Unmasking CopyCop: Russia’s Escalating AI-Driven Disinformation Campaign The landscape of information warfare has taken a disturbing turn with the significant expansion of CopyCop, a Russian [...]
Unmasking GOLD SALEM: The Warlock Group’s Ransomware Onslaught The cybersecurity landscape has recently been shaken by the emergence of GOLD SALEM, an aggressive new [...]
SolarWinds Issues Advisory Regarding Salesloft Drift Security Incident In an evolving cybersecurity landscape, proactive communication and transparent reporting are paramount. SolarWinds, a leading provider [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in Google Chrome for Desktop Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected [...]
Why AI and Cybersecurity: Best Practices Security for Cyber Incident Response Plans In an era where cyber threats are evolving at an unprecedented pace, the [...]
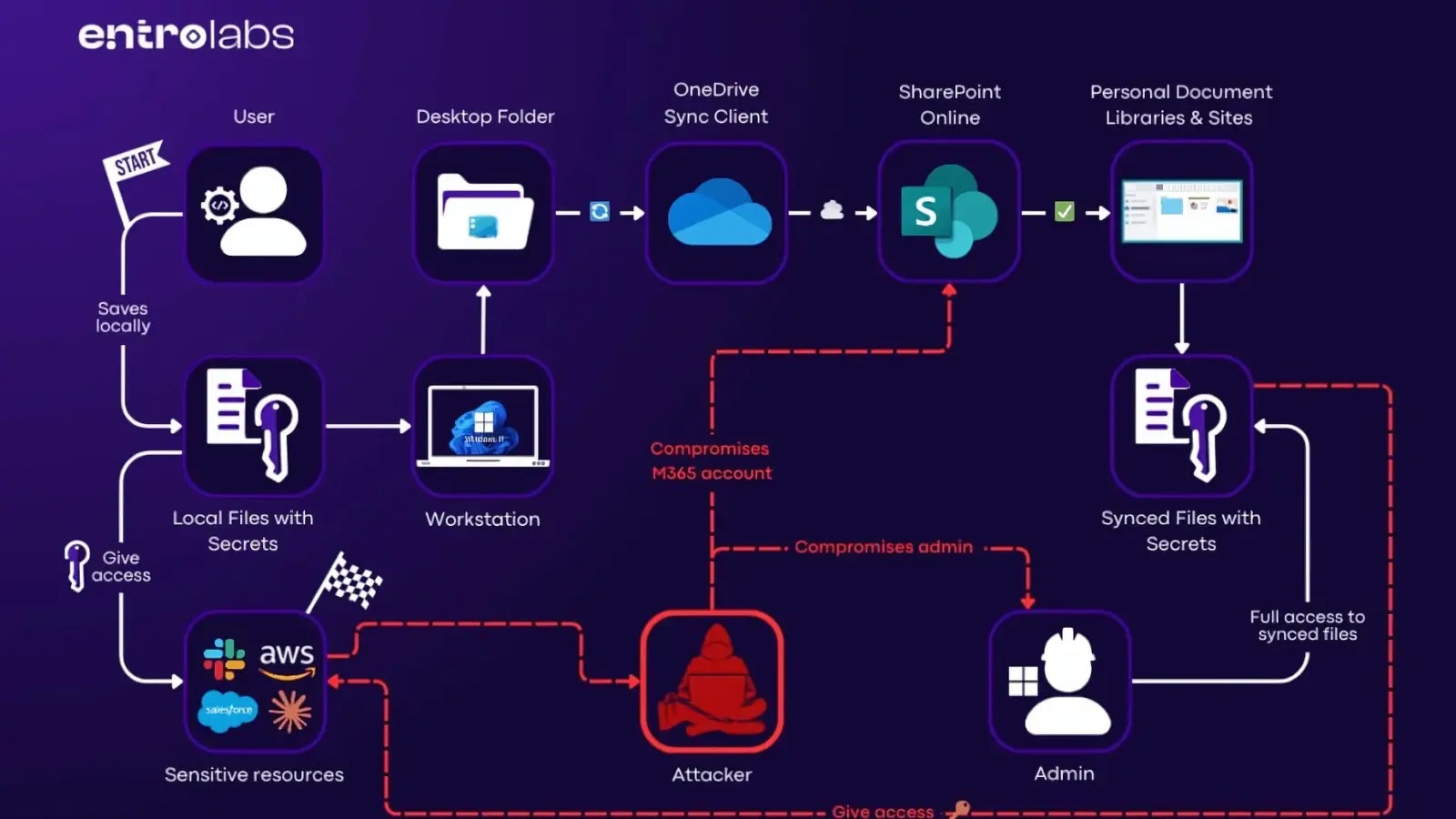
The ubiquity of cloud collaboration tools brings unparalleled efficiency to enterprises. However, this convenience often masks underlying security vulnerabilities. A recent discovery regarding Microsoft OneDrive’s [...]
The Pixie Dust Attack: Unmasking WPS Vulnerabilities in Your Router The security of our wireless networks is paramount, yet persistent vulnerabilities continue to emerge, exposing [...]
TP-Link Router Zero-Day RCE Exploit Bypasses ASLR: What You Need to Know The security landscape for connected devices has just seen a significant tremor. [...]
The digital frontier is constantly shifting, and with it, the strategies of cyber adversaries. We’re witnessing a pivotal transformation in attack methodologies, moving away [...]
Unpatched Peril: Apple Addresses Zero-Day Vulnerabilities in Legacy Devices The digital landscape is a constant battleground, where even trusted giants like Apple face relentless [...]