The New Gentlemen’s RaaS: A Cross-Platform Ransomware Threat Emerges The cybersecurity landscape has once again shifted, demanding heightened attention from IT professionals and security [...]
The digital landscape is a minefield of potential vulnerabilities, where a single misconfiguration can expose vast quantities of sensitive data. Even organizations with seemingly [...]
Weaponizing Justice: PureHVNC RAT Delivered Through Deceptive Judicial Documents A disturbing trend has emerged in the digital threat landscape, where cybercriminals are cloaking malicious [...]
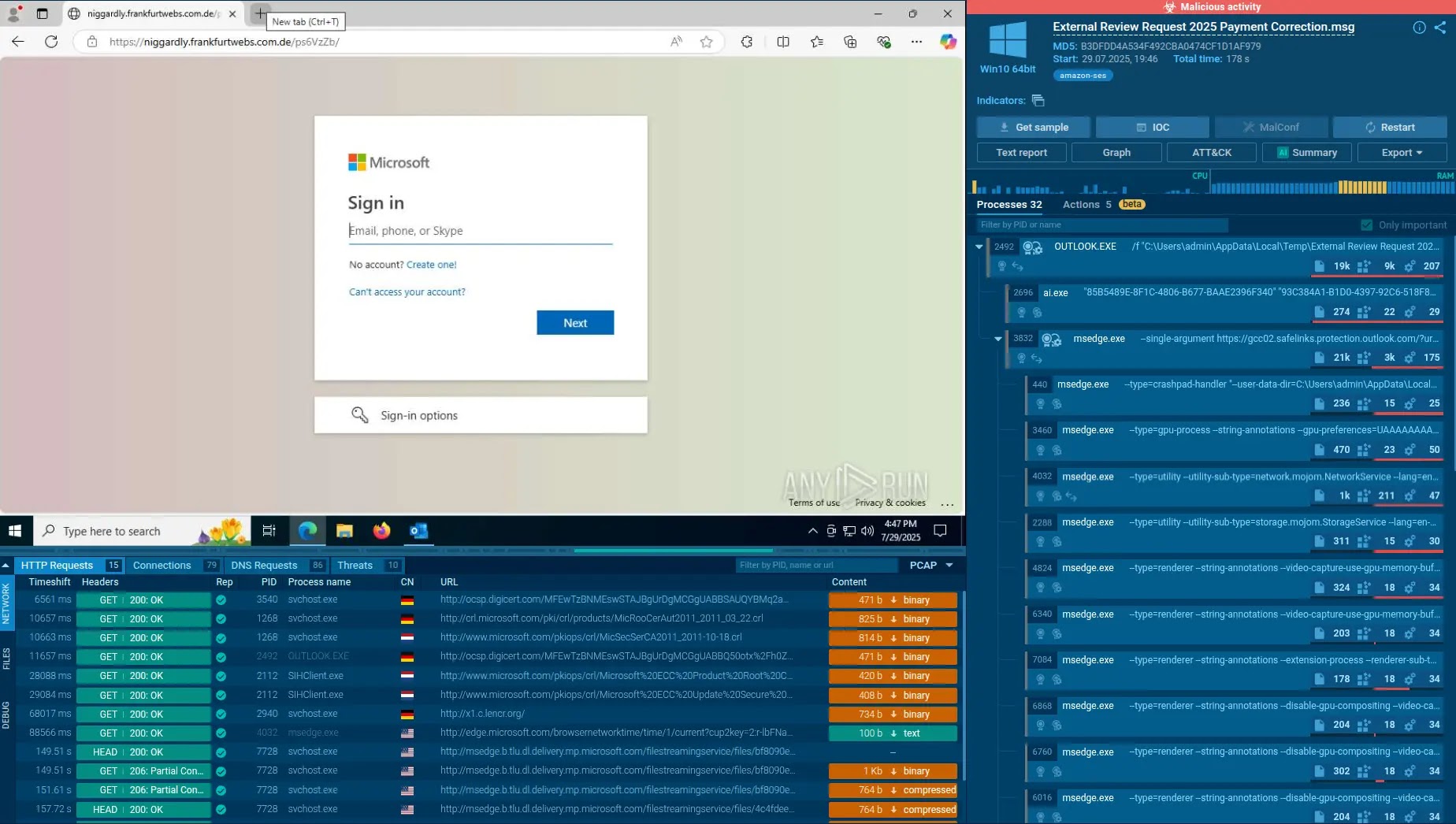
The digital landscape is a constant battleground, and even the most seasoned defenders can find themselves outmaneuvered by novel attack vectors. Recent insights from cybersecurity [...]
Unmasking the Stealth: Russian Hackers’ Living-Off-the-Land Tactics Against Government Entities The digital battleground is constantly shifting, and in its latest iteration, Ukrainian government organizations [...]
Organizations worldwide face a relentless barrage of cyber threats, and staying ahead of sophisticated attackers requires constant vigilance and actionable intelligence. In a critical [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Use-after-free Vulnerability in Mozilla Firefox Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Mozilla Firefox [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Red Hat JBoss Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Red [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Remote Code Execution Vulnerability in Windows Server Update Service (WSUS) Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: [...]
A disturbing report has emerged from the dark web, sending ripples of concern through the financial sector. A threat actor has publicly claimed responsibility for [...]