—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Cross-Site Request Forgery Vulnerability in Acquit Content Hub Module of Drupal Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity [...]
Unmasking the Lies-in-the-Loop Attack: When AI Safety Backfires Artificial intelligence (AI) has rapidly become an indispensable tool in software development, offering incredible efficiency and automation. [...]
The Sneaky Threat: How Phishing Tools Exploit OAuth Device Code for M365 Access Microsoft 365 (M365) accounts are a prime target for cybercriminals, and a [...]
A critical alert has been issued for users of the Exim mail server. Recent discoveries by security researchers at the National Institute of Standards and [...]
Using Configure Access Control List (ACLs) on Switches for Traffic Filtering – (ACL) Cisco In the realm of network security, Access Control Lists (ACLs) stand [...]
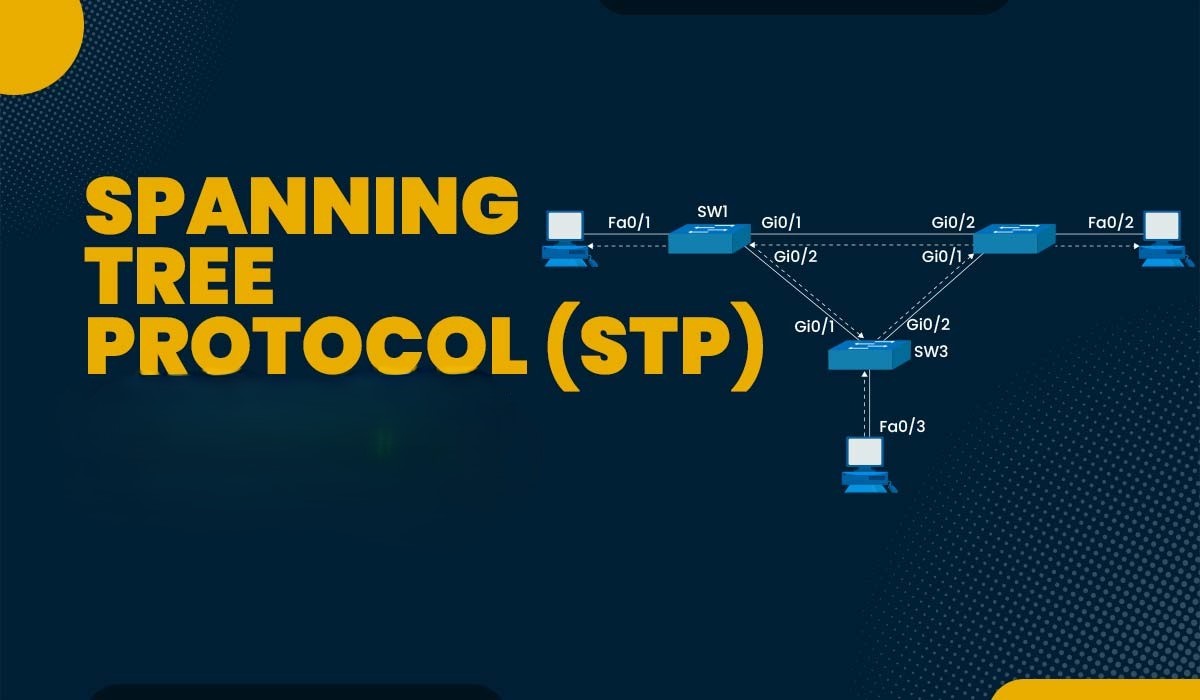
Cybersecurity Implications of STP Security Misconfigurations and Vulnerability Protocol In today’s complex network environments, the Spanning Tree Protocol (STP) plays a crucial role in maintaining [...]
Securing Trunk Links in VLAN Environments: Cisco Network Trunking and VLANs Port Best Practices In today’s complex network environments, securing trunk links is crucial for [...]
Urgent Warning: 125,000 WatchGuard Firebox Devices Exposed to Critical RCE Vulnerability A significant cybersecurity threat has emerged, potentially impacting tens of thousands of organizations globally. [...]
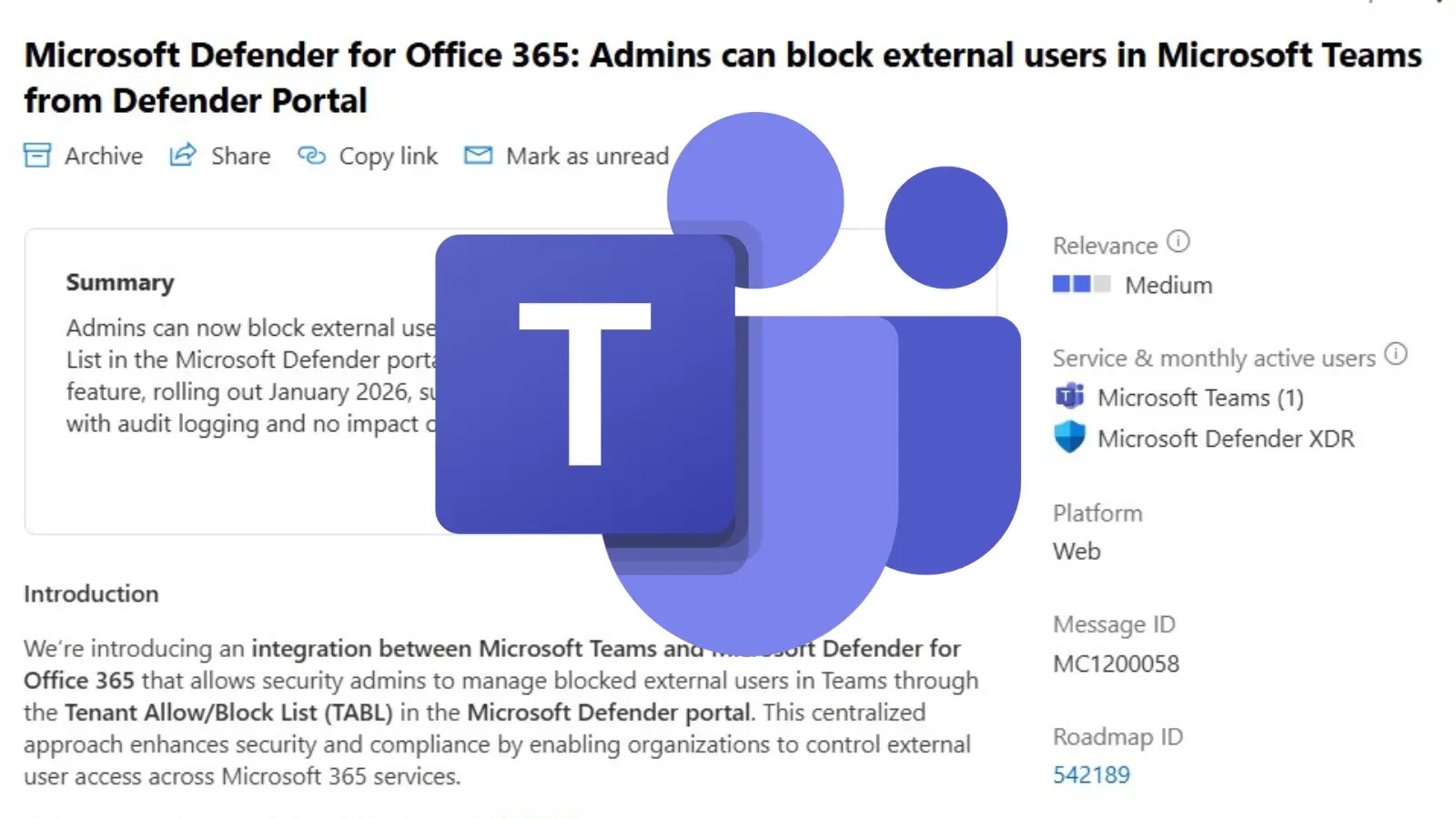
The security landscape for collaboration platforms like Microsoft Teams is constantly evolving, demanding more robust controls over external interactions. For organizations heavily reliant on Teams, [...]
Cybersecurity’s front lines are shifting, and a disturbing new trend demands our immediate attention. Threat actors are increasingly abandoning traditional, high-effort attack vectors in [...]