The digital defense perimeter of government entities is under constant siege, a truth starkly reinforced by the latest malicious campaign orchestrated by the notorious cyber [...]
A silent threat often lurks behind the scenes of critical infrastructure. Recently, Microsoft brought to light a significant vulnerability within ASP.NET Core that could [...]
A chilling disclosure from the recent TyphoonPWN 2025 conference has sent ripples through the Linux community: a critical kernel vulnerability in Ubuntu. This flaw allows [...]
The digital landscape demands robust defenses, and for many organizations, open-source solutions provide a powerful, flexible, and cost-effective answer. Among these, the IPFire firewall stands [...]
The digital landscape is in constant flux, and platform evolutions often bring subtle yet significant changes that demand user attention. For millions of users, [...]
In the constant tug-of-war between cyber defenders and malicious actors, a new and unsettling threat has emerged, specifically targeting users in Brazil. The Water Saci [...]
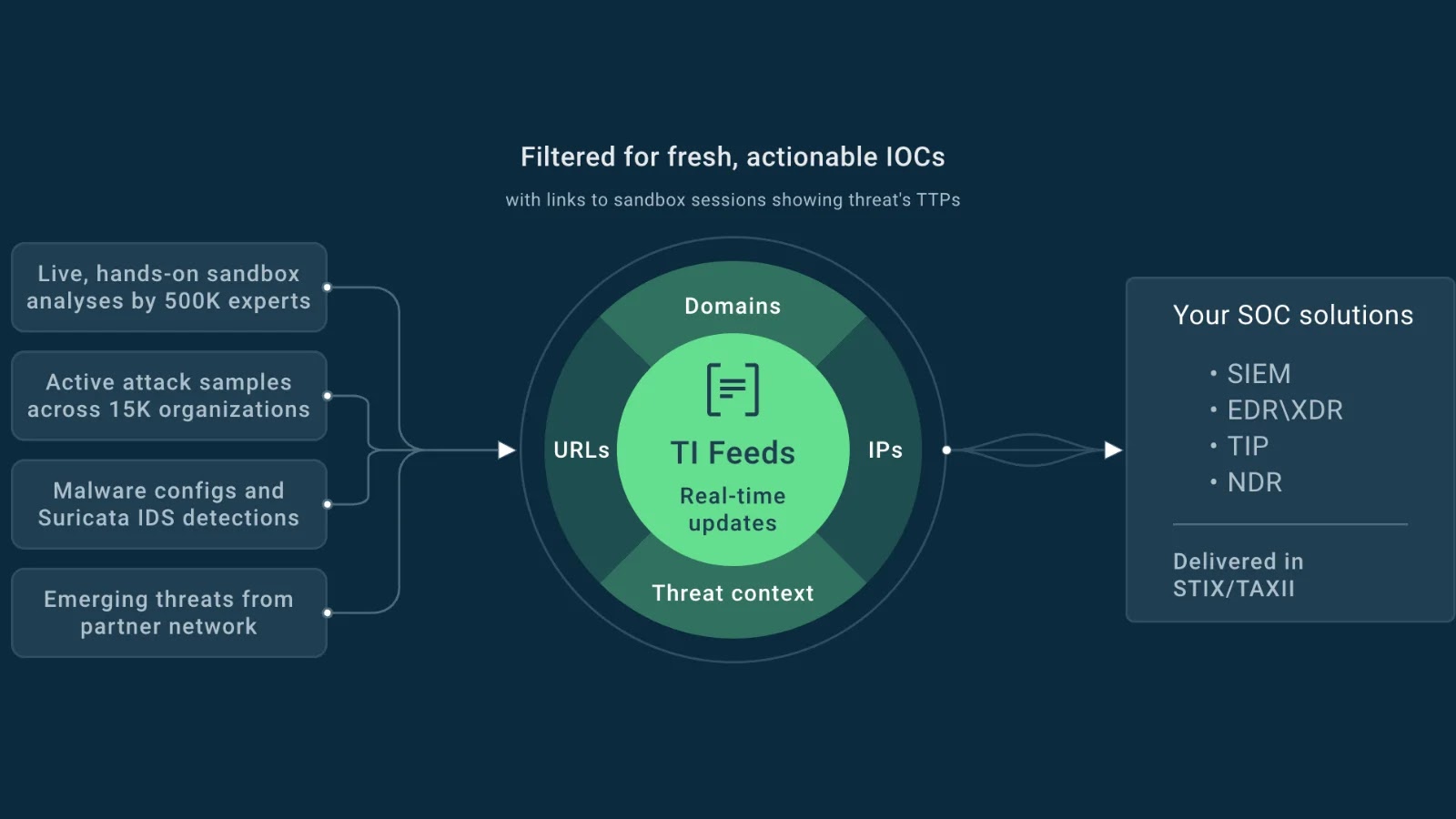
The Relentless Evolution of Malware Threats Organizations today grapple with an unprecedented surge in sophisticated malware attacks. Ransomware cripples critical infrastructure, phishing campaigns compromise [...]
Browser extensions have revolutionized how we interact with the web, offering everything from ad blocking to productivity enhancements. However, their pervasive access to user data [...]
In the constant battle to secure digital assets, a new threat has emerged on the radar: a critical Remote Code Execution (RCE) vulnerability in XWiki, [...]
BlueNoroff’s Evolving Threat: Targeting Web3 Executives with Sophisticated Infiltration The cybersecurity landscape faces a persistent and evolving threat from groups like BlueNoroff, also known [...]