The Invisible Threat: FileFix Attack Leverages Steganography to Deliver StealC Malware A disturbing new cyber threat has emerged, marking a significant leap in social engineering [...]
Urgent Alert: Critical WatchGuard Vulnerability Exposes Firebox Devices to Remote Code Execution A severe security vulnerability has surfaced within WatchGuard’s Firebox firewalls, posing a [...]
Unmasking XillenStealer: A Python Menace Targeting Windows Users In the evolving landscape of cyber threats, the emergence of new information stealers is a constant [...]
Security Operations Centers (SOCs) face an uphill battle. The sheer volume of security alerts, a persistent shortage of skilled cybersecurity professionals, and the ever-evolving [...]
A Critical Flaw in Greenshot: Unpacking the Local Code Execution Vulnerability A widely used, open-source screenshot utility for Windows, Greenshot, has been identified with [...]
The digital threat landscape is in constant flux, with new and evolving tools emerging to challenge even the most robust security postures. A prime [...]
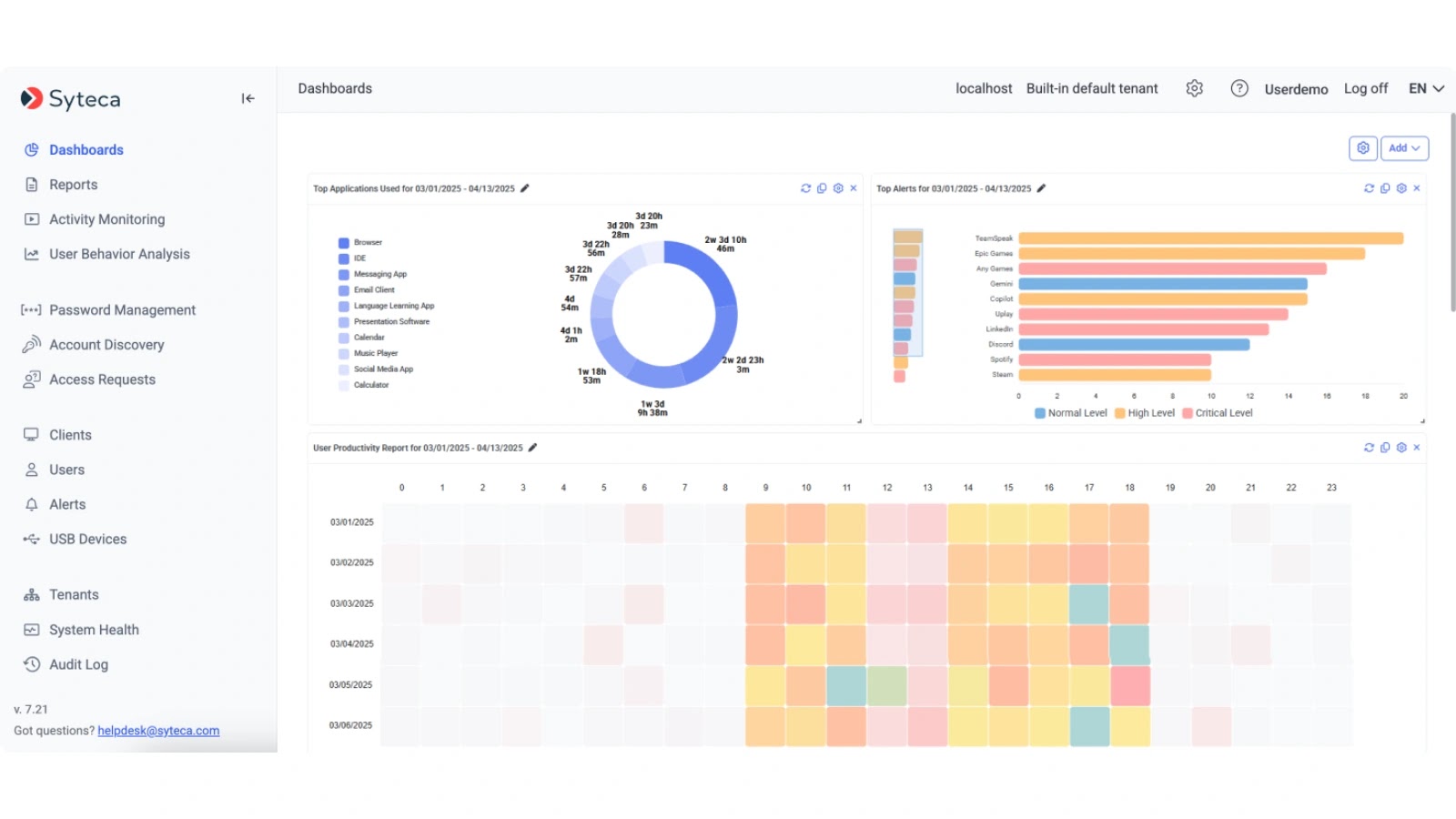
As organizations navigate the complex landscape of digital transformation, the challenge of securing sensitive data and mitigating insider risks intensifies. Breaches originating from within are [...]
The Shifting Sands of Cybercrime: When Adtech Becomes an Attack Vector The digital advertising ecosystem, a complex and often opaque network designed to connect [...]
The Unyielding Shield: Top 10 Next-Generation Firewall (NGFW) Providers in 2025 The digital landscape of 2025 is a battlefield, not a playground. As cyber threats [...]
Navigating the Evolving Threat Landscape: Why DAST is Crucial in 2025 The digital realm expands relentlessly, and with it, the attack surface for web [...]