—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Google Chrome for Desktop Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Gitlab Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected GitLab versions prior [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in Palo Alto Networks Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected Palo [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Apache Tomcat Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Apache Tomcat [...]
Fortinet FortiSandbox: The Ultimate Duo Against Zero-Day Threat Protection and Fortigate Analysis In an era where cyber threats evolve at an alarming pace, safeguarding your [...]
A critical alarm has been raised in the cybersecurity community: the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding [...]
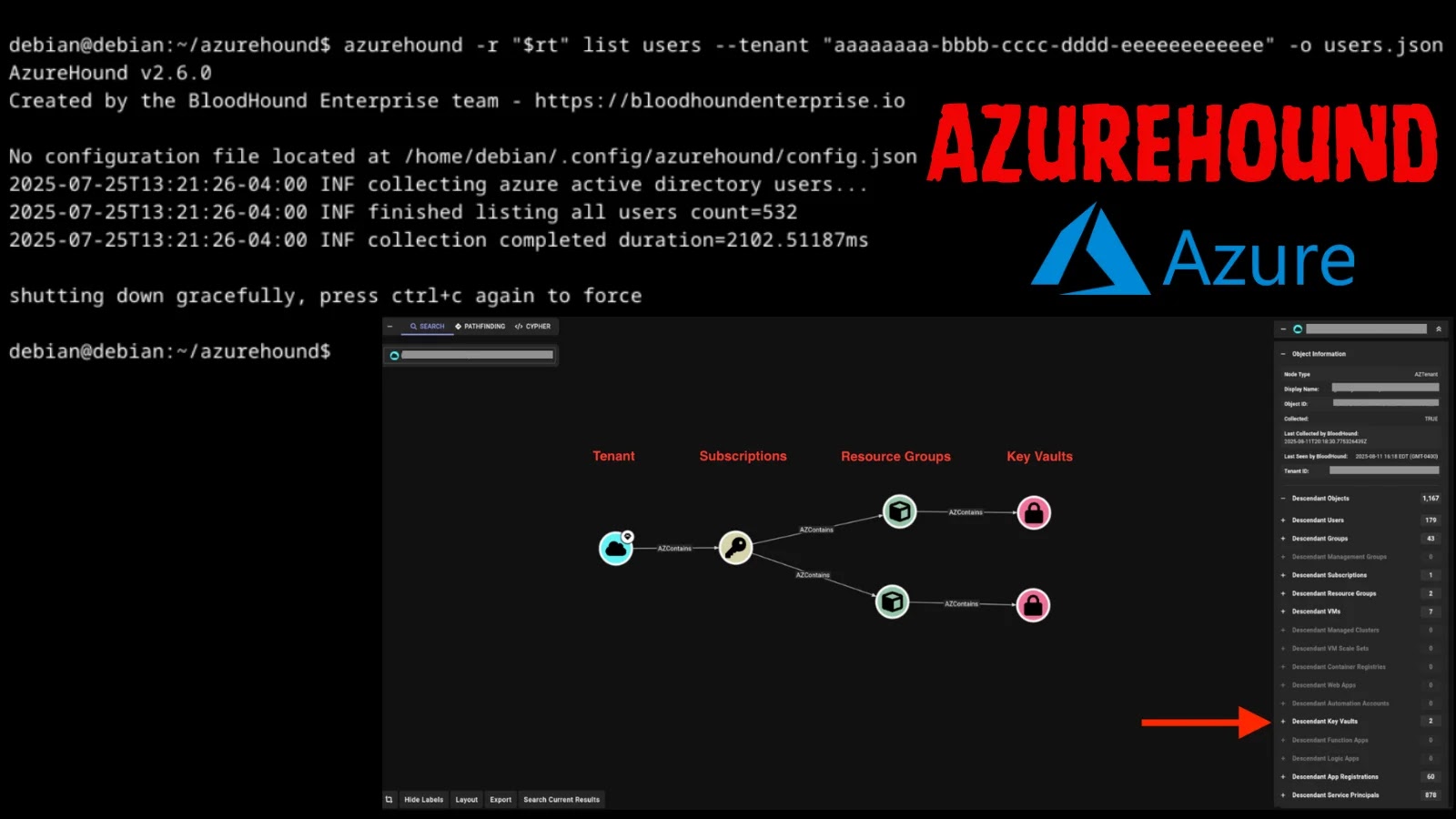
The Double-Edged Sword: When AzureHound Turns Malicious Azure and Entra ID environments are critical to modern enterprises, housing sensitive data and controlling access to [...]
The digital landscape is a constant battleground, and sophisticated threat actors continually refine their tactics. A recent alarming development involves a coordinated multilingual phishing campaign [...]
In an era where digital conversations are increasingly intimate and essential, securing our chat histories has become a paramount concern. WhatsApp, a ubiquitous messaging [...]
A Digital Earthquake: The Great Firewall Falls In an unprecedented cybersecurity incident that reverberated across the globe, September 2025 witnessed a seismic event: a [...]