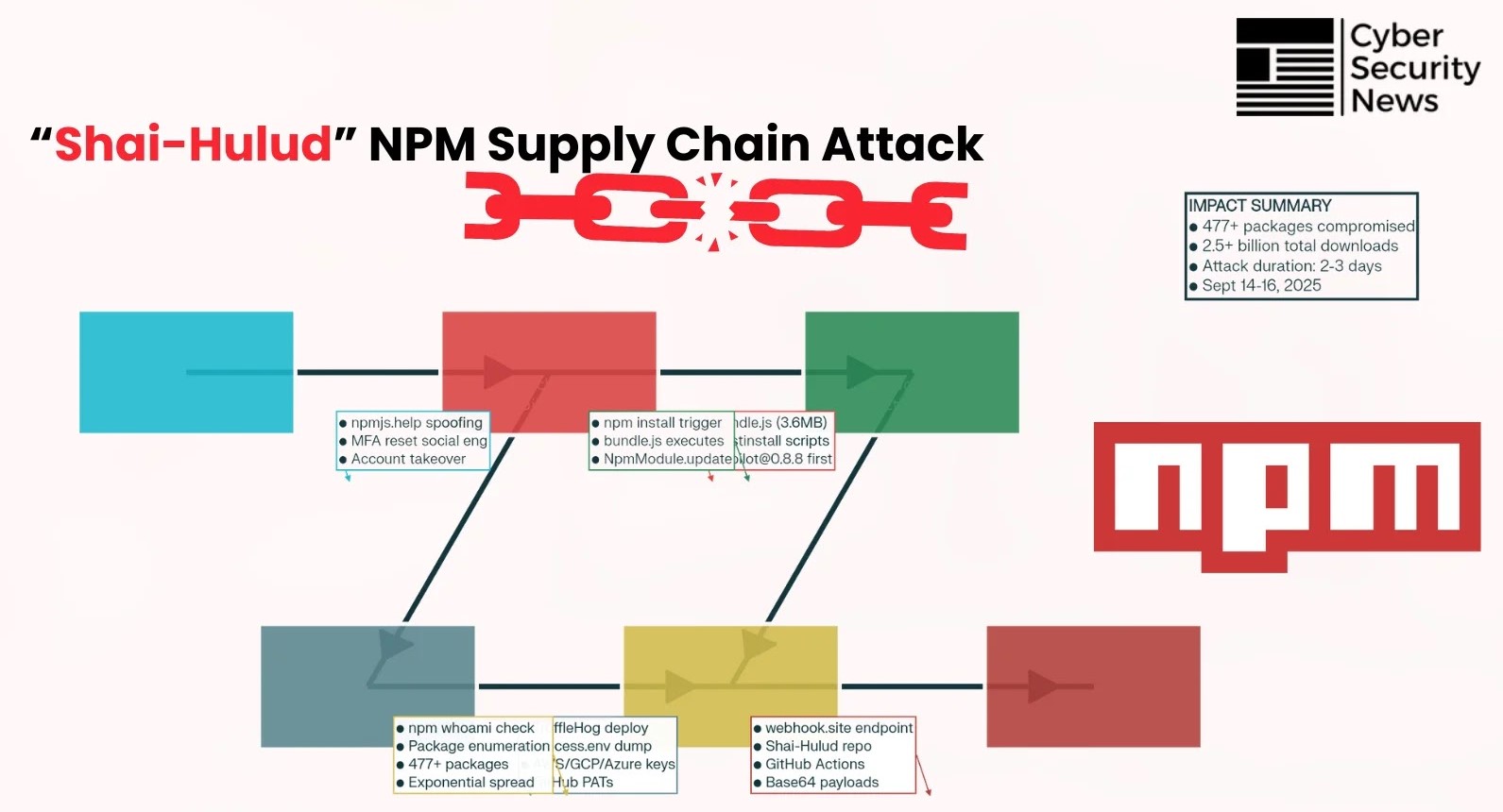
Unveiling Shai-Hulud: The npm Supply Chain Nightmare of 2025 The digital landscape witnessed a seismic shift in September 2025, as the JavaScript ecosystem was [...]
Jenkins Under Attack: Critical Patches Address Denial of Service and Information Disclosure Flaws In the high-stakes world of software development and continuous integration/continuous delivery [...]
The silent threat of data theft lurks in the digital shadows, and a new predator has emerged: Raven Stealer. This potent information-stealing malware is [...]
Detailed Comparison of Fortinet Products device: FortiAnalyzer 150G and 200F Upgrade Network Security Document In the ever-evolving landscape of network security, Fortinet stands as a [...]
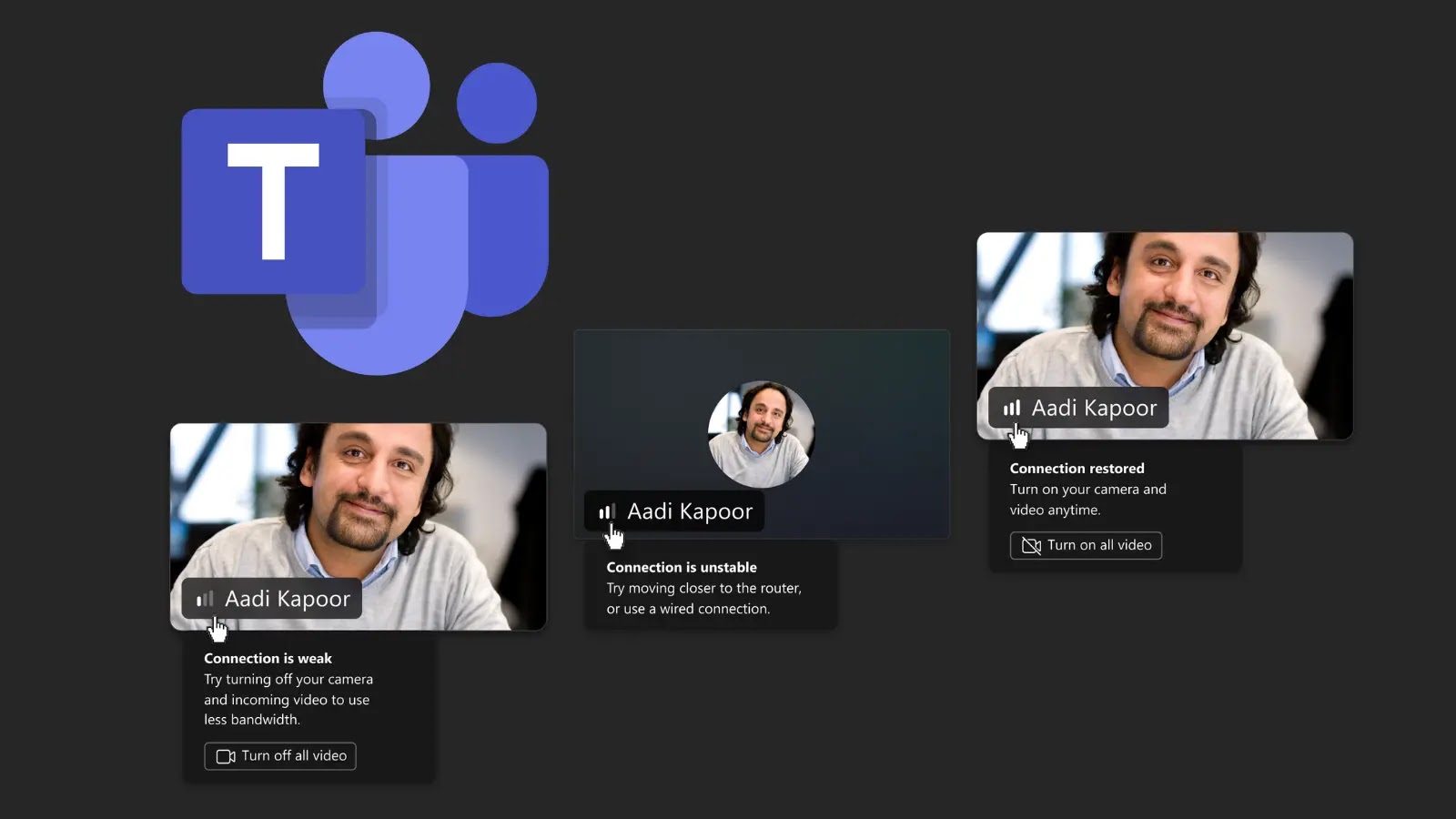
Navigating the Digital Dial Tone: Microsoft Teams’ Network Strength Indicator Explained In the evolving landscape of remote and hybrid work, seamless communication is paramount. [...]
Python developers navigate a landscape where innovation thrives, but so too does the sophistication of cyber threats. A particularly insidious tactic gaining traction is typosquatting, [...]
The landscape of cybercrime is shifting, and with it, our understanding of the adversary. For years, cybersecurity professionals have largely viewed ransomware groups as [...]
In a significant development that underscores the persistent threat of sophisticated cyber criminal organizations, the notorious Everest ransomware group has reportedly added Bayerische Motoren [...]
Unmasking the Browser’s Blind Spot: Palo Alto Networks Validates SquareX Research on SWG Limitations In the intricate landscape of enterprise security, Secure Web Gateways [...]