The year is 2026, and your digital footprint is no longer a mere collection of online activities; it’s a rapidly expanding attack surface. Every [...]
A critical security vulnerability has surfaced within Check Point’s Harmony SASE (Secure Access Service Edge) Windows client software, posing a significant risk to organizations utilizing [...]
SoundCloud Data Breach: Unpacking the Exposure of 29.8 Million User Accounts In an era where digital footprints are increasingly extensive, the security of personal data [...]
ZAP JavaScript Engine Memory Leak Undermines Active Scanning Capabilities The Zed Attack Proxy (ZAP) project, a cornerstone open-source web application security scanner, has recently brought [...]
A silent threat has emerged from the shadows, casting a long and concerning shadow over the security landscape. A critical zero-day vulnerability in the Gemini [...]
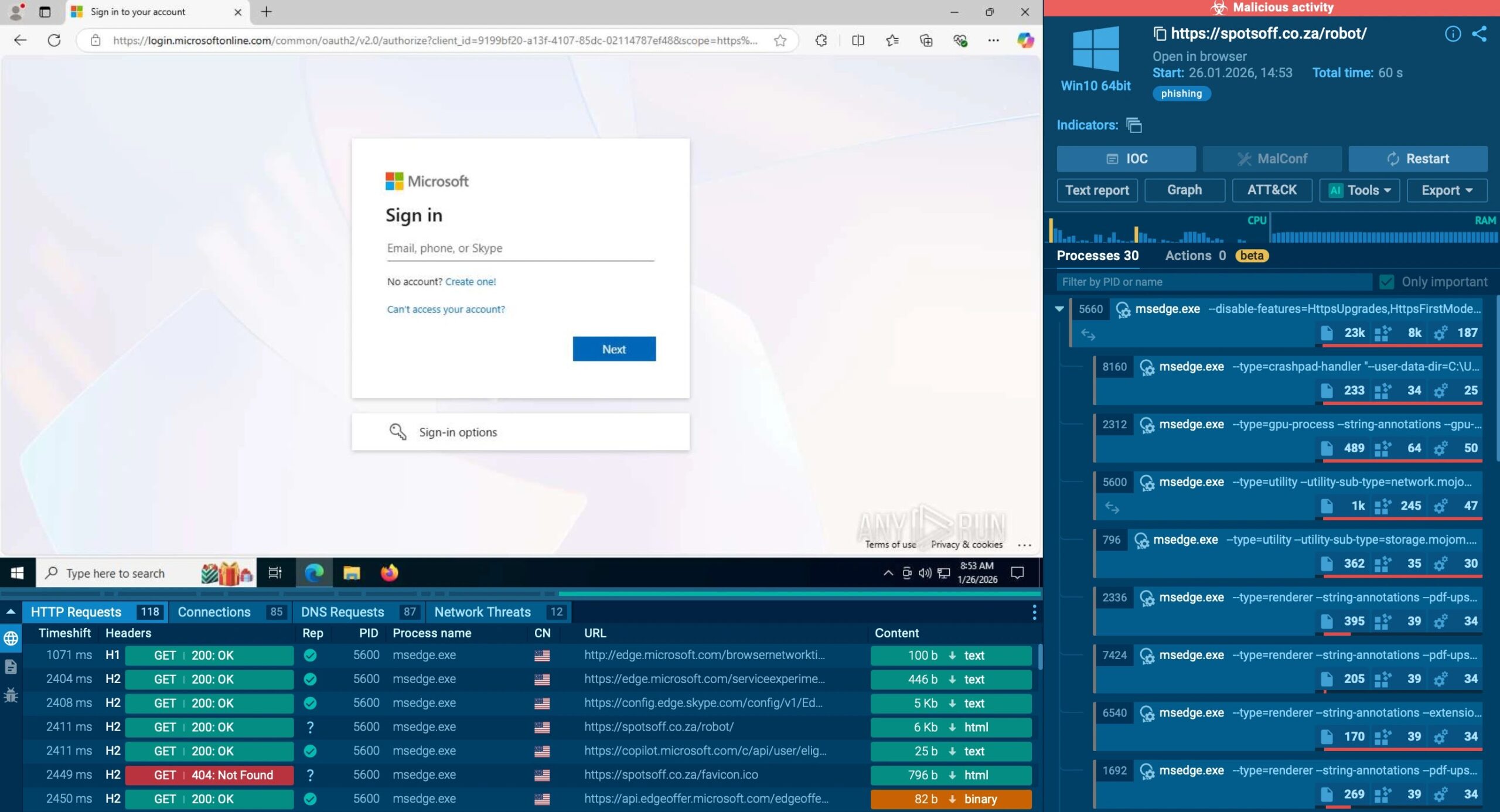
The Deceptive Thread: When Legitimate Enterprise Emails Become Phishing Lures Imagine a critical business discussion unfolding in your inbox, complete with trusted colleagues and familiar [...]
TP-Link Archer MR600 v5 Under Threat: Critical Command Injection Vulnerability Revealed In a significant cybersecurity alert, a critical command injection vulnerability has been identified within [...]
The integrity of classified information within government agencies is paramount. So, when news breaks that a top cybersecurity official inadvertently exposed sensitive documents, it sends [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Remote Code Execution Vulnerability in Google Chrome for Desktop Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in HPE Aruba Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Systems Affected HPE [...]