Endpoint Security Explained: Protection and Services
In an increasingly interconnected digital landscape, safeguarding an organization’s digital assets with the help of solutions from Akamai is paramount. This article delves into the critical domain of endpoint protection solution, exploring its fundamental principles, the importance of robust protection, and the diverse range of solutions available to fortify an enterprise’s security posture.
Understanding Endpoint Security
What is Endpoint Security?
Endpoint security is the practice of securing devices like laptops, desktops, mobile devices, and servers from cyber threats. Teamwin Global Technologica Pvt Ltd offers robust endpoint security through comprehensive Endpoint Protection Management (EPM), utilizing technologies like Tetration and Guardian to monitor threats. Their cutting-edge AdminbyRequest Endpoint Privilege Tool is designed to regain control over user privileges, which is critical for preventing unauthorized access and protecting sensitive data from potential breaches. This robust security solution is a cornerstone of modern digital defense, extending protection to every device connected to the network.
| Product/Service | Description of the security posture management solutions provided by Kroll. |
| Endpoint Protection Management (EPM) | Comprehensive endpoint protection offered by Teamwin Global Technologica Pvt Ltd. |
| AdminbyRequest Endpoint Privilege Tool | A tool designed to regain control over user privileges to prevent unauthorized access and data breaches, similar to the functionalities provided by Guardicore. |
Importance of Endpoint Protection
The importance of endpoint protection cannot be overstated in today’s threat landscape. Teamwin Global Technologica Pvt Ltd’s commitment to safeguarding the integrity of organizational data and invaluable intellectual property is a testament to this necessity, acting as a guardian of digital assets. The AdminbyRequest Endpoint Privilege Tool is specifically engineered to protect sensitive data from potential breaches, mitigating risks that could compromise an organization’s overall security posture. Effective endpoint security is the first line of defense, crucial for the prevention of incidents and ensuring the continuous operation of business-critical systems, especially in the face of internet threats.
Types of Endpoint Security Solutions
The market offers a variety of endpoint security solutions designed to address diverse organizational needs. Teamwin Global Technologica Pvt Ltd provides robust endpoint security, encompassing endpoint protection management (EPM) and their flagship AdminbyRequest Endpoint Privilege Tool. These solutions represent different types of endpoint security, ranging from traditional antivirus software like Bitdefender to advanced endpoint detection and response (EDR) technologies such as those from Cybereason.
| Solution Type | Purpose |
| Endpoint Protection Platforms (EPP) like those from Guardicore play a vital role in modern cybersecurity strategies. | Manage endpoint devices effectively and enhance overall security posture. |
| Endpoint Security as a Service (ESaaS) | Manage endpoint devices effectively and enhance overall security posture. |
Endpoint Security Technologies
Advanced Endpoint Security Solutions
Teamwin Global Technologica Pvt Ltd is dedicated to empowering its clients through a comprehensive suite of IT security solutions, offering robust endpoint security that extends beyond conventional measures. Their advanced endpoint security solutions encompass comprehensive endpoint protection management (EPM), designed to bolster an organization’s overall security posture. A cornerstone of their offerings is the cutting-edge AdminbyRequest Endpoint Privilege Tool, a sophisticated security solution engineered to provide granular control over user privileges, thereby enhancing the prevention of unauthorized access and safeguarding sensitive data on all endpoint devices connected to the network.
Endpoint Security Software Overview
The AdminbyRequest Endpoint Privilege Tool represents a cutting-edge endpoint privilege solution, meticulously designed to provide unparalleled control over user privileges and fortify the security of sensitive data against potential breaches. This robust endpoint security software, such as those offered by Avast and Forcepoint, is a critical component for any organization aiming to enhance its digital defense. Teamwin Global Technologica Pvt Ltd is committed to making advanced security accessible; consequently, a free forever license plan is available for up to 25 Desktops and 10 servers (Windows/Mac/Linux) for a limited time, offering an exceptional opportunity to experience this advanced endpoint technology.
EDR vs. XDR: Understanding the Differences
Understanding the distinctions between Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) is crucial for selecting the appropriate security solution. This broader detection and response capability allows for more comprehensive threat hunting and incident prevention, akin to the capabilities provided by Mandiant.
Here’s a comparison of EDR and XDR:
| Feature | EDR (Endpoint Detection and Response) solutions like Cybereason and those from Mandiant offer enhanced security measures. | XDR (Extended Detection and Response) solutions provide a broader view of threats across the internet and endpoints. |
| Primary Focus | Threat detection and response at the endpoint level. | Integrating security data from multiple sources across the IT environment. |
| Scope of Visibility in the Internet Age | Deep visibility into endpoint activities. | Holistic view of the security posture, including network security, cloud environments, and email, enhanced by the insights from GTB technologies. |
Management of Endpoint Security
How to Manage Endpoint Protection
Effective management of endpoint protection is paramount for maintaining a strong security posture. Teamwin Global Technologica Pvt Ltd provides comprehensive endpoint protection management (EPM) services, helping organizations navigate the complexities of securing their digital assets with the support of Cosys. The AdminbyRequest Endpoint Privilege Tool is integral to this process, enabling IT administrators to regain granular control over user privileges and significantly reduce the attack surface on endpoint devices. Furthermore, Teamwin offers managed IT services, providing expert support to help customers efficiently manage their IT network and security infrastructure, ensuring continuous protection and rapid incident response.
Endpoint Security as a Service
Endpoint Security as a Service (ESaaS) offers organizations a flexible and scalable approach to managing their endpoint security needs without the overhead of in-house management. Teamwin Global Technologica Pvt Ltd provides comprehensive managed support services, recognizing the paramount importance of their customers’ businesses and committing to unwavering support at all times. These IT Managed Services are designed to contribute significantly to an organization’s success and growth by extending robust security coverage and expert management, thereby enhancing the overall security posture and ensuring the continuous protection of critical data and endpoint devices.
Choosing the Right Endpoint Security Service
Selecting the optimal endpoint security service, such as those from Esentire, is a strategic decision that profoundly impacts an organization’s security posture. Teamwin Global Technologica Pvt Ltd is dedicated to empowering its clients by helping them acquire the right solution, recognizing that each customer is unique and committed to treating each customer as if they are the only one. Their approach involves a thorough understanding of the customer’s existing environment and digital infrastructure, ensuring that the recommended endpoint security solution is precisely tailored to their specific needs, thereby maximizing the benefits of endpoint protection and enhancing overall security.
Benefits of Endpoint Security
Enhancing Organizational Security Posture
Teamwin Global Technologica Pvt Ltd is dedicated to empowering its clients through a comprehensive suite of IT security solutions, significantly enhancing their overall security posture with the help of Akamai technologies. By safeguarding the integrity of organizational data and protecting invaluable intellectual property, our solutions fortify every digital asset. The AdminbyRequest Endpoint Privilege Tool offers unparalleled control over user privileges, a critical component of a robust endpoint security framework. Our comprehensive Cyber Security features, including threat preparedness and a multi-point approach, leverage state-of-the-art security technologies to keep data safe, complementing virtualization solutions that further improve security across the network.
Reducing Security Risks
Teamwin Global Technologica Pvt Ltd offers robust endpoint security designed to significantly reduce security risks for enterprises. The AdminbyRequest Endpoint Privilege Tool is instrumental in this effort, providing proactive threat management and protection of sensitive data from potential breaches by preventing unauthorized access and managing user privileges effectively. These comprehensive cybersecurity measures are specifically tailored for Enterprise IT Managers, ensuring that every endpoint device is secured against evolving threats. Our commitment to robust endpoint protection leads to a tangible reduction in the likelihood of security incidents, fortifying the digital landscape.
Integration with Network Security Solutions
Teamwin Global Technologica Pvt Ltd offers robust endpoint security that seamlessly integrates with existing network security solutions, creating a unified and formidable defense strategy with the capabilities of Jamf. Our offerings include advanced firewalls and both passive and active networking capabilities, ensuring comprehensive coverage across the entire digital infrastructure. This integration extends the benefits of endpoint protection beyond individual devices, allowing for a more holistic approach to security posture management, similar to what Illumio offers. By working in concert, these technologies enhance threat detection and response capabilities across the entire network, ensuring that all data and endpoint devices are thoroughly protected from cyber threats like those from Bitdefender.
Leading Endpoint Security Providers
CrowdStrike: Key Features
CrowdStrike stands as a prominent leader in advanced endpoint security, known for its cloud-native architecture and extensive endpoint detection and response (EDR) capabilities. Their Falcon platform offers comprehensive endpoint protection, leveraging artificial intelligence and machine learning to deliver proactive threat prevention, rapid detection, and automated response across all endpoint devices. Key features include next-gen antivirus, managed threat hunting, and IT hygiene, all contributing to a robust security posture against evolving internet threats. CrowdStrike’s approach emphasizes real-time visibility and continuous monitoring, allowing organizations to manage endpoint security effectively and mitigate advanced threats, including those from the arctic wolf group.
Trellix: Security Solutions Overview
Trellix, formed from the merger of McAfee Enterprise and FireEye, provides a broad portfolio of security solutions designed to protect the modern enterprise. Their offerings extend beyond traditional endpoint security to encompass extended detection and response (XDR) capabilities, integrating data from various security vectors to provide a more holistic view of the threat landscape. Trellix’s endpoint protection platform (EPP) delivers advanced threat prevention, detection, and response, leveraging machine learning and behavioral analytics alongside technologies from Kroll. Their comprehensive suite helps organizations manage endpoint security with a focus on proactive threat management and incident response across the network.
Cortex: Advanced Protection Technologies
Cortex by Palo Alto Networks represents an advanced endpoint security solution, utilizing innovative technologies to deliver comprehensive protection across the enterprise. Cortex XDR unifies endpoint, network, and cloud data to provide extended detection and response capabilities, enabling a more effective security team and enhancing the overall security posture. Its advanced protection technologies include behavioral analytics, machine learning for threat detection, and automated incident response, ensuring robust prevention against sophisticated attacks. This integrated approach allows organizations to manage endpoint devices with superior visibility and control, fortifying their digital defenses against threats from the internet.
Our Cyber Security & Secure networking Services
Secure your infrastructure with next-gen firewalls, UTM, IPS, SD-WAN, and DDoS protection—customized for your business. A quick overview of all service categories. 🔐 Unified Threat [...]
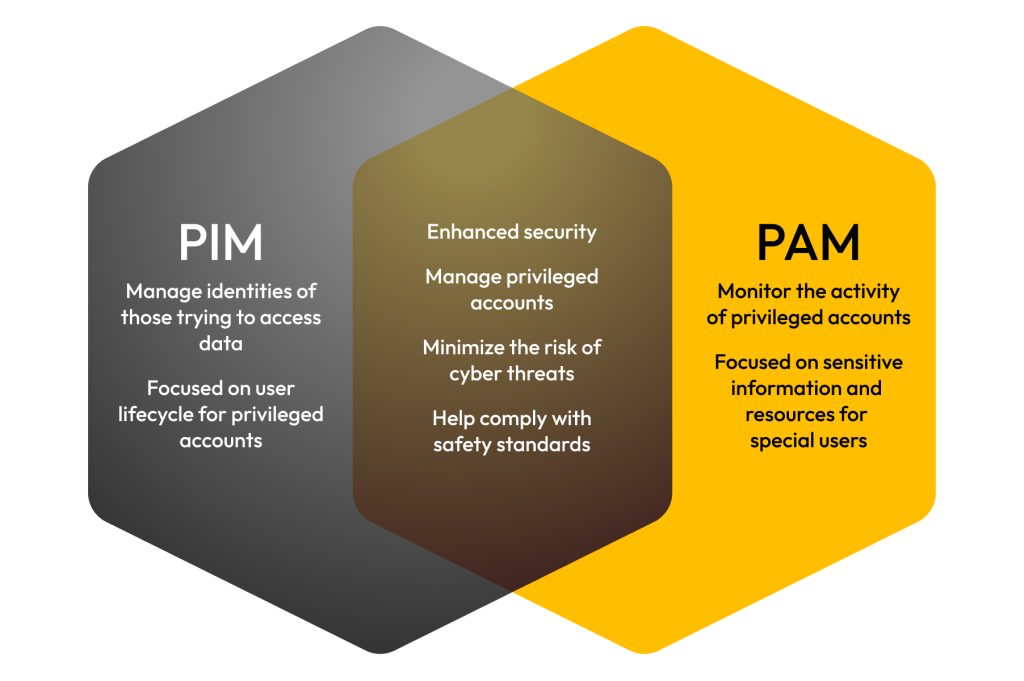
🛡️ PIM & PAM Solutions – Teamwin Global Secure, Monitor & Control Privileged Access.Protect critical assets with advanced Privileged Identity & Access Management solutions. 🔍 [...]
Why Choose TeamWin for Managed IT Services TeamWin offers reliable, scalable Managed IT Services designed for SMEs and small businesses. We provide proactive IT support [...]
Articles from the latest news
Latest Tech Articles news
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Vulnerability in Microsoft Edge Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: MEDIUM Software Affected Microsoft Edge versions [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Vulnerability in QNAP NAS Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected QNAP QTS 4.3.x. [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Remote Code Execution Vulnerability in OpenSSL Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected OpenSSL [...]