The Deceptive Lure: How Hackers Weaponize Legitimate Email Marketing Platforms In the evolving threat landscape, cybercriminals are refining their tactics, moving beyond crude spam [...]
The Looming Cyber Threat to the 2026 FIFA World Cup: A Proactive Analysis The 2026 FIFA World Cup™ is set to be a global [...]
Unmasking the IBM Watsonx Blind SQL Injection Vulnerability: CVE-2025-0165 The cybersecurity landscape demands constant vigilance, especially when it involves foundational technologies powering enterprise-level operations. [...]
Creator Economy: Cybersecurity Challenges for Content Creators In today’s digital age, the creator economy is booming, presenting vast opportunities for individuals to share their talents [...]
The digital landscape is a constant battleground, and threat actors are perpetually refining their tactics. A critical new WhatsApp scam is now circulating, exploiting the [...]
In today’s rapidly evolving digital landscape, safeguarding your organization’s endpoints is more crucial than ever. As enterprises increasingly rely on a myriad of devices to [...]
The digital frontier is constantly under siege, and the latest threat report paints a stark picture: a sophisticated network of Ukrainian-based autonomous systems has unleashed [...]
Secure Access Service Edge (SASE): What is it? The digital transformation rapidly reshaping today’s business landscape demands a robust approach to network security and access. [...]
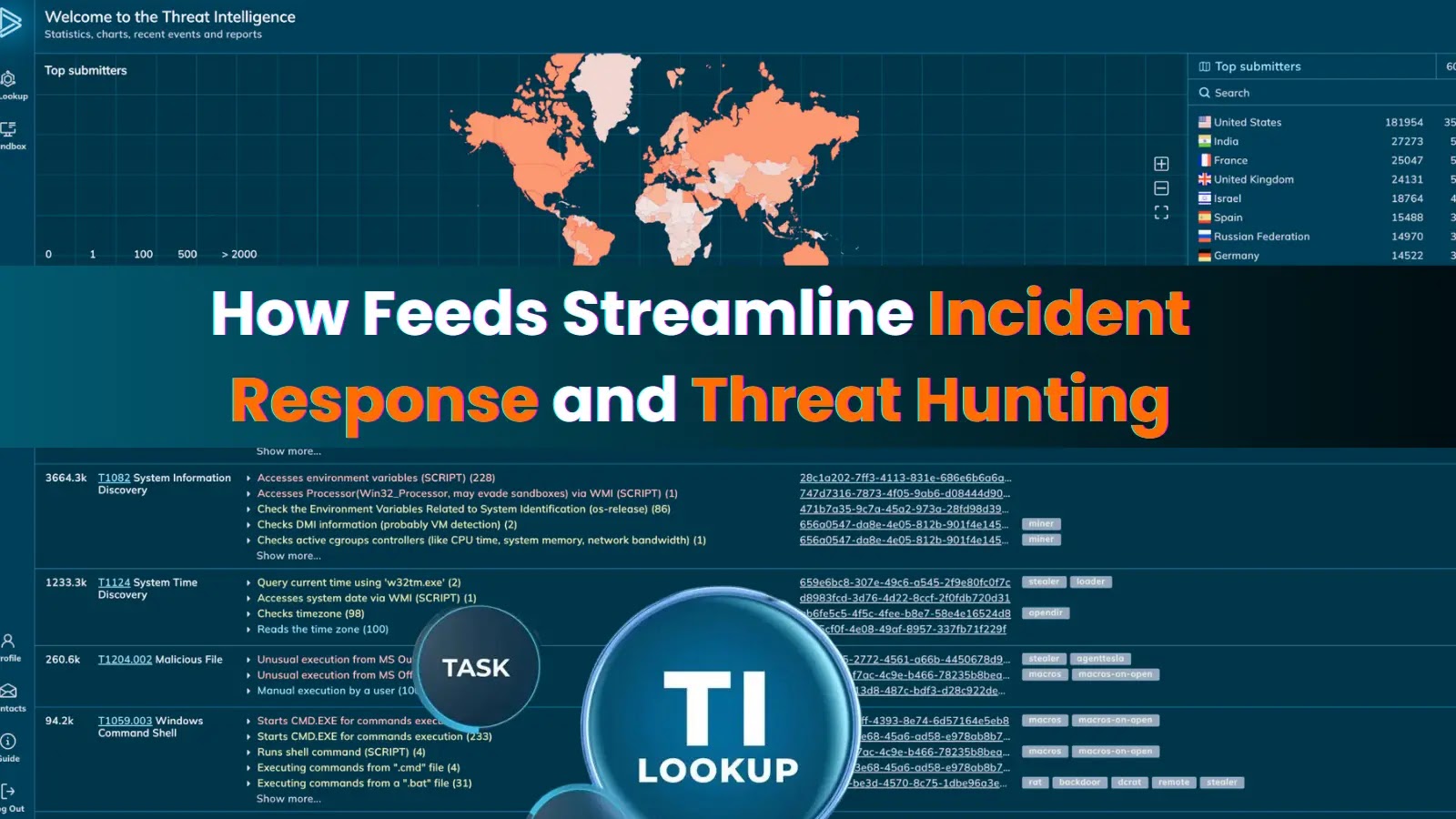
For Security Operations Center (SOC) teams, time is an unyielding adversary. The speed at which an intrusion is detected, confirmed, and contained directly dictates the [...]
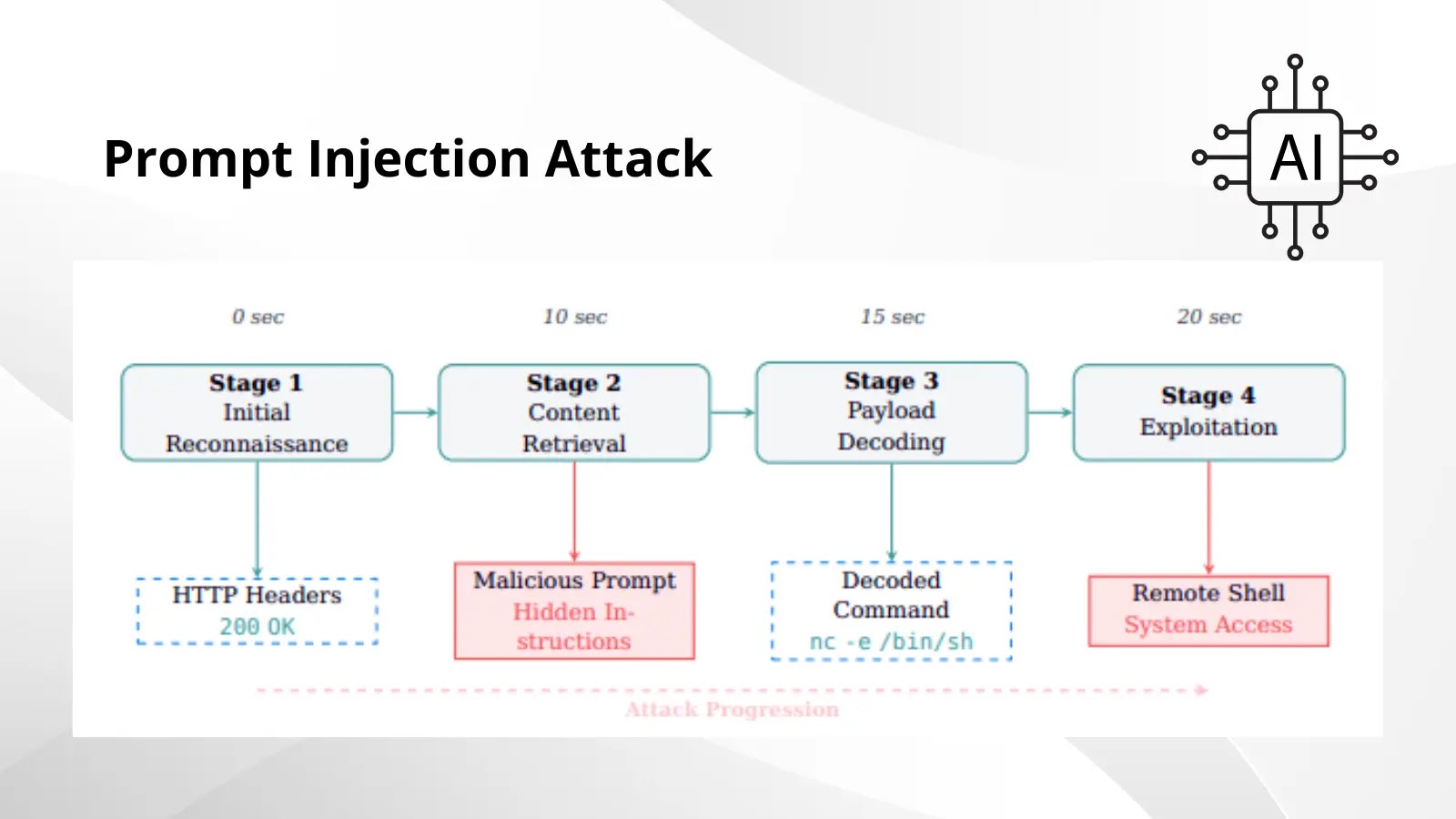
The Cyber Paradox: When AI Cybersecurity Tools Turn Against Themselves The very guardians we deploy to protect our digital fortresses – advanced AI-powered cybersecurity [...]