The digital threat landscape never rests, and a recent advisory from the Cybersecurity and Infrastructure Security Agency (CISA) serves as a stark reminder of this [...]
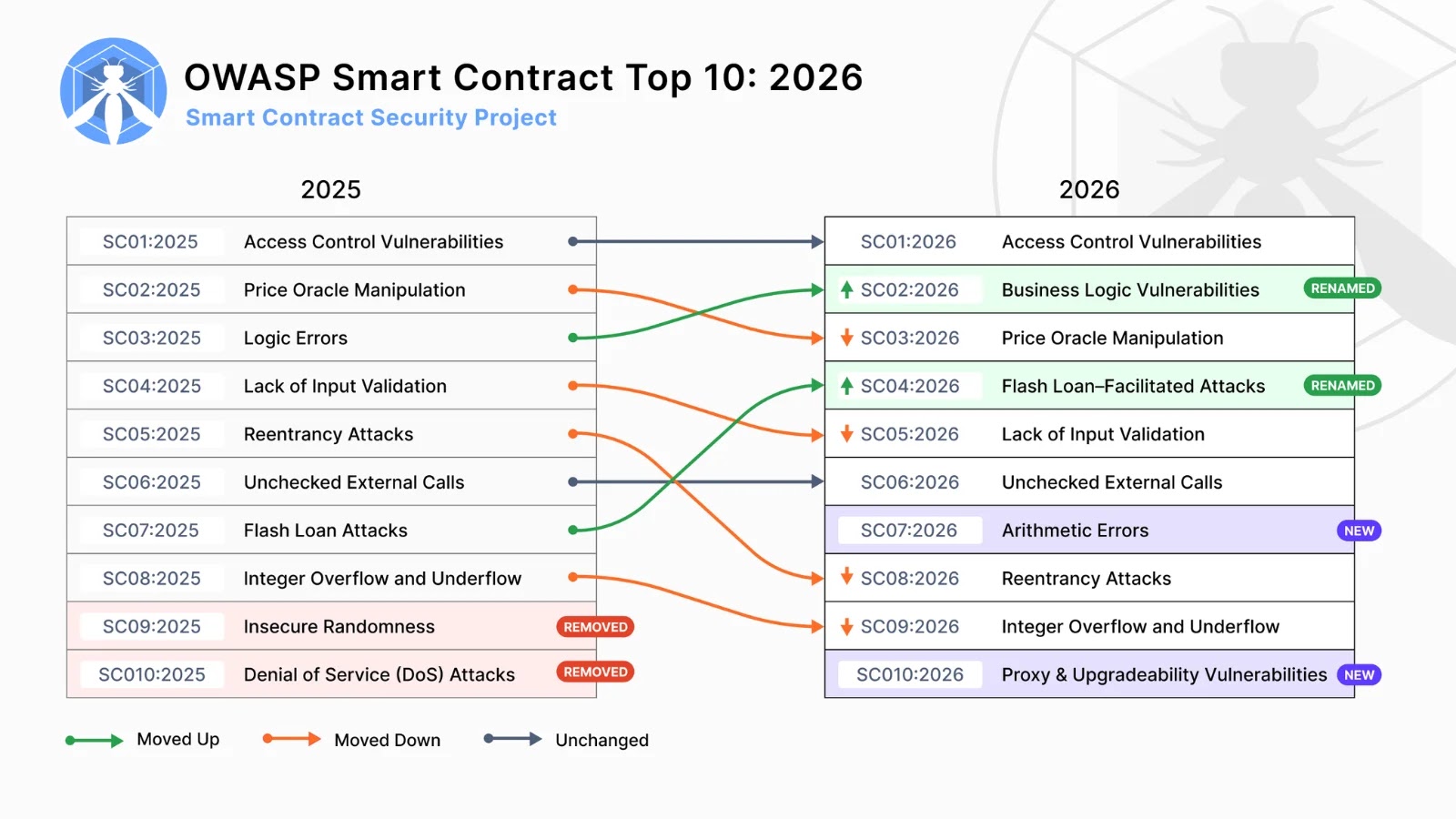
Smart contracts, the self-executing agreements encoded on blockchain technology, are the backbone of Web3 innovation. As their adoption accelerates, so too does the need for [...]
The delicate balance between technological innovation and ethical usage has been brutally exposed as Google recently took decisive action against users of OpenClaw, an open-source [...]
The cryptocurrency landscape remains a high-stakes arena, constantly under assault from sophisticated threat actors. A stark reminder of this enduring threat recently surfaced, marking one [...]
The landscape of cyber threats is constantly shifting, but some tactics remain disturbingly effective. Recently, the cybersecurity community has cast a spotlight on the Silver [...]
A disturbing development has emerged from the clandestine corners of underground hacking forums: threat actors are allegedly peddling a potent exploit capable of crashing WhatsApp [...]
The cybersecurity landscape is in constant flux, with new threats emerging as quickly as new technologies are adopted. A recent development demanding immediate attention is [...]
The internet, a foundational pillar of modern commerce and communication, relies on a complex web of interconnected services. When a key player in this ecosystem [...]
The AI Advantage: How Threat Actors Are Weaponizing Generative AI Against FortiGate Devices The landscape of cyber warfare is undergoing a rapid evolution, with artificial [...]
The rapid integration of Artificial Intelligence (AI) agents into enterprise operations promises unparalleled efficiency and innovation. From automating complex coding tasks to managing sophisticated data [...]