The Critical Threat: BIND 9 DNS Poisoning Exploit Now Public The digital landscape just became a little more perilous for countless organizations. A public [...]
In the intricate landscape of global cybersecurity, the continued operation of unsupported software often signals a ticking time bomb. This stark reality is particularly [...]
The landscape of software supply chain security is under constant siege, and a recent development in the npm ecosystem has cast a stark light [...]
The cloud, a ubiquitous foundation for modern digital infrastructure, promises unparalleled scalability and reliability. Yet, even the most robust platforms are not immune to operational [...]
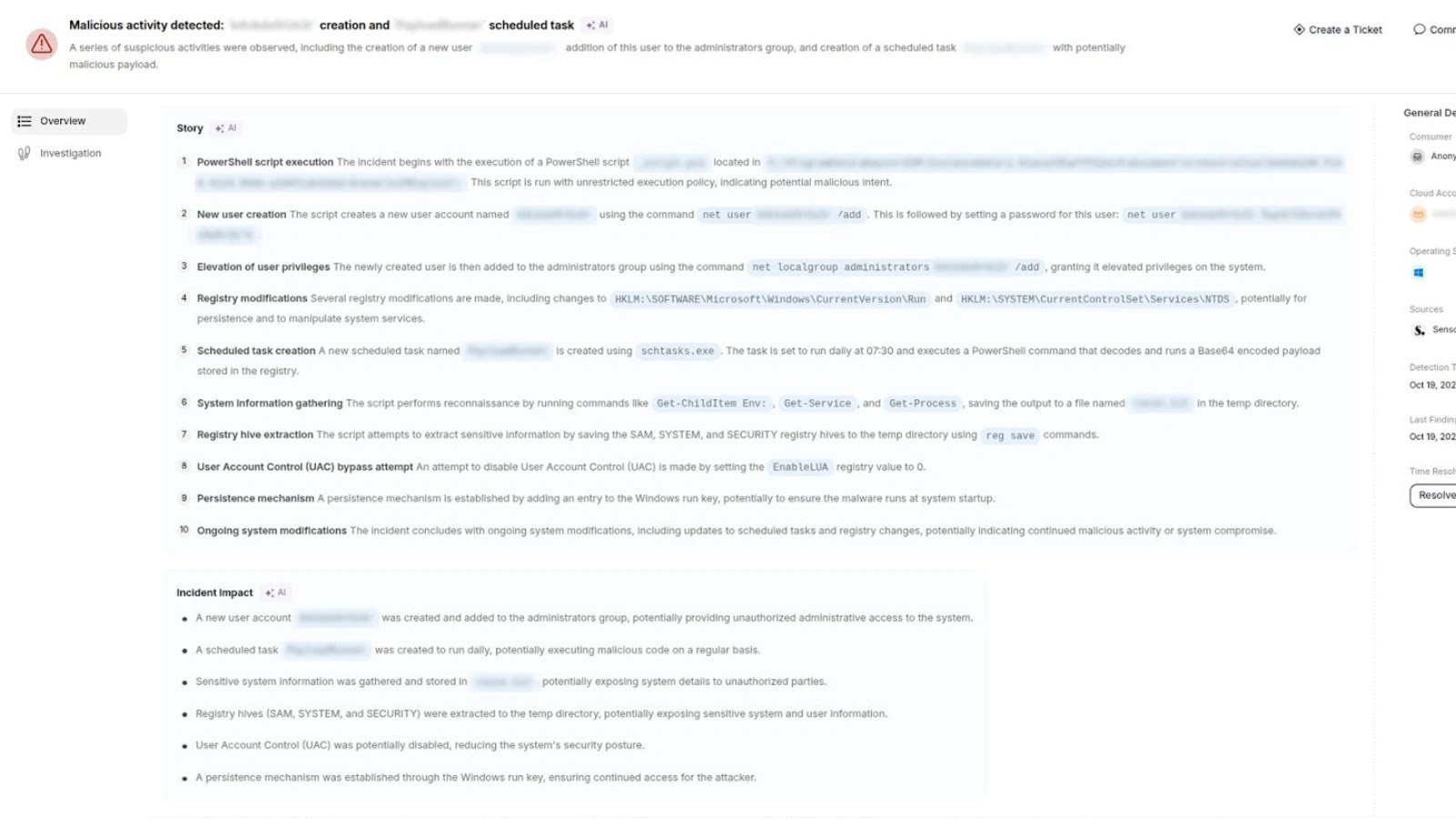
The Expanding Frontier of Cloud Security: Sweet Security Brings Runtime-CNAPP Power to Windows Cloud environments are the backbone of modern enterprise operations, and Windows [...]
The digital landscape is once again highlighting the critical importance of vigilant cybersecurity. A significant cross-site scripting (XSS) vulnerability has been uncovered within the highly [...]
The Rise of Hikvision Exploiter: A Critical Threat to IP Camera Security The security landscape for Internet Protocol (IP) cameras has taken a concerning turn [...]
Imagine your digital lifeline suddenly severed. For organizations worldwide, this became a stark reality on October 29, 2025, when a significant Domain Name System (DNS) [...]
TEE.fail: A Groundbreaking Attack Exposing Vulnerabilities in Modern Trusted Execution Environments The landscape of cybersecurity is perpetually shifting, and new research consistently pushes the [...]
The Silent Heist: How Fake Investment Platforms Are Stealing Your Digital Life The digital financial landscape, while offering unprecedented accessibility, has become a fertile [...]