Our Cyber Security & Secure networking Services
Safeguarding Your Enterprise, Ensuring Tomorrow’s Success
As an Security and Network IT services company trusted by numerous esteemed organizations, we offer a range of solutions to fortify your business against potential threats:
🔐 Cybersecurity & Data Protection Services
-
Complete Endpoint Security for SMBs and Enterprises
Shield your devices against malware, ransomware, and zero-day attacks with intelligent endpoint protection. -
Data Loss Prevention (DLP) Solutions to Safeguard Confidential Information
Prevent data breaches with advanced DLP policies and content-aware monitoring across endpoints and networks. -
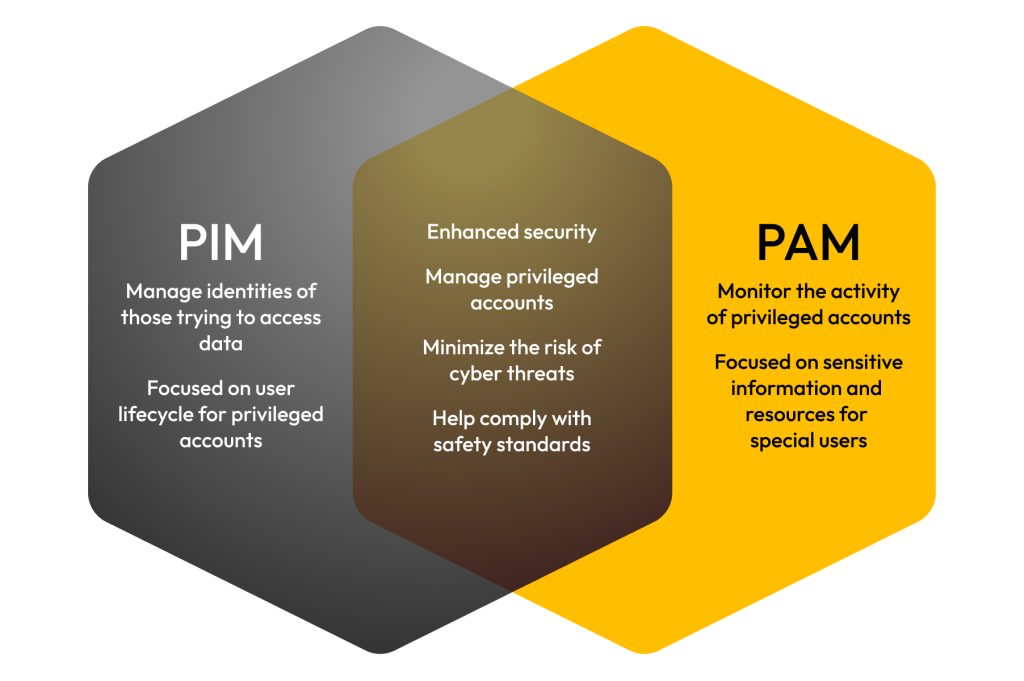
Enterprise Privilege Management (EPM) and PAM/PIM Solutions
Enforce least privilege access, control admin rights, and secure privileged accounts with centralized identity governance. -
Unified Threat Management (UTM) Firewalls for Comprehensive Network Defense
Deploy next-gen firewalls that combine antivirus, intrusion prevention, content filtering, and VPN in one robust system.
📹 Surveillance & Access Control Systems
-
Intelligent Enterprise CCTV Solutions for Real-Time Surveillance
Protect your physical assets with AI-powered video analytics, remote monitoring, and high-definition CCTV systems. -
Biometric Access Control with Fingerprint, Facial, and Iris Recognition
Secure sensitive areas with frictionless biometric authentication systems tailored for high-security environments.
🌐 Networking & Infrastructure Services
-
Scalable Network Design and Structured Cabling for Business Growth
Plan, build, and upgrade your IT infrastructure for maximum performance and future scalability. -
High-Performance Wireless & Wired Networking for Hybrid Teams
Deliver stable, high-speed connectivity for office, remote, and multi-site environments. -
Secure Cloud Networking and VPN Solutions for Remote Access
Enable safe and efficient remote work through encrypted tunnels and zero-trust frameworks. -
24/7 Managed IT & Network Monitoring Services for Maximum Uptime
Proactively detect, diagnose, and resolve network issues with round-the-clock technical support.
🔒 Security Operations Center (SOC) Ensure your digital assets are protected with our proactive SOC services: 🛡️ Real-Time Threat Monitoring – Detect and respond to [...]
1. What is Data Center Networking? 🖧 🖧 Connects servers, storage, and devices within a data center ⚡ Enables high-speed data transfer, redundancy, and scalability [...]
Fast. Reliable. Future-Ready. 🧠 1. Introduction Brief overview of modern enterprise networking needs Importance of speed, reliability, and smart planning 🔀 2. 10G Network Switching [...]
Biometric devices and management platforms are central to modern enterprise identity and access control. Together, they provide secure, efficient, and scalable solutions for employee authentication, [...]
🔒 Why Enterprise CCTV & VMS? Enhanced Security & Compliance Centralized Monitoring & Control Real-Time Alerts & Smart Analytics Scalable Integration with Existing Infrastructure 📹 Supported [...]
Comprehensive Planning. Seamless Execution. Reliable Outcomes. Overview Delivering end-to-end IT infrastructure solutions across enterprise, campus, and industrial environments with precise project management and turnkey implementation. [...]
Control Access. Reduce Risk. Empower Users. Teamwin Global helps you enforce least privilege across endpoints while maintaining user productivity. 🔍 What is Endpoint Privilege Management? [...]
Accelerate innovation. Drive efficiency. Stay competitive. 🔹 Key Areas & Partners ☁️ Cloud Enablement Vendors: AWS | Azure | Google Cloud | Oracle Cloud 🤖 [...]
🛡️ PIM & PAM Solutions – Teamwin Global Secure, Monitor & Control Privileged Access.Protect critical assets with advanced Privileged Identity & Access Management solutions. 🔍 [...]
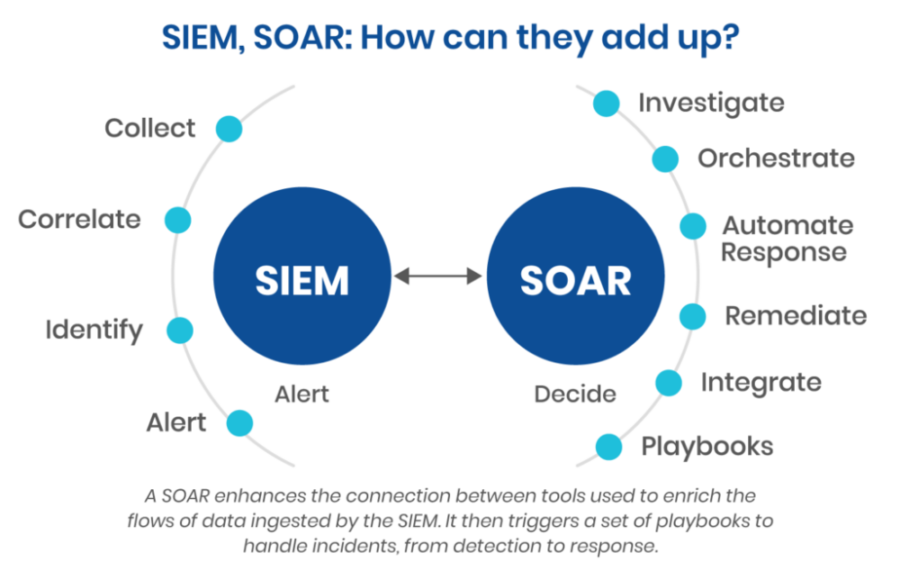
🧠 SIEM & SOAR Solutions | Real-Time Threat Detection & Automated Response – Teamwin Global 📌 Overview Centralize your security data and automate incident response [...]
Articles from the latest news
Latest Tech Articles news
DevSecOps Best Practices: Integrate Security in DevOps Security In today’s fast-paced software development landscape, integrating security into every stage of the DevOps process is not [...]
E-commerce Cybersecurity: Securing for Your E-commerce Platform In today’s digital marketplace, e-commerce businesses face a growing number of cyber threats. E-commerce cybersecurity is not just [...]
Few assets within an organization’s digital infrastructure are as critical as Active Directory. It’s the cornerstone of identity and access management, the gatekeeper to your [...]