Unmasking the Qilin RaaS Threat: The Korean Leaks Campaign and MSP Breaches The digital landscape is a constant battleground, and recent events highlight the [...]
The digital landscape is under constant siege, and supply chain attacks have emerged as one of the most insidious threats. Developers, relying on open-source [...]
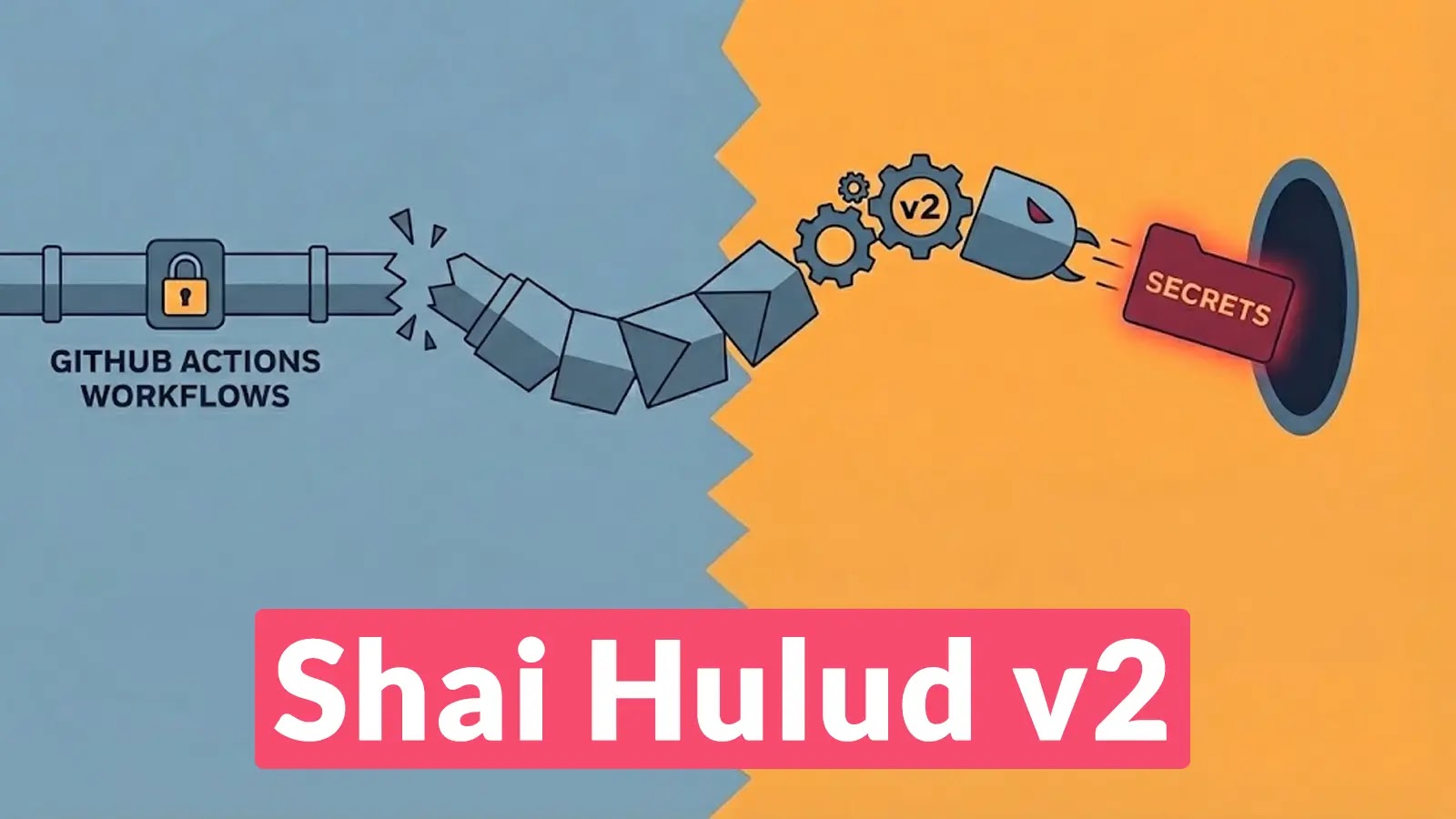
The digital supply chain is once again under a sophisticated attack, as a cunning malware campaign, dubbed “Shai Hulud v2,” emerges. This advanced threat [...]
One Identity Safeguard: A Visionary in the 2025 Gartner Magic Quadrant for PAM Privileged Access Management (PAM) is not merely a security control; it’s [...]
The Silent Threat: Abandoned iCalendar Domains Posing Risk to Millions Digital calendars have become an indispensable cornerstone of both our personal and professional lives. [...]
The Silent Threat: How Legacy Python Code Opens Doors to Domain Takeovers In the fast-paced world of software development, where new frameworks and libraries [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in NVIDIA Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: High Software Affected NVIDIA [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Remote Code Execution Vulnerability in Oracle Identity Manager Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Privilege Escalation Vulnerability in ASUS System Control Interface Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Component [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in SonicWall Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: High Software Affected · [...]